Medical device manufacturers are no longer struggling to find vulnerabilities. They are struggling to decide which ones matter.
As SBOM adoption has expanded, security and engineering teams now have unprecedented visibility into the software components that make up their devices. That visibility, however, has surfaced a new challenge: hundreds or sometimes thousands of CVEs per product, with little guidance on where to focus first. The result is alert fatigue, inefficient remediation, and difficulty explaining decisions to regulators. This often leads to delayed releases, reactive patching, and remediation decisions that are difficult to defend during audits and regulatory review.
FDA cybersecurity expectations are explicitly risk based. Manufacturers are not expected to remediate every vulnerability, but they are expected to understand exploitability, assess potential impact, and act where cybersecurity issues could reasonably affect safety, effectiveness, or availability. Raw vulnerability lists do not provide that understanding.
Why Vulnerability Lists Fall Short
A CVE on its own says very little about real world risk in a medical device. The same vulnerability can have dramatically different implications depending on where and how it appears in the system.
In practice, risk depends on context such as where the component sits in the device architecture, whether it is externally reachable or internally isolated, what function it supports such as control, sensing, monitoring, or logging, and whether exploitation could plausibly impact clinical use or patient safety. For example, a medium severity vulnerability in a network exposed update mechanism may present greater patient risk than a critical vulnerability in an isolated logging component.
Without this context, teams default to severity scores or worst case assumptions. Both approaches generate noise rather than clarity.
What Contextualization Enables
When vulnerabilities are evaluated at the component level, prioritization becomes more precise. Teams can distinguish between issues that require immediate action and those that can be monitored or deferred with justification. Contextual prioritization allows organizations to focus remediation on vulnerabilities that affect exposed or safety relevant components, reduce time spent on low risk issues that do not meaningfully reduce patient risk, and provide a clear, architecture based rationale for decisions during regulatory review.
This approach aligns with FDA expectations that manufacturers understand how cybersecurity issues relate to device behavior and risk, not just vulnerability counts.
How Threat Modeling Enables Contextualization and Prioritization
Threat modeling provides the structure needed to turn vulnerability data into risk based priorities. By anchoring each vulnerability to a specific component in the device architecture, the threat model clarifies whether a vulnerability is reachable and how it could realistically be exploited. A weakness in an isolated component carries a different risk profile than the same weakness in a network exposed controller or software update pathway.
By incorporating attacker behavior and attack paths, threat modeling shifts prioritization away from abstract severity scores and toward realistic exploitability. It also connects vulnerabilities to device specific impact, including effects on safety, essential performance, and availability. This enables teams to focus remediation on issues that materially reduce patient risk and to clearly justify why certain vulnerabilities were addressed first while others were monitored or deferred.
Traditional Versus Contextualized Approach
In a traditional workflow, SBOM data cascades into long CVE lists and severity scores that fail to reflect how a device actually operates. The result is unclear priorities and an expanding remediation backlog. Decisions are driven by abstract metrics rather than device specific risk, creating inefficiency and regulatory friction. Figure 1 illustrates how severity driven workflows flatten risk, causing most vulnerabilities to appear urgent without clear linkage to patient or operational impact.

Figure 1. Traditional approach with unclear priorities and vulnerability overload
In contrast, a contextualized workflow inserts architectural and functional analysis between the SBOM and remediation steps. By evaluating vulnerabilities in the context of component placement, reachability, and clinical function, this approach transforms raw vulnerability data into actionable risk insight. Figure 2 shows how architectural context introduces a decision layer that translates SBOM data into clear and defensible remediation priorities.
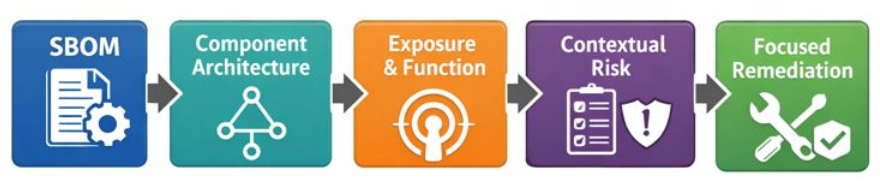
Figure 2. Contextualized Approach – Contextual Prioritization and Remediation
The outcome is not fewer vulnerabilities. It is clearer prioritization, enabling teams to focus remediation where it meaningfully reduces patient and operational risk.
Conclusion
Moving from SBOM visibility to meaningful action requires more than counting vulnerabilities or reacting to severity scores. Without architectural and operational context, remediation efforts quickly accumulate into large backlogs with unclear priorities. By anchoring vulnerabilities to component architecture, exposure, function, and realistic attack paths, manufacturers can translate raw CVE data into defensible, risk-based decisions.
SBOMs are the starting point, but context is what turns vulnerability data into effective cybersecurity action.
C2A Security enables this contextual, risk-based approach by anchoring SBOM and vulnerability data to device architecture and threat models, helping manufacturers make defensible remediation decisions. Learn more or request a demo here.







