The Cyber Resilience Act: What You Need to Know
The Cyber Resilience Act (CRA) has shifted the mindset of industrial suppliers and manufacturers who are responsible for securing vast interconnected networks of operational technology (OT) and information technology (IT) systems.
Further Reading:
Download your complimentary CRA 1-pager (PDF)
CRA for MDMs and Healthcare Security Leaders (blog post)
Cyber Resilience Act and Tariler Bodybuilders (blog post)
Navigating UN Regulation No. 155 (blog post)

CRA guidelines will complement existing industrial security protocols, such as IEC 62443 to address security for industrial automation and control systems (IACS) throughout their lifecycle, and IEC ISO-27001 for managing information security beyond the Factory Acceptance Test (FAT) which evaluates the safety of equipment and machinery before it is shipped to the customer.
The industrial sector has been a prime target for cyber-attacks in the past few years.
Cyber Threats to the Industrial Sector
The average total cost of a data breach in the industrial sector was $5.6M.
Key findings from the 2024 IBM Cost of a Data Breach report showed that the average total cost of a data breach in the industrial sector was $5.6M. Ransomware and supply chain attacks were the primary security threats plaguing manufacturers and critical infrastructure providers.
A recent survey conducted by Sophos found that 65% of manufacturing and production organizations were hit by ransomware last year. The report also found that manufacturing organizations reported a mean cost of $1.67M to recover from a ransomware attack.
65% of manufacturing and production organizations were hit by ransomware in 2024.
Unsecured ICS/SCADA systems and programmable logic controllers (PLCs) pose significant security risks if critical vulnerabilities are not mitigated effectively, potentially compromising the entire supply chain and disrupting the production processes. Manufacturing plants may be shut down indefinitely if an attacker gains unauthorized access to one of the SCADA systems.
The consequences of a cyber attack against the mining industry include operational disruption – stemming from lost production and recovery time to reactive cybersecurity measures that encompass full incident response investigations and triage.
The costs of a breach can multiply further if the mining or manufacturing companies are non-compliant with industry regulations or data protection laws. GDPR violations can result in fines of up to €10 million, or 2% of the manufacturer’s global annual revenue from the preceding financial year. The question is then, how can manufacturers and others in the industrial sector avoid these penalties while demonstrating CRA compliance? That is the focus of this article.
Strategies for Achieving Compliance in the Industrial Sector
Here are several common industrial attack points and best practices to implement to remain compliant with CRA requirements, ensuring safety protocols meet the criteria needed to receive a CE marking.
Secure access to programmable logic controllers (PLCs): Attackers can inject malicious software or exploit vulnerabilities in the PLC’s firmware to manipulate data or take complete control over the infrastructure. Isolate PLCs from other networks and cloud servers by enforcing the least privileged access. Monitor and review logs to detect any suspicious activity or unauthorized access attempts, which are clear signs of a breach in progress.
Conduct routine cybersecurity risk assessments: Manufacturers must have a security plan, and planning begins with risk assessments. Define the current cybersecurity risk posture of the entire manufacturing plant, from the control systems to the supply chain, and employee workstations. Determine the severity of risks and prioritize mitigation strategies mapped to business objectives. Perform cyber risk quantification to assess the financial impact of potential attacks.
Bill of Materials (BOM) assessment: The best way to gain visibility over your supply chain is by generating a BOM. Think of a BOM as a list of ingredients encompassing all raw materials, items, assemblies, subassemblies, part numbers, procurement types, and components required to manufacture a product. Every manufacturer must create a BOM to ensure supply chain transparency and meet CRA requirements to obtain a CE marking.
Vulnerability management: Create an ICS/SCADA-focused incident response plan following NIST 800-61 guidelines. Prioritize high-risk vulnerabilities and isolate compromised endpoints to contain and mitigate any serious cybersecurity threats throughout the product lifecycle. When in doubt, take a step back and analyze the current risk landscape. Ask the following questions:
- Who has access to the ICS control systems?
- Have third parties been held accountable for following CRA requirements and defined industry compliance regulations?
- How are IT and OT networks segmented to prevent unauthorized access?
- How do you detect and respond to unauthorized changes in programmable logic controllers (PLCs)?
Assemble a team to conduct the risk assessment and delegate responsibilities accordingly.

Industry Spotlight: Preparing Mining Companies for CRA Readiness
Mining companies are attractive targets for cybercriminals. IoT interconnected devices have heightened security risks exponentially. Consider the scenario where a threat actor gains access to the control system, essentially being able to shut off production from a smartphone at any designated geolocation point. A scary yet surreal possibility that could result in significant operational downtime, equipment damage, and life-threatening safety hazards for on-site workers.
Further Reading
A Deloitte Report: Securing Industrial Operations in Mining (PDF)
Unpatched software vulnerability in a VM can spiral into a full-scale breach if left undetected. A BOM assessment helps security professionals document and inventory all critical assets that require immediate mitigation. Every recorded item and component serve as a checklist and reference point to help security teams track and manage risks throughout the product lifecycle, further enhancing CRA readiness.
Enhancing CRA Readiness and Compliance for the Industrial Sector with C2A Security
Manufacturers are responsible for securing machinery and maintaining compliance with regulatory frameworks. C2A Security simplifies the process with EVSec, by helping manufacturers, OEMs, and mining companies demonstrate CRA readiness to obtain that coveted CE marking and close those hidden security gaps across the supply chain.
Here’s how:
End-to-end premarket and postmarket solution: EVSec ensures continuous compliance from development to deployment and postmarket monitoring.
Context-Driven Prioritization: EVSec prioritizes cybersecurity risks based on context, ensuring that the most critical threats receive immediate attention while balancing cybersecurity with operational needs.
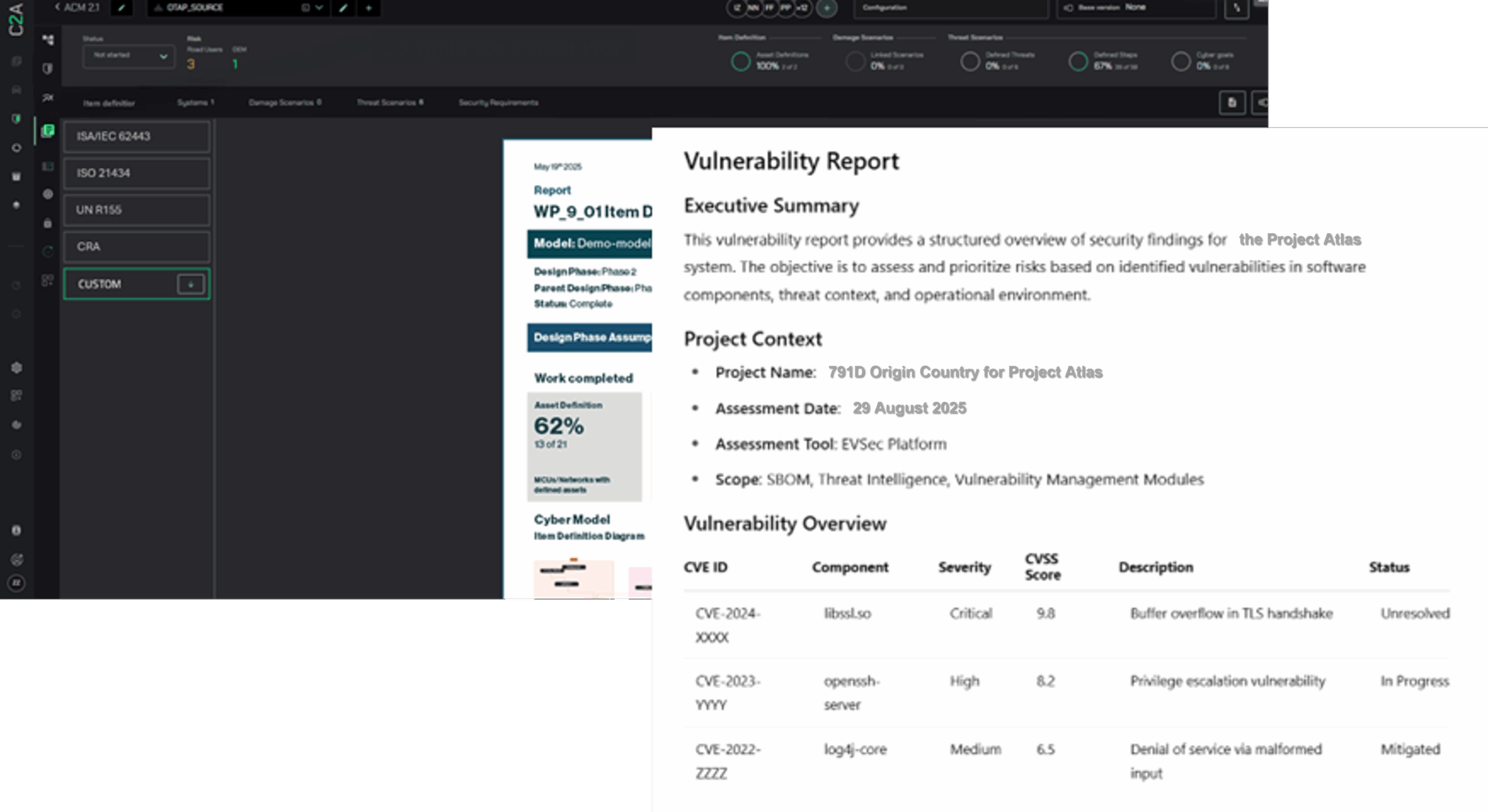
Automated BOM validation: EVSec leverages BOM management and vulnerability orchestration to monitor and secure third-party software components, reducing supply chain risks and ensuring compliance.
Automate security processes: EVSec automates vulnerability scanning, patch management, and compliance audits, reducing manual workload while ensuring continuous security.
Collaboration & delegation: EVSec enables real-time collaboration, task delegation, and workflow tracking while automating critical security tasks.
Key benefits include:
- Automated BOM validation and management for internal teams and external suppliers.
- Full visibility into open-source and third-party software components.
- Risk mitigation throughout the entire product lifecycle.
- Automation of security processes, including vulnerability scanning and patch management.
- Seamless regulatory compliance with IEC 62443, ISO 27001, NIST guidelines, and FDA SBOM mandate, simplifying compliance through automated auditing and reporting.
As the only context-driven product security platform for Premarket Approval and Postmarket Surveillance, EVSec leverages dynamic risk assessment, BOM validation, and vulnerability management to ensure targeted protection and compliance.
Schedule a demo to learn how C2A Security can help you prepare for CRA readiness.