The 626 Mile Road Trip
Ford CEO, Jim Farley, alongside several Ford employees, embarked on a journey from Silicon Valley to Las Vegas in the all-electric F-150 Lightning. This trip provided Jim with a firsthand experience of the challenges associated with driving an electric truck, particularly when faced with a dwindling battery.
During a stop at a charging station in Coalinga, Farley encountered the reality of slow charging speeds that many EV owners often face. Despite charging his truck for 40 minutes using a low-speed charger, he could only restore the battery to 40 percent.
In a video shared on X, he described the process as “pretty challenging” and underscored the significance of fast charging for an efficient customer experience.
Other Potential Key Challenges
Despite the challenges faced by Jim with the charging process during his road trip, there are additional areas of concern that need to be addressed in the EV industry:
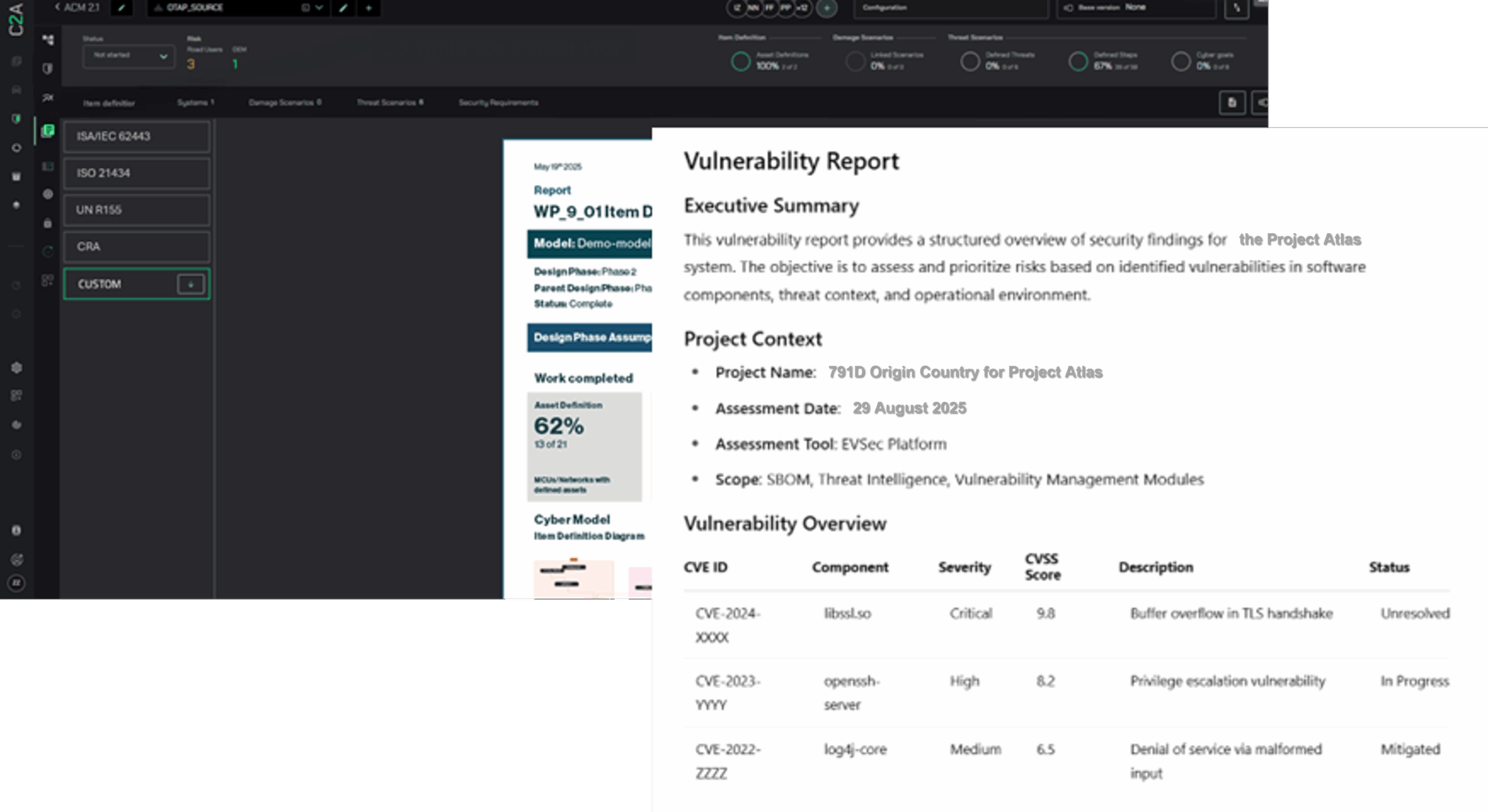
Cyber Threats and Security: Cybersecurity measures are crucial for EV manufacturers and charging network providers. The discovery of critical vulnerabilities in ABB’s ChargerSync Platform last month highlights the need for solid processes that ensure system integrity and user data protection.
Regulation and Quality of Service: The UK has implemented comprehensive cybersecurity regulations for EV infrastructure, contributing to an enhanced charging network and seamless customer experience. However, these types of regulations need to become the norm worldwide. Countries should follow the UK’s lead and China’s rapid progress by establishing improved cybersecurity regulations.
Turn Security into a Business Value Multiplier
C2A Security provides the only mobility-centric DevSecOps platform designed to optimise your risk management efforts. Our advanced approach to automotive cybersecurity empowers companies to deliver secure products and create new software-based revenue streams while staying compliant and adhering to regulations and standards. Try it out by scheduling a demo today.