The evolving threat landscape in today’s digital world makes robust cybersecurity strategies critical for every organization. To address these risks effectively, organizations need frameworks that assess their current cybersecurity posture and guide continuous improvement. The Cybersecurity Capability Maturity Model (C2M2) is an instrumental tool, that provides a structured approach to enhancing an organization’s cybersecurity capabilities, both information technology (IT) and operations technology (OT). But how does C2M2 relate to other frameworks, like the NIST Cybersecurity Framework (CSF) and why should organizations prioritize ‘leveling up’ within C2M2? Read on.
***
What is the Cybersecurity Capability Maturity Model (C2M2)?
C2M2 was originally developed in 2012 by the U.S. Department of Energy (DOE) and designed by NIST, the National Institute for Standards and Technology (US), as part of its Cybersecurity Framework (CSF), to help organizations in critical infrastructure sectors assess and improve their cybersecurity capabilities. Over time, it has become widely adopted across various industries due to its structured, scalable approach.
The model is divided into ten domains, which cover broad cybersecurity activities:
- Risk Management
- Asset, Change, and Configuration Management
- Identity and Access Management
- Threat and Vulnerability Management
- Situational Awareness
- Information Sharing and Communications
- Event and Incident Response
- Workforce Management
- Cybersecurity Program Management
- Third-Party Risk Management
Each domain within the Maturity Model (C2M2) has progressive maturity indicators, helping organizations evaluate where they currently stand and identify areas for improvement.
How Does the Maturity Model Align with the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework (CSF) is another widely used cybersecurity guideline, developed to help organizations understand, manage, and reduce cybersecurity risks. While the Maturity Model and NIST CSF both serve to guide cybersecurity efforts, they are complementary rather than redundant.
The Cybersecurity Framework (CSF) focuses on five key functions: Identify, Protect, Detect, Respond, and Recover. It is designed to give organizations a comprehensive understanding of their cybersecurity risk management and can be applied across industries. However, CSF doesn’t provide a detailed roadmap on how to measure and grow cybersecurity maturity levels over time.
This is where C2M2 comes into play, offering a detailed methodology to assess the maturity of these [CSF] activities.

Why Should You Care about the Cybersecurity Maturity Model
- Heightened Cyber Risks: As cyberattacks become more sophisticated, businesses across all industries are grappling with the increasing risks to their digital infrastructure. The consequences of a data breach, from financial losses to reputational damage, can be devastating. The Maturity Model helps organizations identify weaknesses and build resilience in a structured, measurable way.
- Regulatory Compliance: Governments and regulatory bodies are increasingly requiring organizations to adhere to stringent cybersecurity standards. For example, the Cyber Resilience Act (CRA) is pushing businesses to strengthen their cybersecurity postures. C2M2 provides a measurable framework for organizations to meet these regulatory demands, especially for those in critical infrastructure sectors like energy, healthcare, and finance.
- Strategic Advantage: With cyber risks affecting operational efficiency and customer trust, cybersecurity is no longer just a technical issue; it’s a core business concern. Companies that can demonstrate a high level of cybersecurity maturity gain a competitive edge. They are better equipped to protect their assets, and their supply chain, reduce operational disruptions, and maintain stakeholder confidence.
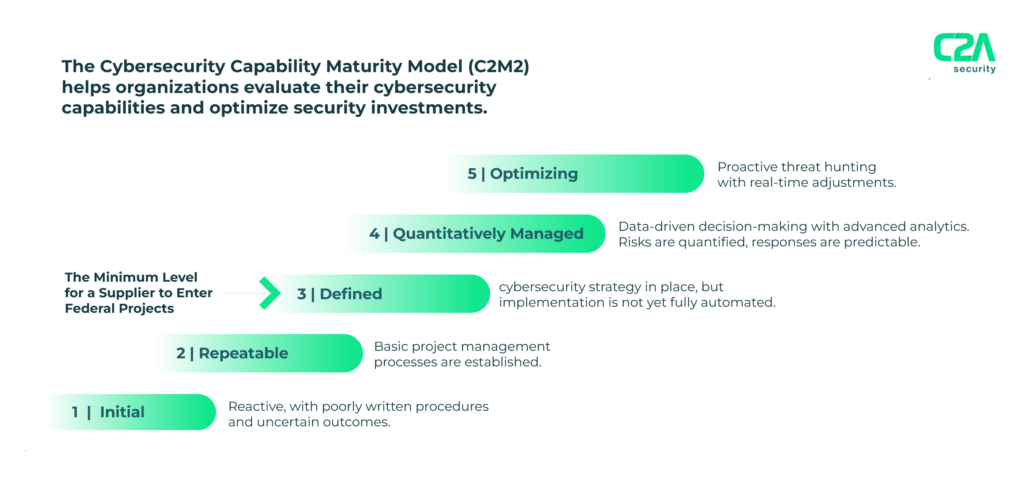
The Maturity Model Indicator Levels (MIL)
The Cybersecurity Capability Maturity Model (C2M2) defines five maturity indicator levels (MILs) to help organizations assess their cybersecurity capabilities. These levels provide a structured path for continuous improvement, allowing organizations to understand where they stand and what they need to do to advance their cybersecurity posture.
Level 1: Initiated
At level 1, the organization has begun to implement basic cybersecurity activities. These activities are typically reactive, performed on an ad-hoc basis with uncertain outcomes, and are not standardized across the organization.
- Basic Cybersecurity Practices: Some cybersecurity controls are in place, but they are informal and may not be applied consistently.
- No Formal Documentation: The organization may have some informal documentation of security practices, but formal policies and procedures are still lacking.
- Individual Responsibility: Cybersecurity tasks are often the responsibility of individual employees, with no overarching governance or accountability structure.
Level 2: Repeatable (Managed)
At this level, the organization starts to formalize its cybersecurity practices and processes. Policies and procedures are documented, and cybersecurity activities are now managed and repeatable.
- Documented Procedures: Cybersecurity processes are formalized, documented, and shared across the organization.
- Consistent Application: Security practices are applied more consistently across different teams and departments.
- Basic Governance: The organization establishes oversight mechanisms, ensuring that cybersecurity activities are carried out as planned.
Level 3: Defined
At level 3, the organization has developed a more mature cybersecurity strategy with comprehensive policies and procedures that are consistently followed throughout the organization, but implementation is not automated:
- Proactive Risk Management: The organization moves beyond compliance-based security and begins to actively identify and mitigate risks.
- Established Cybersecurity Program: Cybersecurity practices are now embedded in the organization’s culture, and there’s a clear security governance structure.
- Metrics and Monitoring: Organizations begin tracking metrics related to cybersecurity performance and incident response, allowing for data-driven decisions.
Level 4: Quantitatively Managed
At level 4, the organization focuses heavily on measurement and data-driven improvement. This level emphasizes the use of performance metrics and risk analytics, with somewhat predicable results.
- Data-Driven Decision Making: Organizations at level 4 use quantifiable data to make informed decisions about their cybersecurity strategy.
- Continuous Improvement: Security processes are regularly reviewed and refined based on performance metrics and changing threat landscapes.
- Integrated Risk Management: Cybersecurity becomes an integral part of enterprise-wide risk management, with close collaboration between cybersecurity teams and other business units.
Level 5: Optimizing
The highest level of maturity, level 5, represents an organization that is at the forefront of cybersecurity capabilities. At this level, cybersecurity is ingrained in the organization’s culture, and the organization continuously adapts to evolving threats.
- Predictive Threat Modeling: Organizations at level 5 employ advanced threat intelligence and predictive analytics to anticipate future attacks and proactively defend against them.
- Fully Integrated Security Culture: Cybersecurity is fully embedded into the organization’s overall business strategy and culture. Everyone in the organization, including the supply chain and the larger ecosystem, is involved in maintaining cybersecurity.
- Innovation in Cybersecurity: At this level, organizations are not just following best practices but are leading the industry in developing new, innovative approaches to cybersecurity.
***
Leveling Up Your Maturity Model with C2A Security
The maturity levels range from basic, reactive cybersecurity practices to hyper-automated and proactive security postures. As an organization progresses through these levels, it not only strengthens its defenses but also:
- Reduces Risk: Advanced cybersecurity maturity means organizations can detect and respond to threats faster, preventing potentially catastrophic incidents.
- Improves Incident Response: With higher maturity, organizations are better equipped to handle incidents, minimize damage, and recover quickly.
- Fosters a Security Culture: A mature cybersecurity organization fosters a culture of security awareness across all employees, not just those in IT or security roles.
C2A Security helps organizations across four main domains:
Dynamic Risk Management & Risk Quantification
- Fully integrated throughout the product security lifecycle- Automating the identification, prioritization, and mitigation of software vulnerabilities based on the context of the cyber model.
- Utilizing intelligent and “live” risk calculation to maintain a continuous balance between security implementation, software development, and operations efficiency.
Cyber Model-Based Management & Automation
- Leveraging Dashboards and analytics for risk-based decision-making on product security cost, time to deployment, risk levels of fleets and components, supply chain response and efficiency, and much more.
Real-time Management & Workflows
- On multiple system elements and a centralized product – EVSec allows a team building a fully complex product to work simultaneously with teams in the organization or suppliers.
- Map all open-source components and software dependencies across all projects while allowing security teams instant visibility to all assets in seconds. The module also supports automated retrieval of CVEs.
- Leverage EVSec’s unique automation to easily monitor, identify, prioritize, and offer potential mitigations for vulnerable components when a new vulnerability is discovered.
Compliance and Regulation Automation
- Automating the creation of compliance work products for regulators, threat analysis and risk assessment, and the Cyber Security Management System (CSMS) required by the regulator in all product lifecycle stages.
**
EVSec Platform leverages a proprietary risk-based approach to product security, enabling organizations to achieve compliance in minimum time and cost while enhancing their overall cybersecurity posture. Schedule your exclusive product demo today.







