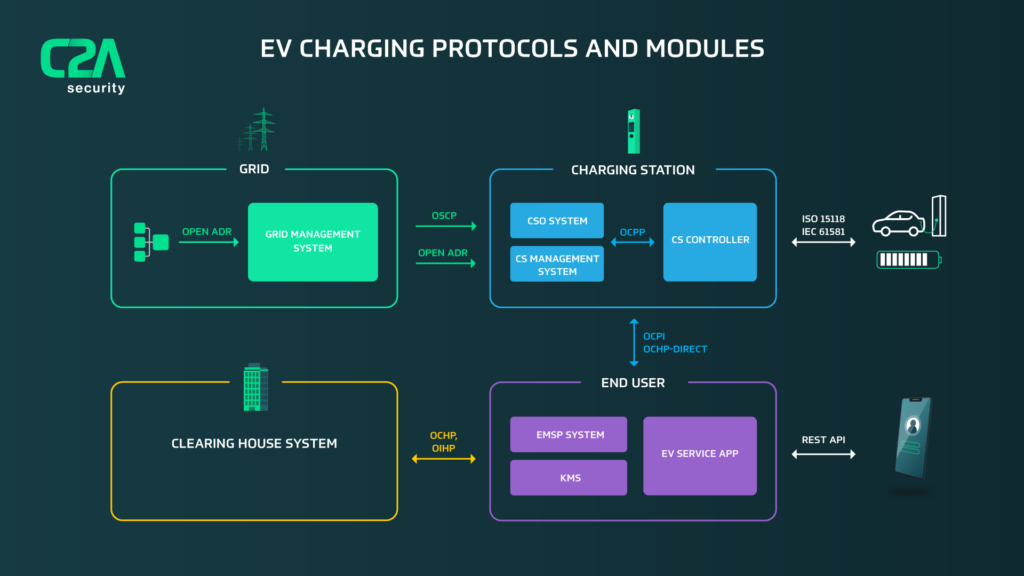
As the adoption of electric vehicles continues to grow, so do the concerns about the security of electric vehicle (EV) charging infrastructure. Cyber threats targeting EV charging systems are becoming increasingly sophisticated, posing a significant risk to both the safety of individuals and the stability of the energy grid. In addition, regulations surrounding EV charging are quickly evolving, with governments and industry bodies introducing new standards and requirements to ensure that charging infrastructure is resilient and secure.
In this blog post, we’ll explore the current state of cyber threats to EV charging systems, as well as the latest regulations and standards designed to protect this critical infrastructure.
Potential cyber threats to the EV charging infrastructure
It’s no secret that as more and more people switch to electric vehicles, the EV charging infrastructure is becoming a bigger target for cybercriminals, who are constantly looking for ways to exploit vulnerabilities, and unfortunately, there are quite a few vulnerabilities to exploit.
For example, cybercriminals can skim credit card information from EV charging stations, just like they can at conventional gas pumps or ATMs. That’s just the beginning – potential hackers can use cloud servers to hijack entire electric vehicle charger networks, causing massive amounts of damage and disruption.
Some of the main cyber threats to EV charging infrastructure include:
- Malware and ransomware attacks. This is any type of computer program designed to harm or take control of EV chargers, potentially leading to unauthorized access and manipulation of the EV charger’s data. These attacks can also cause charging stations to malfunction or shut down, potentially leading to disruptions in the electrical
- Unauthorized access. Attackers may attempt to gain unauthorized access to the charging infrastructure’s control systems or backend networks. If successful, they could potentially manipulate the charging process or steal sensitive data.
- Denial-of-service (DoS) attacks. DoS attacks can be used to overwhelm the charging infrastructure with traffic, causing it to slow down or stop working altogether. This could impact the ability of EV owners to charge their vehicles, and could also lead to disruptions in the electrical grid.
- Social engineering attacks: Social engineering attacks, such as phishing, can be used to trick EV owners or charging infrastructure operators into providing sensitive information or access to systems.
The potential consequences
The potential consequences of cyber threats to electric vehicle charging infrastructure are significant and far-reaching:
- Disruption of charging services: Cyber attacks on EV charging infrastructure can cause charging stations to malfunction or shut down completely, leading to a disruption of charging services. This can result in inconvenience and frustration for EV owners, and can also impact the ability of businesses and organizations to operate EV fleets.
- Compromised personal and financial data: Cyber criminals can steal personal and financial data from EV charging infrastructure systems, such as credit card information. This can lead to identity theft and financial losses for individuals.
- Damage to infrastructure: Malware or ransomware attacks on charging infrastructure systems can cause physical damage to the infrastructure, leading to expensive repairs or replacement costs.
- Safety risks: Cyber attacks on charging infrastructure could also create safety risks for EV owners and the public. For example, a compromised charging station could potentially cause a fire or explosion, leading to serious injury or property damage.
- Impact on the electrical grid: A large-scale cyber attack on EV charging infrastructure could potentially impact the stability of the electrical grid, leading to power outages and other disruptions.
The regulatory angle
As the importance of electric vehicle (EV) charging infrastructure grows, governments and industry organizations around the world are taking steps to ensure that charging stations are secure and reliable.

The UK is the 1st country to mandate EV charging regulations (The Electric Vehicles Smart Charge Points Regulations 2021), which went into effect in June 2022, as part of an overhaul of the country’s Building Regulations. The regulations ensure that charge points meet certain device-level requirements, enabling a minimum level of access, security, and information for consumers. On the security aspect, a charge point must be designed, manufactured, and configured to provide appropriate protection:
- Against the risk of harm to, or disruption of, the electricity system
- Against the risk of harm to, or disruption of, the relevant charge point
- For the personal data of the owner and any other end-user of the relevant charge point
The National Institute of Standards and Technology (NIST) in the United States has developed a framework for improving critical infrastructure cybersecurity that includes guidelines for securing EV charging infrastructure. The European Union Agency for Cybersecurity (ENISA) has also published guidelines for securing EV charging infrastructure, focusing on areas such as access control, data protection, and incident response.
While these regulations and standards are necessary to ensure the safety and reliability of these systems, they create both opportunities and challenges for companies manufacturing EV charging equipment:
- Cost of compliance. Regulations and standards can require significant investments in security measures – from software to hardware, as well as expertise and workforce, which can increase the cost of producing EV supply equipment (EVSE)
- Lead by security. EVSE manufacturers have a unique opportunity to build trust with consumers by providing a security layer that will translate to added value for consumers
- Complexity of compliance. Regulations and standards can be complex and difficult to navigate, specifically when operating in more than one market
How C2A Security can help
C2A Security’s DevSecOps platform is a fully automated TARA solution that empowers OEMs to address the challenges of merging security, compliance, and product innovation.
- Expertise and knowledge: C2A Security has been an integral part of recent regulatory efforts and standards’ working groups, such as the WP.29 and ISO/SAE 21434
- Interoperability: The platform is designed to work seamlessly with a wide range of DevOps tools, such as GitLab, Jira, ServiceNow, Polarion, and others – helping EVSE companies reduce complexity and avoid costly integration efforts
- Automated TARA, mobility-grade: By automating the risk management, EVSE companies can build a ‘breathing’ and updateable analytical threat model, to serve as the core of their DevSecOps automation process
- Know your code: Maintain a complete picture of your software and its potential vulnerabilities, from the grid to the car and back
Interested in hearing more? Leave your details to schedule a demo with me.