The automotive industry is at the forefront of innovation, with features like remote keyless entry (RKE) becoming a standard in modern vehicles. However, a recent research paper titled Security Analysis of Remote Keyless Entry Systems (PDF) by Ristenpart et al., exposes significant vulnerabilities in these systems. These findings underscore the critical need to enhance supply chain security through automated DevSecOps tools and context-driven risk management approaches.

In this blog, we’ll summarize the key insights from the paper, highlight the most alarming vulnerabilities, and explore strategies to mitigate these risks—particularly focusing on how secure software development and supply chain monitoring can play a transformative role.
Summary
Ristenpart et al. delve into the architecture and security mechanisms of contemporary RKE systems. By analyzing multiple vehicles and manufacturers, the authors identify design flaws in cryptographic implementations, weaknesses in key management, and susceptibility to over-the-air attacks. These vulnerabilities stem largely from insufficient threat modeling, lack of encryption best practices, and inconsistent supply chain practices.
Their findings reveal that many RKE systems fail to address the evolving threat landscape, leaving vehicles vulnerable to attacks that can compromise user safety, privacy, and brand reputation. The paper stresses the importance of contextual awareness in designing RKE systems, as well as the need for continuous validation across the supply chain to avoid cascading risks.
The Top Vulnerabilities
1. Replay Attacks
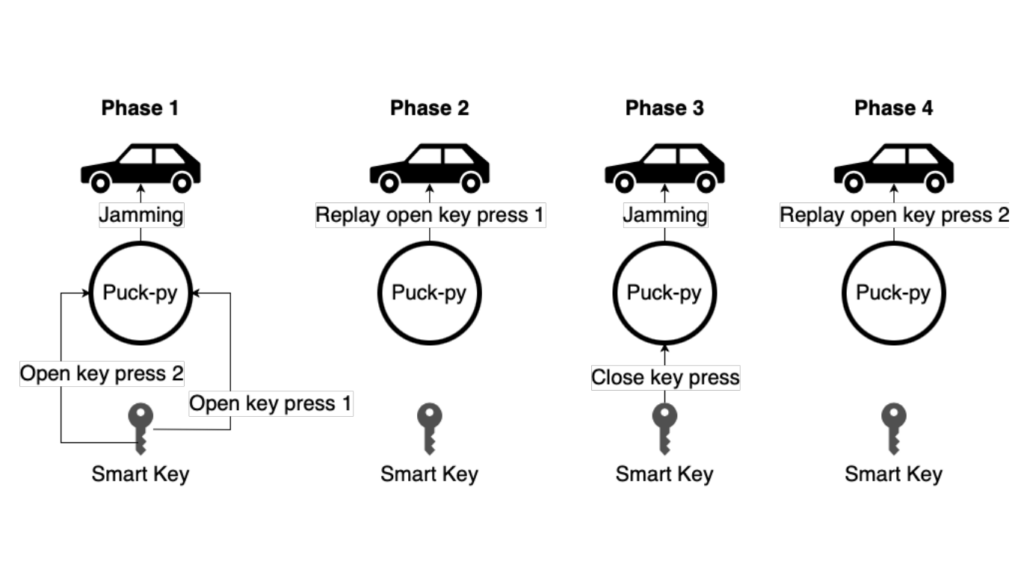
Some RKE systems are vulnerable to replay attacks, where an attacker captures legitimate communication between the key fob and the vehicle and reuses it to unlock or start the car. This issue arises from the improper implementation of rolling code protocols, which are meant to generate unique codes for each interaction but are often inadequately secured.
2. Weak Cryptographic Primitives
The researchers identified that several systems still rely on outdated or poorly implemented cryptographic algorithms. This not only makes them vulnerable to brute force attacks but also simplifies reverse-engineering efforts for attackers.
3. Insecure Supply Chain Components
Many RKE systems use third-party components sourced from the global supply chain, some of which do not adhere to stringent security standards. Attackers can exploit these weak links to inject malware or manipulate firmware during production, leaving vehicles vulnerable from the start.
4. Inadequate Firmware Update Mechanisms
RKE systems often lack robust over-the-air (OTA) update mechanisms. Insecure update processes can allow attackers to distribute malicious firmware, escalating the potential for remote takeovers and data breaches.
Mitigation Strategies
1. Embrace DevSecOps for Secure Development
Integrating DevSecOps principles into the automotive software development lifecycle can significantly reduce vulnerabilities. Automated tools for static and dynamic analysis can detect insecure cryptographic implementations and identify other common coding flaws early. Security testing should extend to third-party components, ensuring every piece of software meets uniform standards.
2. Implement Context-Driven Risk Management
Context-driven risk management emphasizes prioritizing threats based on their likelihood and potential impact. For example, manufacturers can deploy contextual tools to analyze RKE attack vectors based on geographic, supplier, and user behavior data. Such methods can help pinpoint high-risk components or regions and allocate resources accordingly.
3. Harden Supply Chain Security
Supply chain vulnerabilities require a multi-pronged approach:
- SBOMs and Continuous Monitoring: Mandating Software Bills of Materials (SBOMs) for all RKE system components helps track dependencies and identify weak links. Continuous monitoring tools can flag outdated or compromised third-party software in real-time.
- Zero Trust Architectures: Adopting a zero-trust model ensures that all devices and firmware updates are verified before integration or deployment. This can mitigate risks stemming from counterfeit or compromised parts.
4. Enhance OTA Update Protocols
OTA updates must leverage end-to-end encryption and secure boot processes to prevent tampering. Rolling code algorithms should be periodically reviewed and updated to remain resilient against emerging threats. Manufacturers should adopt update frameworks that support both immediate patching and long-term upgradeability.
5. Collaborate Across the Ecosystem
Automotive OEMs, suppliers, and cybersecurity experts need to work collaboratively to establish industry-wide standards for RKE system security. Participating in industry organizations like the Auto-ISAC, ASRG, and adhering to regulations and standards as UN R155, UN R156, CRA, and ISO/SAE 21434 can foster shared responsibility and knowledge sharing across the supply chain.
Conclusion
The vulnerabilities demonstrate that remote keyless entry systems are not merely convenient features but also critical components in automotive cybersecurity. By adopting automated DevSecOps tools, emphasizing context-driven risk management, and securing supply chains, carmakers can potentially mitigate these risks while preserving innovation.
As the threat landscape continues to evolve, the automotive industry must proactively adapt its security practices. The road to secure mobility starts with building resilience at every stage—design, development, deployment, and beyond.
C2A Security’s EVSec Platform empowers software-defined companies to develop more secure products and solutions across the entire mobility ecosystem. From vulnerability management, asset management, analyzing SBOMs, and context-driven risk management, C2A Security helps product teams manage their security posture throughout the product lifecycle.
Automate cybersecurity processes and gain visibility over all assets with the EVSec platform.
Schedule a demo today to learn more.