The development of the first electric vehicle in 1832 has since given way to an ecosystem nobody at the time could anticipate. Though consumer demand is set to soar in the coming years, with 30 million EVs expected to take to roads in the EU alone, challenges have surfaced at every point in the supply chain. A lack of raw materials is causing battery shortage, manufacturing constraints result in slow delivery to consumers, while the U.S. may need to increase the supply of EV charging by as much as 20 times to effectively meet demand.
Most recently, charging station vulnerability has put the industry at risk. Hacked electric charging stations in Russia display messages disparaging President Putin, while others in the Isle of Wight link to adult websites. It’s a growing trend. “Black hat” hackers are targeting EV charging stations in an effort to turn a profit fast, focusing on the most lucrative part of the EV ecosystem: those with direct access to users credit card information.
With no signs of demand slowing and increased investment from the Biden Administration in the electric vehicle ecosystem — everything from battery development through to charging stations — consumers must question, how cyber safe is it to invest in an electric vehicle? Any supply chain backed by electricity is vulnerable to cyber threat, are the right moves being taken to protect the sanctity of the electric vehicle ecosystem?
The Electric Vehicles are more vulnerable
The automotive industry has always been prone to cyber threats. Connected vehicles today have over 100 million lines of code and can be equal to approximately twenty computers. Vehicles comprise many components, all of which need to communicate with each other to get a full picture of the entire cybersecurity landscape in a vehicle.
But the electric vehicle ecosystem is even more so — the vehicles themselves host sophisticated control systems with wide attack surfaces that are vulnerable at many points, including charging stations. White hat researchers have identified several vulnerabilities in this emerging market. Most recently, drivers of Nissan Leaf cars were warned electric cars could be remotely hacked through bluetooth connectivity to the internet, resulting in remote control of their systems or worse.
In 2021, black hat hackers became the majority. Malactors looking to profit off manufacturers’ cybersecurity missteps, attacks ranged from simple display and text tampering to operational damage of charging stations and even the battery management system of a vehicle. Attacks happened globally, putting the security of EV charging stations into the limelight — now, it’s not a nice to have, but a must.
EV charging stations emerge as the most vulnerable.
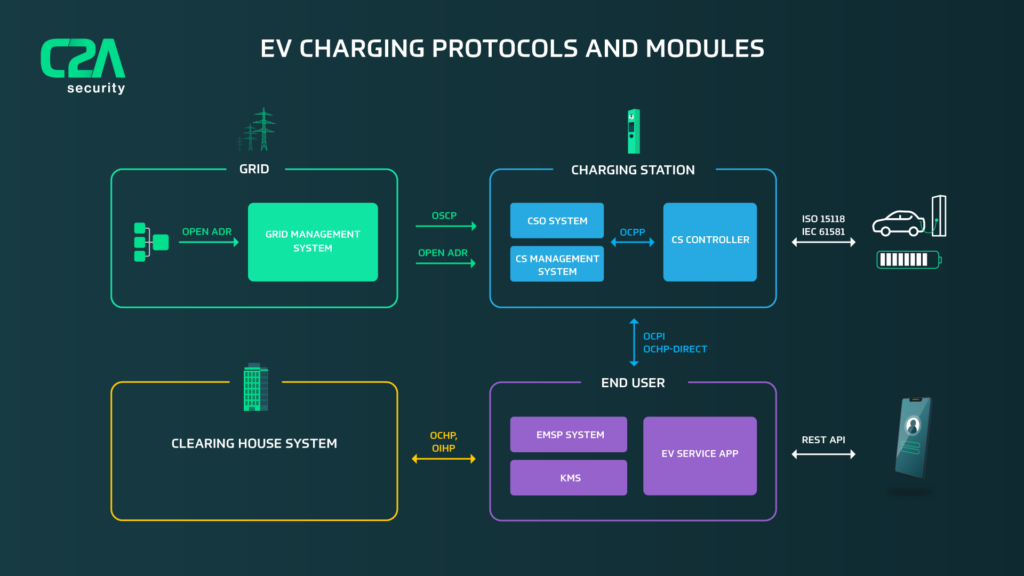
The typical EV charging system consists of a remotely-managed operation center, grid management center to balance power, a mobile app for user interaction, an in-vehicle battery management system and the charging station itself.
With unlimited public access, no security by design, limited resources for protection and supply chain control, vast attack surface with both remote and physical connections and its position holding valuable business assets, EV charging systems are by far the most vulnerable element of any EV ecosystem.
The risk in reality: what can hackers do to EVs?
With remote code execution threats, anything is possible. Hackers can manipulate charging station screens to place text, pictures, retrieve personal information from consumers or place prompts to consumers to charge their EV for free. Though concerning, the real security risks begin when damage is made to charging stations, vehicles or to the entire electric grid — which is possible through the power management system housed within a charging station.
Threat | Risk |
Attack Central Operation System through Charging Station and retrieve multiple personal information records | High |
Attack Grid Power Management system through Charging Station and manipulate power | High |
Attack Station Management System through Charging Station and shutdown operation | High |
Attack BMS in Charging car through Charging Station and retrieve personal info | Medium |
Attack BMS in Charging car through Charging Station and damage Battery | Medium |
Attack | Low |
What can be done to protect EV charging systems?
In order to protect the weakest link in the system, EV players must embed security within the lifecycle of charging station development. From concept, development and validation through to post production monitoring, security must be assessed throughout the entire vehicle lifecycle. Fortunately, the Security Development Lifecycle (SDL) processes and tools that exist for the BMS in vehicles, as required by current automotive regulation, can be adapted for the needs of EV Charging stations and networks as well.
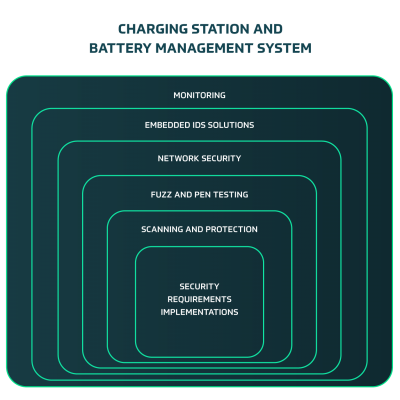
Charging Station makers, owners, and operational services, all must work in tandem to ensure risk is visible and mitigated during development, and monitored after production for new vulnerabilities. Only through a centralized and managed security approach can different players in the ecosystem share security information, understand risk, and mitigate new vulnerabilities. Multiple security layers such as embedded IDS, network security, fuzzing validation and more, will all work to reduce risk.
As described in the diagram above, different security layers will be created during the SDL process for charging stations.
- Security Requirements Implementations: security concept derived from threat analysis
- Scanning and protection: code or binaries scanning for supply chain vulnerabilities, and protection of code and binaries
- Fuzz and Pen testing: system validation of the security by performing fuzz testing and penetration testing
- Network Security: applying network security controls such as firewall
- Embedded IDS solution: monitoring run time activities in charging station to detect real time attacks and act upon these attacks
- Monitoring: overall monitoring of all activities including threat intelligence to detect new vulnerabilities
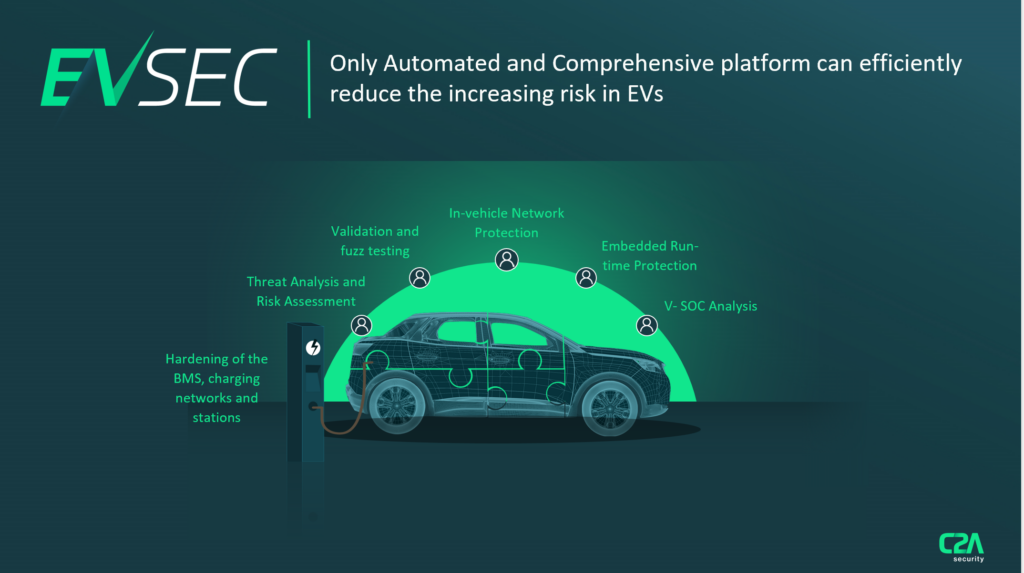
C2A solutions means automated cybersecurity for the entire EV ecosystem.
C2A’s suite of solutions offers protection from in-vehicle, to charging station and electric grid. Ongoing management has never been easier. Backed by intuitive automation, planning, testing and embedded security throughout the vehicle lifecycle seamlessly comply with new standards and regulations. By partnering with EV charging and BMS leaders, C2A means comprehensive cybersecurity designed for modern mobility to supercharge the EV evolution.
C2A’s flagship product EVSEC is an automated Cyber Security Management System (CSMS) that breaks down communication silos to create a true cybersecurity single pane of glass. Its impact is felt at every stage of the vehicle lifecycle: streamlining new processes and thwarting threats facing modern vehicles. Now, pressure is removed from security teams by reducing manual work and expertise and replacing it with advanced process automation.
As the EVs evolve, so must its sophistication and response to cyber threats. C2A Security’s suite of solutions is specifically adapted to meet the needs of the entire EV ecosystem — from the vehicle itself, through to the charging station, electric grid and BMS. Planning, testing and embedded security are all easily deployed. Ongoing management of the entire EV ecosystem security lifecycle is simpler than ever, as C2A provides automated, intuitive and comprehensive cybersecurity for the EV revolution. By including everything from threat analysis, embedded protection, fuzzing, network and host IDS, and VSOC event analysis, now, the electric vehicle supply chain is supercharged with cybersecurity.