
Supply chain management is still playing the second violin. Here is why:
Cybersecurity in the automotive industry has recently been under great progress. The industry has paid attention to the cybersecurity challenges and we can see the outcome in the new standard ISO\SAE 21434 which was published last month.
As we all know, the advanced technology embedded in vehicles creates security challenges especially around connectivity, but the industry faces even more risk with user-driven content that is not under OEM control. Things like application stores and even the car’s internet browser are creating a challenging attack surface for new vulnerabilities.
In addition to the technology risk, the diversity of code and supply chain creates management challenges. Tracing vulnerability to the right line of code and the right supplier in the chain is not simple.
The new ISO\SAE 21434 standard WP.29 155R regulation addresses the processes needed to meet those challenges with an emphasis on risk management across the organization and its supply chain.

What is needed to effectively orchestrate cybersecurity management?
The need for a central cybersecurity management tool that enables visibility across the development lifecycle and across the supply chain is very clear according to WP.29 and it will be a prerequisite for vehicle approvals starting next year.
We can demonstrate the orchestration needs in the three main phases of the vehicle lifecycle as defined by WP.29:
- Development
- Production
- Post-production
Development
Generally speaking, during development the vehicle will move from concept to implementation and then to testing. Orchestrating between OEM and its suppliers at this stage is mainly about security information.
We should expect that at this stage, the interface agreement between OEM and its suppliers will include:
- Item definition and relevant threat analysis from the OEM side
- Requirements to suppliers
- Refined threat analysis from the supplier side and requirement status
- Implementation status and security reports from suppliers including static code analysis, unit testing, and CVE reports.
- System tests and Pen-test results from suppliers
- Relevant standard work packages
The goal of this security information exchange is to allow the OEM to follow its security policy down the pipeline of its suppliers and be sure that the products integrated into the vehicle comply with their standards.
Production
In the production stage, the main challenge other than securing the production sites is key provisioning. At this stage, the orchestration needs to make sure the right keys are being produced and written in the correct places across the supply chain — and securely.
This would involve not only a KMS to manage the keys, but also visibility on production processes of the supply chain, following secure production plans, and test results on keys implementation.
Post Production
When the vehicle hits the road, security operations move to monitoring and incident response. The main orchestration challenge at this stage is shortening the loop time between a security event and a new security mitigation patch is deployed in the vehicle.
Today, the time it takes between a new vulnerability being exposed and an actual fix can take 6 months or more. Orchestration at this stage will concentrate on early warnings to the supply chain through monitoring of potential weaknesses, and coordinate tight collaboration between the OEM and supplier once an event is triggered, including possible temporary fixes and integration of the process with the OEM’s OTA system.
C2A’s AutoSec is the conductor
C2A’s AutoSec is a CSMS (Cybersecurity management system) solution. AutoSec is the first comprehensive cybersecurity lifecycle management platform that empowers OEMs and their suppliers with the visibility, control, and protection required to meet vehicles’ lifelong cybersecurity needs. This unique orchestration layer gives manufacturers unparalleled transparency into the entire cybersecurity lifecycle, enabling streamlined management of each phase — risk assessment, planning, policy creation, monitoring, and enforcement, allowing the true resilience needed to tackle the cybersecurity management challenge.
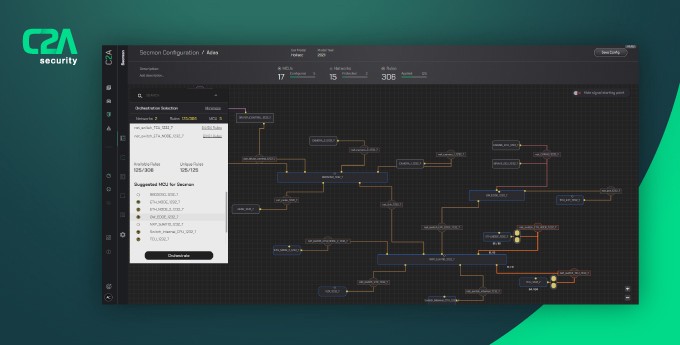
As a centralized cybersecurity hub for the entire industry, AutoSec helps create a dev-ops backbone for cybersecurity management and bridges the gap between all entities down the supply chain, while enabling flexibility for software solutions deployed inside the vehicle and allowing for fast re-configuration and deployment of security policy. AutoSec’s open ecosystem approach creates new opportunities for cross-industry collaboration, enabling security teams to prevent dangerous attacks and prepare for the future of mobility.
It is an honor to have AutoSec recognized as the best orchestration solution of 2021. Winning this award validates C2A’s cybersecurity approach and reinforces the industry’s need for an easy, simple, and effective way to manage the overall security of all connected vehicles. Having an Orchestration tool is essential for the automotive industry to react as one — to safely prepare for the current and future cybersecurity challenge. Finally, the automotive industry can all play on the same note.







