Manufacturing modern vehicles at scale is a uniquely difficult challenge. Some in the industry have gone as far as to claim that managing automotive manufacturing processes is more complicated than designing a spaceship. One commonly-cited reference point for the complexity of a modern vehicle is the 100 million lines of code found within. In an era of skyrocketing consumer expectations, OEMs strive to create a reliable, safe, cost-optimized, cutting edge, long-lasting vehicle… and at mass production scale.
The automotive ecosystem is thus unique among industries, from its complex supply chain to a growing list of technological expectations, alongside safety requirements, and minimal compute resources to spare. C2A was born with an awareness of the challenges inherent in designing and manufacturing vehicles. As a cutting-edge automotive cybersecurity solution, the C2A platform offers very strong security, enhancing vehicle and passenger safety. What sets C2A apart, however, is that it speaks the language of this unique industry. Rather than a cyber company branching into automotive, C2A considers itself an automotive company focused on cyber. As a result, the company has been built from the ground up to fit within the technical and business comfort zones of today’s leading OEMs and Tier 1 suppliers:
1. Automotive-grade solutions
In a safety-first industry, partners across the ecosystem must — first and foremost — provide a reliable, trustworthy solution, while equipping OEMs with strong measures to fight off attackers. There is no “silver bullet” in cybersecurity; no single security layer can protect a vehicle from the entire range of potential attacks. Rather, a multilayered approach is needed.
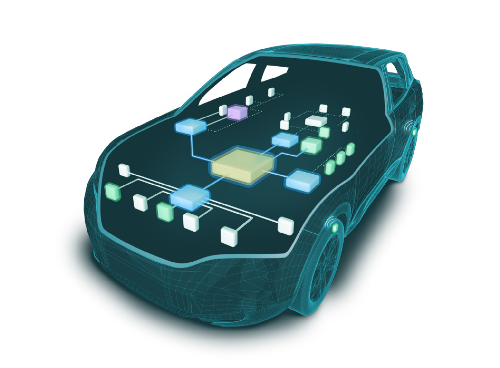
C2A’s multi-layer cybersecurity protection
C2A offers a complete suite of solutions, each defending from specific attack vectors. From a cybersecurity point of view, a vehicle is a completely new domain. Cars feature high-load networks with unique protocols — some very-much legacy, closely resembling protocols and standards from the IT world of the 1990’s — alongside runtime environments not originally designed with security in mind. On the other hand, most automotive ECUs are quite monotonic, with a somewhat limited attack surface. C2A’s products were tailor-made to operate in this environment and to protect from automotive-focused attacks, including network-based and those leveraging in-memory vulnerabilities.
Verifying the safety of any automotive system requires a challenging and rigorous process of certification. Some security paradigms do not comply with the requirements of safety certification. Indeed, some cyber solutions even remove certification compatibility through the very processes designed to protect the car. Understanding the need for verifiable cyber defense in strategic points inside the vehicle, and not only on the perimeter, C2A’s cybersecurity products comply entirely with safety requirements in a manner fully compatible with the certification process
2. Ease of integration
Among the core functionalities of an OEM is integration. Rather than manufacturing exclusively in-house, OEMs rely on a complex supply chain of manufacturers to provide many of a vehicle’s components. Considering this complex supply chain, ease of integration is a primary consideration for automotive players.

C2A understands that hardware-based solutions considerably and unnecessarily complicate an already-daunting supply chain. C2A’s products are software only, with minimal integration complexity, shrinking integration and implementation process from months to days.
However, even software-only platforms can make demands on the hardware of a car. In an industry optimized down to the cent per component, every bit of compute resources are accounted for, leaving few unutilized compute resources inside vehicles. For seamless integration, software must have a negligible computing footprint, while meeting automotive’s strict, real time processing requirements. To meet these constraints without compromising on security functionality, C2A formed an interdisciplinary team of algo-trading researchers, low-level security veterans and hardware experts. The out-of-the-box approach taken by C2A allows real-time cybersecurity protection in a car’s existing 80 MHz CPU with 80% prior processor utilization.
In addition, C2A collaborates with leading hardware and software suppliers to provide automotive manufacturers a ready-to-use, simple security solution. C2A has adopted a collaborative, solutions-based approach, working closely with other Tier 2’s to provide OEMs and their suppliers complete, tailor-made solutions meeting or exceeding their requirements.
Finally, C2A offers a practical business model familiar to OEMs. Rather than shoehorning SaaS or other business models from the world of software into the automotive world, C2A bills like any other part of the automotive supply chain. C2A charges a simple licensing fee well within security budgets of OEMs.

3. Whitebox approach
OEMs and Tier 1s are sufficiently sophisticated and strategic to expect control over security processes and to fully understand every component in the car. Such players will not — and should not — integrate “black box” security systems into their cars. C2A has created transparent products that are fully customizable, empowering our clients with full control over their vehicles’ security.
4. Security lifecycle management
When designing cybersecurity for mass-market vehicles, product longevity becomes a significant factor. Unlike the IT or IoT ecosystems, cars can stay on the road for two decades or more. As outlined in previous posts, cybersecurity products require ongoing management and adaptation throughout the life cycle of a vehicle to handle an ever-changing array of incidents and environments.
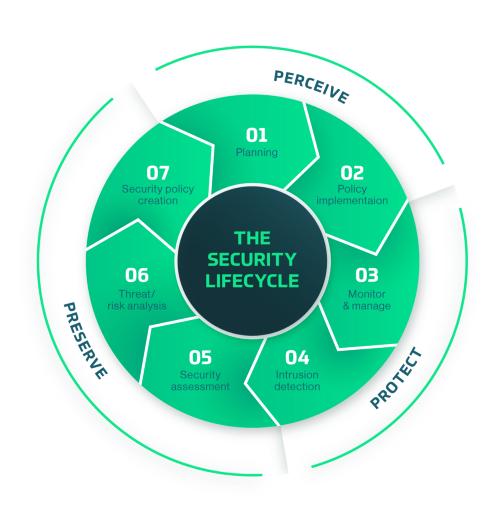
We provide our clients with the tools and products to easily adapt the vehicles’ security to match each phase of the automotive life cycle. C2A knows that clients want and deserve to be involved in every phase in the security lifecycle — from planning through to protection and preservation.
At its very core, C2A seeks to enable and empower clients to fully own the security lifecycle. Without a long-term design from the ground up, such security products are liable to become both a financial and operational burden long after the vehicle has reached the customer.
C2A was not designed with a dedicated automotive approach out of convenience. Every new product and idea must meet the high standards of the automotive industry in reliability, practicality, transparency, and long-term sustainability. Any concept not in line with C2A’s automotive approach, regardless of novelty or ingeniousness, is immediately disqualified. As responsible members of the automotive ecosystem first, C2A goes the extra mile to craft products around the unique priorities and needs of its partner OEMs and Tier 1 suppliers.