" " indicates required fields

Risk-driven BOM management identifying true risks, enabling precise prioritization, resource allocation, and cost-effective mitigation.
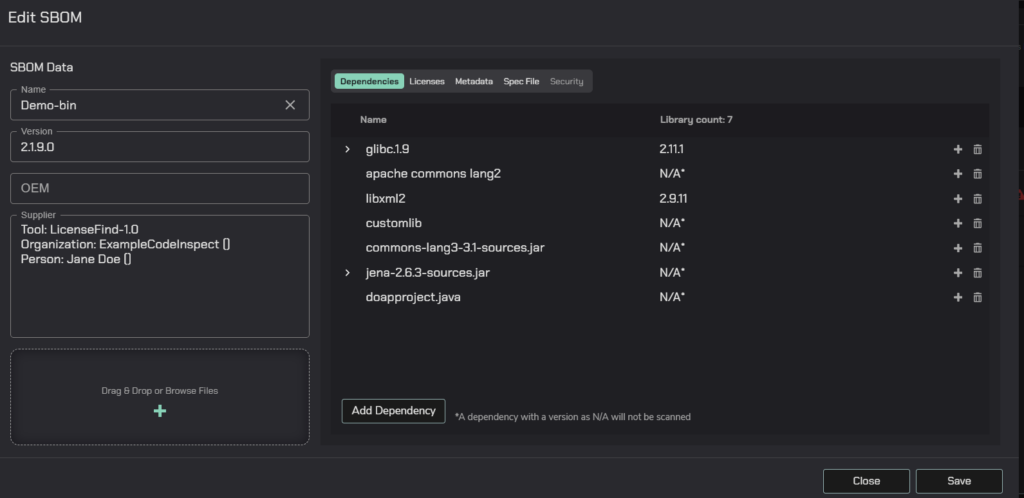
Create direct BOM or ingest with 3rd-party sources. Automatically validate and manage the BOM in the context of internal teams and external suppliers as part of EVSec sharing and collaboration capabilities (track, approve and validate).
Leverage EVSec’s binary analysis and BOM scanning capabilities for automated BOM validation, including dependencies, licenses, and weakness analysis, ensuring coherence.
The inherent bond between EVSec BOM & Vulnerability Management and the TARA Information Layer
Streamlined BOM Management
Effectively manage BOMs within the context of the project or corporate ensuring accurate and up-to-date information.
Risk-Driven Vulnerability Prioritization
Automate the connection between risk and other product security information layers, enabling accurate risk-based identification, prioritization, and mitigation of emerging vulnerabilities.
True Impact Analysis
Leverage the understanding of the model together with risk scores from multiple databases to determine the real impact on your model and product.
Ease of Compliance and Reporting to Regulators
Benefit from a comprehensive toolkit for optimized security posture, automated and dynamically updated work products, and customizable reports for regulators and internal company stakeholders.
Accelerated Project Delivery
Streamline software development through automation and efficient collaboration, enhancing overall efficiency, security and Operations by Design.

“The method of integration between the BOM information and the TARA is a unique differentiator of EVSec, something we haven’t seen with other vendors.”

CRO
C2A Security

VP and GM, Medical Technology
C2A Security
Ken Zalevsky brings over 20 years of medical device cybersecurity experience to his role at C2A Security, where he serves as VP and GM, Medical Technology, following the acquisition of Vigilant Ops in October 2025. A former Bayer executive, Ken founded Vigilant Ops in 2019 after witnessing the consequences of inadequate technical preparation in the healthcare industry. He is an active contributor to CISA’s SBOM working groups and a frequent speaker on software supply chain security. Ken’s mission: transform SBOM from a compliance checkbox into operational intelligence that keeps patients safe while streamlining regulatory processes.