OEMs, Tier 1 suppliers, and key stakeholders are struggling with the implementation of automotive cybersecurity systems and processes. In particular, these challenges are most prominent when addressing the need to maintain vehicle security throughout the vehicle lifecycle. With the advent of sophisticated vehicle technology and increasingly complex vehicle architectures, an intricate supply chain, and new regulations to comply with, it has never been more critical to streamline cybersecurity communications.
There is one mutual pain point that the entire ecosystem faces: a lack of harmonization. Harmonizing the activities of the multitude of stakeholders in the industry is a key success factor for effective automotive cybersecurity. As expressed by Andre Weimerskirch, VP Cybersecurity, and Functional Safety of Lear at C2A Security’s industry discussion panel event, “We need to get away from individual templates and sets of requirements. We need to get a harmonized way because [the individual template model] hurts everyone: it hurts car makers, who need to react to ten different ways of doing things, as do the suppliers.”
This sentiment on the importance of harmonization is widely held in the industry, and for good reason. Without harmonized cybersecurity communication and project management, tasks like risk assessment are unnecessarily complicated and time-consuming, and security is jeopardized for drivers and companies alike.
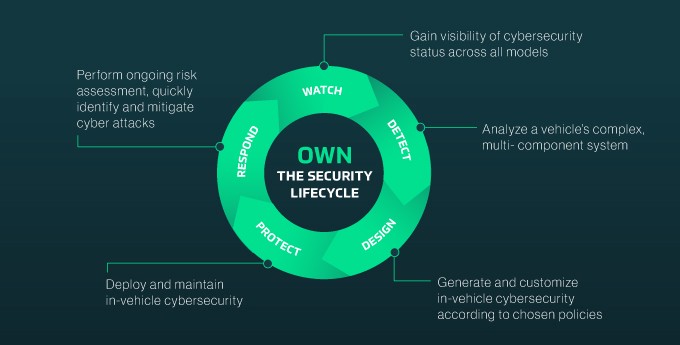
Automotive industry players need to be able to own the cybersecurity lifecycle management process. By “own” I mean developing the capability to address cybersecurity issues throughout the entire vehicle lifecycle freely, thoroughly, quickly and transparently, despite increasingly complex vehicles and a fragmented supply chain. OEMs and Tier 1 suppliers need to be able to understand exactly where vulnerabilities in a vehicle lie, deploy security measures where they are needed, and perform ongoing risk assessments to maintain cybersecurity. Only with this level of ownership can we make rapid cybersecurity improvements and monitor and protect vehicles from design to decommissioning.
Considering risk assessment as an example, automotive players don’t have the ownership that they currently need. According to C2A Security’s recent industry report, 56% of surveyed automotive professionals recognized that it requires at least three weeks for their organizations to complete a comprehensive cybersecurity risk assessment. For modern, connected vehicles, that timeframe is simply not sufficient. Risk assessment is a basic, recurring activity that needs to be performed quickly and on an ongoing basis. The current risk assessment capabilities of most OEMs and suppliers fall short of matching the advanced infrastructure of tomorrow’s CASE (connected, autonomous, shared, electric) vehicles; many face challenges when complying with today’s cybersecurity regulations.
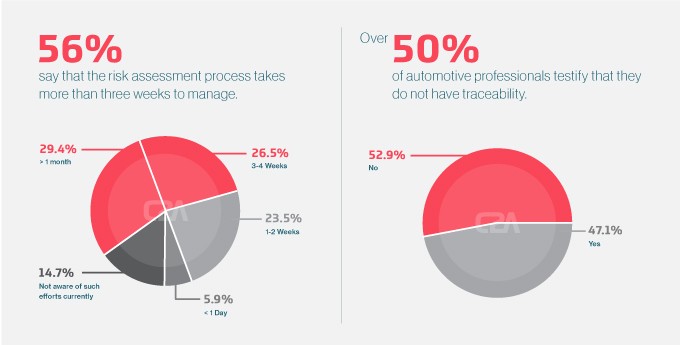
*Based on C2A’s state of the industry report, September 2020
Visibility issues also point to an ownership problem — C2A’s report found that more than half of survey participants do not have traceability from software and hardware BOM to vehicle identification number (VIN) for vehicles on the road today. Visibility is the foundation for ownership: 360-degree oversight of the security makes relevant information easily accessible, and therefore manageable and actionable.
Unfortunately, it’s evident that no single participant in vehicle production and supply chains owns the entire cybersecurity lifecycle management process right now, creating a true challenge for the entire industry to develop the resilience needed to tackle arising automotive cybersecurity challenges.

Harmonization is Essential Missing Link to Achieving Ownership
To achieve the ownership we need, stakeholders must ensure harmonized communication and coordination among all parties involved in automotive cybersecurity. Every link in the supply chain must send and receive consistent updates and information about solutions deployed that are compatible with every team and every process. This level of harmonization will allow the ecosystem to act and react as one force to successfully keep attackers at bay. This harmonized approach is currently lacking in the automotive space. Fifty percent of participants in C2A’s market research report identified a lack of communication and coordination among stakeholders as the biggest impediment to timely cybersecurity risk assessments.
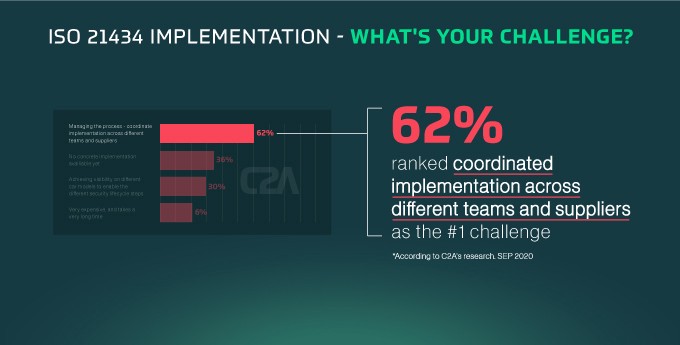
*Based on C2A’s state of the industry report, September 2020
Harmonization is also critical to ensuring that OEMs and suppliers incorporate the new ISO 21434 standard and UNECE WP.29 regulations, which go into effect this year. 62% of study participants agreed that coordination between internal and external teams responsible for implementing different aspects of the standard throughout the vehicle lifecycle is the core challenge for implementing the new standard.
For OEMs, managing communication between all parties involved in vehicle production, both inside and outside their organization and throughout the vehicle lifecycle, is near impossible. All teams and all players involved, such as cybersecurity architects, incident response engineers, integration engineers, system owners, cybersecurity validation engineers, and so on, need the ability to effectively communicate with their own colleagues as well as their counterparts down the supply chain. If achieved, this harmonization could assure effective cybersecurity for the entirety of every individual vehicle’s 20-year lifecycle.
For Tier 1s, collaboration with OEMs on cybersecurity is difficult, vague and frustrating. Cybersecurity requirements set by OEMs sometimes lack clarity and scope, making it hard for Tier 1s to implement, deliver and support OEMs throughout the vehicle lifecycle. Asaf Atzmon, HARMAN International’s Former VP & General Manager of Automotive Cybersecurity explained that “The complexity is huge, we must deal with many OEMs that have their own way of bringing requirements. We also bring requirements to many suppliers; it is like a multi-dimensional matrix.”
Looking at the security lifecycle in its entirety, many activities span over two decades across internal and external teams, such as threat and risk assessment (TARA) at the concept phase, designing and implementing security policies with Tier 1 and Tier 2 vendors, incident reporting, and SOC operation including mitigation of attacks. Owning the cybersecurity lifecycle by ensuring an end-to-end, comprehensive, and structured organizational process is only possible through harmonization among different teams, knowledge, and solutions. The ecosystem must act in symphony to keep attackers at bay.
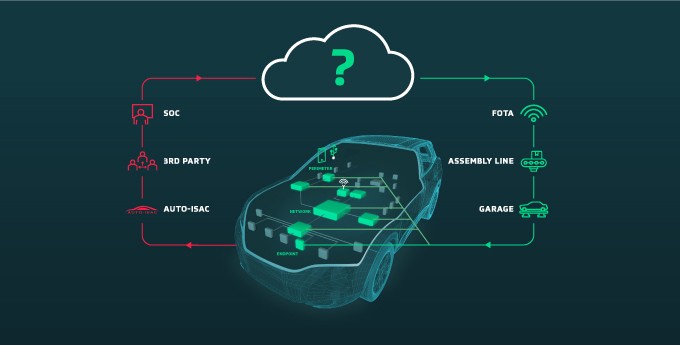
To achieve harmonization and own the security lifecycle, suppliers, OEMs and technology providers need to create a central hub that manages and standardizes all vehicle cybersecurity activities. Such a backbone for cybersecurity would allow OEMs and Tier 1s to communicate with all suppliers, efficiently collaborate, and detect and react to cybersecurity threats in real-time. This is the only way to create a link between the ever-changing reality of cybersecurity challenges and the ability to deploy protection quickly. Different OEMs and Tier 1 manufacturers may utilize their own approaches when trying to grapple with the aforementioned challenges, but as John Krzeszewski, Chair of the Risk Management ISO/SAE 21434 puts it, “Everyone has their own approach, but we all need a common approach.”
Automotive companies should strive to own the entire cybersecurity lifecycle by ensuring an end-to-end, comprehensive, and structured organizational process: harmonizing the entire lifecycle. To meet the rapidly evolving challenges of vehicle cybersecurity, we must empower the entire “village” of manufacturers, parts suppliers and technology providers with the visibility required to meet all cybersecurity needs in a harmonized fashion. Only when we can react as one can we safely prepare for the current and future challenges of advanced mobility.



