What is an SBOM and why is it Important?
A Software Bill of Materials (SBOM) is a foundational cybersecurity and compliance artifact that provides a machine-readable inventory of all software components and dependencies, including open-source libraries, packages, licenses, proprietary code, and metadata.
Think of an SBOM as a label of ingredients for software, where each component is listed with specific attributes such as version, origin, author name, and hierarchical relationships to support secure development.
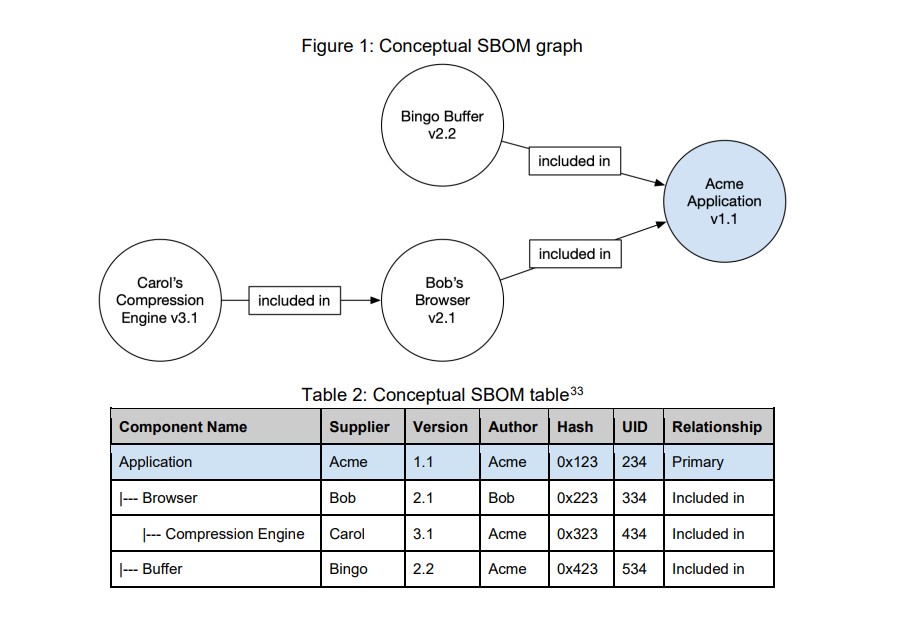
(“Framing Software Component Transparency: Establishing a Common Software Bill of Materials, Third Edition“ Document)
Gartner predicts that over 60% of organizations will adopt SBOMs by the end of this year, up from under 20% in 2022, highlighting their critical role in securing the software supply chain.
SBOMs are no longer a consideration; they are mandatory. Executive Order 14028 requires all vendors to provide SBOM documentation when working with federal agencies, ensuring transparency into software components, third-party dependencies, and potential vulnerabilities to enhance supply chain management security.
For connected medical devices, the widespread use of third-party and open-source software introduces hidden and often unmanaged risks that can directly impact patient safety, system availability, and the confidentiality of sensitive health data. SBOMs provide essential visibility into these components, enabling manufacturers to proactively identify, track, and mitigate security vulnerabilities across the device software supply chain. In regulated healthcare environments, this transparency is not just a best practice—it is becoming a compliance mandate.
An SBOM can provide comprehensive visibility into all software components used within a device, enabling manufacturers to map dependencies between modules that may affect device performance and proactively manage risks to patient data confidentiality.
The Regulatory Push: FDA Requirements and Beyond
The FDA now requires all medical device manufacturers (MDMs) to include a Software Bill of Materials (SBOM) in their premarket submissions for cyber devices. This requirement is formalized under Section 524B of the Federal Food, Drug, and Cosmetic (FD&C) Act, which defines a cyber device as one that includes software, connects to the Internet, and poses potential cybersecurity risks [download the Bill, PDF].
Under this regulation, manufacturers must provide the FDA with a comprehensive and up-to-date SBOM that includes all commercial, open-source, and off-the-shelf software components used in the device. The SBOM must be:
- Maintained and versioned across the full product lifecycle.
- Integrated into both premarket and postmarket cybersecurity planning.
- Aligned with a vulnerability management program capable of identifying, tracking, and remediating security issues over time.
Additionally, manufacturers must disclose any software modifications or updates that impact cybersecurity. This includes patching procedures, component replacements, license changes, or the mitigation of newly discovered vulnerabilities.
Beyond regulatory pressure, the business case is clear: 73% of healthcare organizations report that new FDA cybersecurity requirements and evolving EU regulations influence their procurement decisions. 78% now view SBOM availability as a key factor in vendor selection.
SBOM Use Cases in Medical Devices
Surmodics, a global leader in surface modification technologies for intravascular medical devices, was recovering from a cyber attack in June 2025, when an unauthorized third party accessed critical IT systems and data.
Research showed that 14% of connected medical devices also run an unsupported or end-of-life operating system (OS). An SBOM can help mitigate these risks by providing visibility into all underlying software components, including outdated OS versions, unpatched third-party libraries, and embedded firmware dependencies.
Here are other use cases for medical devices:
- Vulnerability management and VEX (Vulnerability Exploitability eXchange): Vulnerability management in medical devices focuses on full visibility into upstream and downstream components. Upstream components refer to third-party and open-source libraries and operating systems integrated into the device software from external suppliers.
Downstream components include all the software elements and custom code built by the manufacturer that relies on upstream components. If any interconnected components are compromised, it could create a ripple effect throughout the supply chain.
An SBOM and VEX complement each other, providing manufacturers with the tools to assess and manage these risks effectively. SBOMs inventory all components, while VEX complements the SBOM by indicating whether a given vulnerability is exploitable in the device’s context, helping manufacturers prioritize remediation. - License tracking: Software components contain licenses that include copyrights, usage rights, and obligations that, if not properly tracked, could pose legal and intellectual property (IP) risks to MDMs. Open-source libraries may carry restrictive licenses such as GPL, GNU, MIT, and Apache with specific distribution, modification, and usage conditions.
An SBOM catalogs license types across all software components helps maintain traceability for due diligence during FDA audits and supports legal and compliance reviews during regulatory submissions. - Device lifecycle management: An SBOM identifies outdated or deprecated components that may require replacement or patching, while providing manufacturers with continuous visibility into all software components throughout the entire device lifecycle, from design to deployment. An affected component can lead to a software supply chain attack.
An SBOM also reduces supply chain risk by flagging components with a history of compromise, whether attributed to third parties or internal sources. Every component may be traced to an author or supplier, with detailed metadata including version, license, and cryptographic hash. - Developer code reviews and secure supply chain: DevOps and security teams should maintain an open feedback loop for SBOM implementation, where component updates are tracked in real time, and security considerations are integrated early in the SDLC
SBOMs are essential for code reviews to detect risky libraries, deprecated packages, or components with restrictive licenses before they reach production.
SBOMs can also be integrated into CI/CD pipelines to automatically detect transitive dependencies, identify known vulnerabilities, and ensure license compliance, especially when working with open-source software (OSS) repositories, which often contain malicious packages that may be unintentionally installed and remain undetected post-production.
An SBOM provides the needed visibility into every component and its origin, helping developers verify the authenticity of packages.
SBOM Implementation Best Practices
Here are several best practices of SBOM implementation:
- Integrating SBOM generation into DevOps (SPDX / CycloneDX formats to map baseline component information and for data exchange).
- Handling redacted components and proprietary IP.
- Predict growing enforcement and third-party pressure (e.g., hospital procurement standards).
- Urge adoption across various departments, not just for compliance, but for trust, safety, and resilience.
- Tag software components with unique identifiers for traceability across ecosystems.
- Use binary analysis tools for legacy or closed-source components.
- Link SBOM data with asset management systems for full device and component traceability.
- Version-control every SBOM artifact for software component origins
Streamline SBOM Management with C2A Security
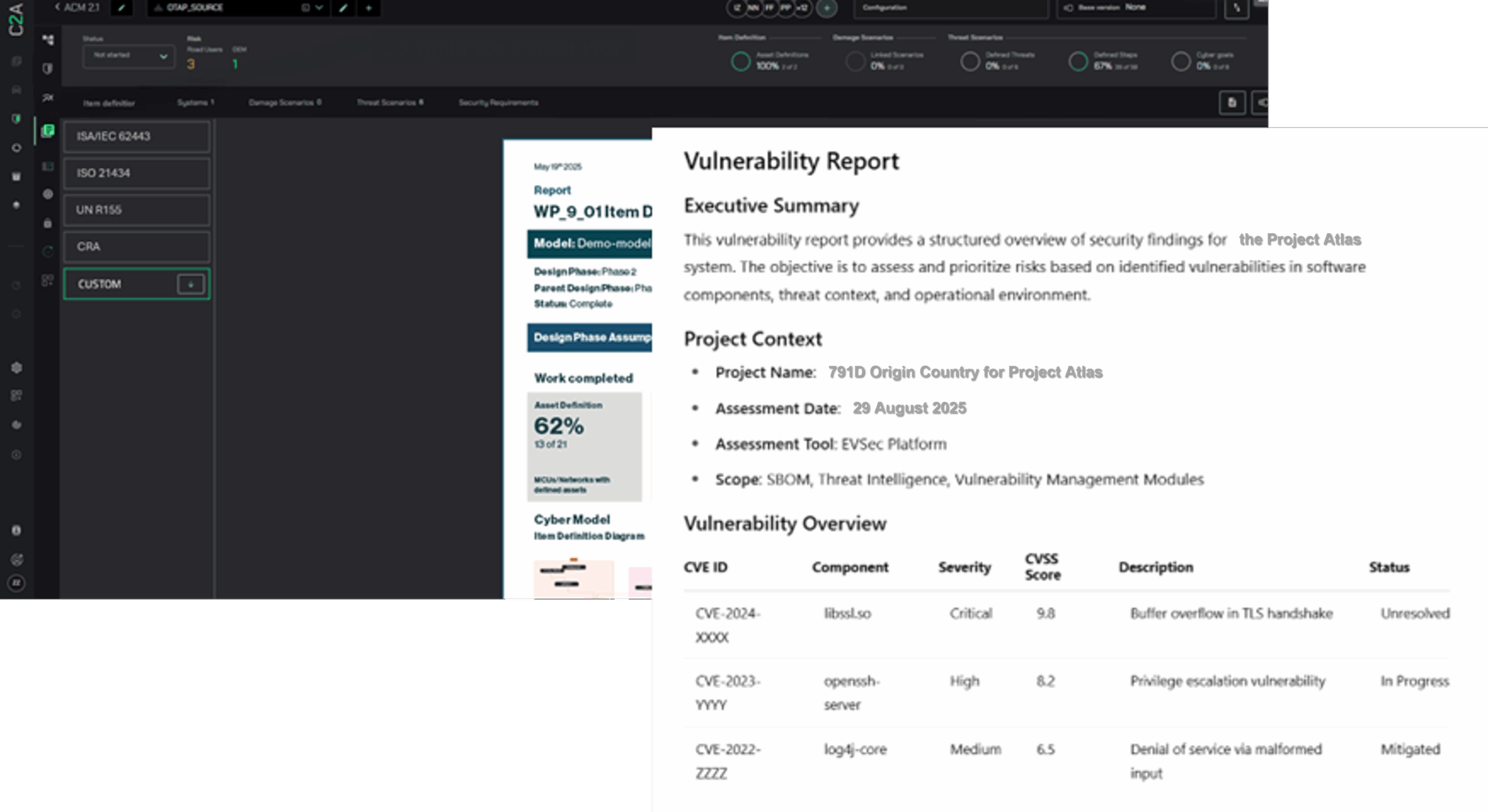
Medical device manufacturers face growing cybersecurity and compliance obligations, especially under FDA Section 524B, ISO 14971, and EU MDR. C2A Security’s EVSec Platform delivers an end-to-end solution to automate, validate, and manage software bill of materials (SBOMs), hardware BOMs (HBOMs), and component BOMs (CBOMs) throughout the device lifecycle – from design to postmarket surveillance:
- Centralized BOM Management:
EVSec provides full lifecycle management of SBOMs, HBOMs, and CBOMs in one unified platform. It supports key industry formats like CycloneDX, SPDX and more, enabling manufacturers to maintain visibility across components and dependencies. Every BOM is versioned, tracked, and governed by secure workflows that align with organizational policies, allowing teams to stay in control from early design to final release. - Automated Validation & Policy Enforcement:
The platform automates vulnerability detection, license validation, and component health checks, flagging issues as soon as third-party components are onboarded. Custom policies can be enforced across the supply chain, with automatic alerts for non-compliant libraries, restricted licenses and more. Audit-ready evidence is maintained continuously, supporting declarations of conformity and regulatory filings. - Triage & Context-based Risk Prioritization:
EVSec enables security and engineering teams to focus on what matters most. New components are triaged automatically, and SBOM data is linked to product architecture and TARA models to assess real-world impact. Enabling efficient and fast risk mitigation. - Collaboration & Integration:
EVSec ensures secure collaboration between engineering, security, and compliance stakeholders. Teams can review, validate, and approve BOMs efficiently across departments and with external suppliers. Integrations with Jenkins, JIRA, Git, and other CI/CD tools bring BOM security and compliance checks directly into the development pipeline, without interrupting workflows. - Continuous Compliance:
With built-in support for global regulations – including FDA 524B, ISO 14971, and more – EVSec continuously tracks compliance status and automates documentation. As components change, reports are updated in real time, helping manufacturers prepare for premarket submissions and respond confidently to audits and postmarket reviews.
With C2A Security, medical device manufacturers can shift from reactive compliance to proactive, context-based cybersecurity, backed by deep supply chain visibility, automation, and traceability. EVSec simplifies complex SBOM management, reduces the risk of regulatory delays, and empowers organizations to deliver secure, compliant, and trusted medical technologies to market.
Schedule a demo to learn how C2A Security can help streamline SBOM processes and risk prioritization for medical device manufacturers.