As the automotive industry transforms into software-oriented vehicles, ensuring robust cybersecurity has become a top priority. During EcoMotion Week in Tel Aviv this May, C2A Security held a Mobility Event for industry executives, investors, and media, featuring keynote talks from hacker Sick Codes, Foxconn Joe Cheng and C2A Security CEO, Roy Fridman.
Here are the highlights from Roy’s talk, as he discussed the rise of electric vehicles, generating new revenue streams through software and added-value services, tighter regulations, and why (we believe) security is THE facilitator for them all.
A paradigm shift: Cars evolving into software-driven computers on wheels
The automotive industry is in the midst of a significant transformation, moving away from its traditional hardware-centric approach and embracing a new era of software orientation. With groundbreaking technological advancements, cars rapidly evolve into sophisticated computers on wheels. This shift signifies a pivotal moment where software systems and connectivity take center stage, revolutionizing how we interact with and perceive automobiles.
Electric vehicles: Unveiling new challenges with advanced architecture, connectivity, and expanding charging infrastructure
The rise of electric vehicles (EVs) has introduced a fresh set of challenges for the automotive industry, stemming from their advanced architecture, heightened connectivity, and the rapid expansion of EV charging infrastructure.
EVs represent a paradigm shift in the transportation sector, driven by their eco-friendly nature and potential to reduce carbon emissions. However, their unique characteristics present both opportunities and hurdles that require careful consideration. The advanced architecture of electric vehicles, which includes high-voltage battery systems and intricate powertrain components, demands specialized expertise and infrastructure for manufacturing, maintenance, and repairs.
As the electric vehicle market expands, addressing these challenges will be crucial to unlocking the full potential of sustainable transportation and creating a seamless and reliable EV ecosystem.

Rising cybersecurity threats: Safeguarding EV charging stations
Rapid growth in the EV industry has also brought about a surge in cybersecurity threats, particularly concerning EV charging stations. With the growing integration of digital technologies and connectivity in charging infrastructure, malicious actors are targeting these systems to exploit vulnerabilities and gain unauthorized access.
The potential risks include unauthorized charging, data breaches, ransomware attacks, and even the compromise of the power grid.
To ensure the reliability, safety, and trustworthiness of EV charging networks, stakeholders in the automotive industry must prioritize cybersecurity measures, such as robust encryption protocols, regular vulnerability assessments, and strong authentication mechanisms, to thwart cyber threats and protect the integrity of EV charging infrastructure.
Evolving cybersecurity strategies for the software-driven future of the automotive industry
Manual processes and hardware-focused strategies, effective in the hardware-driven era, are struggling to keep pace with software-driven vehicles’ increasing complexity and interconnectedness.
The evolving nature of automotive systems demands a proactive and adaptive cybersecurity approach that integrates advanced technologies such as artificial intelligence, machine learning, and real-time monitoring.

The imperative role of automation in advancing software-defined vehicles
By leveraging automation tools, automotive manufacturers can accelerate the development lifecycle, reduce manual errors, enhance collaboration among teams, and achieve higher levels of efficiency and productivity.
Ultimately, embracing automation paves the way for the realization of innovative and cutting-edge software-defined vehicles that deliver enhanced functionality, safety, and user experiences while minimizing development costs and time-to-market.
Embracing cybersecurity regulations in the automotive industry
Adhering to cybersecurity regulations protects customers and their data and ensures the integrity and reliability of vehicles and charging infrastructure. Going beyond mere compliance, automotive companies proactively prioritizing cybersecurity can gain a significant competitive edge.
By implementing robust security measures, conducting thorough risk assessments, and staying ahead of emerging threats, these companies can build trust and confidence among consumers, regulators, and industry stakeholders.

The new currency of value: Trust
Trust in cybersecurity is poised to become a crucial factor in measuring the value of automotive products.
With vehicles evolving into software-driven machines on wheels, customers’ concerns about the security and privacy of their personal data, as well as the safety and reliability of their vehicles, are at an all-time high. As a result, trust in cybersecurity will not only impact the perceived value of automotive products but also influence purchasing decisions, brand loyalty, and overall customer satisfaction.
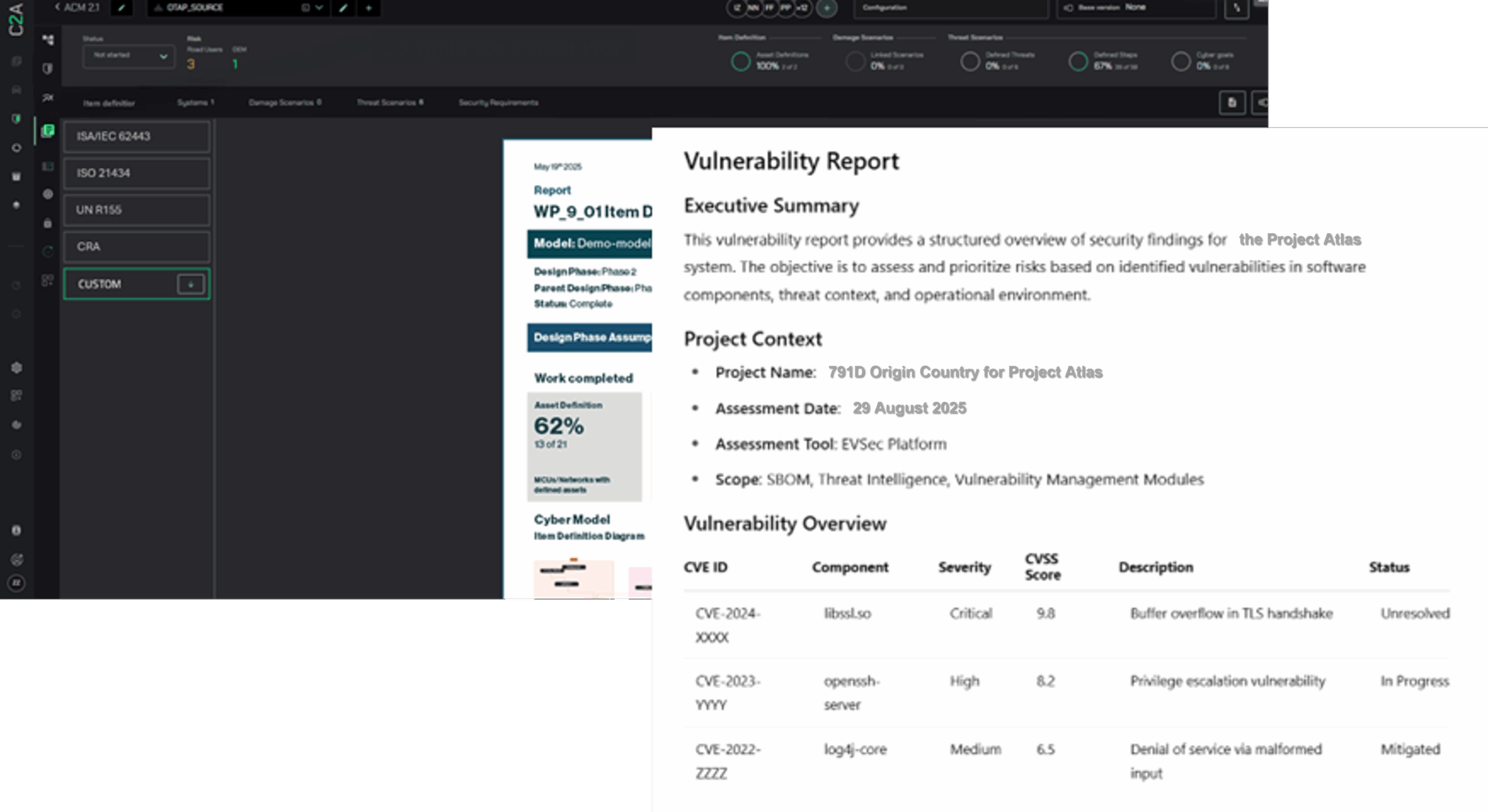
Enhancing cybersecurity with C2A Security’s EVSec platform
C2A Security’s innovative platform, EVSec, presents a cutting-edge solution for managing and mitigating cybersecurity risks in EVs and their associated charging infrastructure.
By leveraging automation and scalability, EVSec offers a comprehensive suite of tools and technologies designed to detect, prevent, and respond to cyber threats effectively.
With its advanced capabilities, the platform empowers automotive manufacturers, charging station operators, and other stakeholders to proactively safeguard against potential vulnerabilities, including unauthorized access, data breaches, and malicious attacks.
Through its automated security management, real-time monitoring, and adaptive defense mechanisms, the platform plays a pivotal role in ensuring the resilience, integrity, and trustworthiness of electric vehicles and the supporting charging infrastructure, contributing to the sustainable growth of the EV ecosystem.
Empowering automotive cybersecurity: C2A Security’s tools and solutions drive efficiency, creation of new revenue streams, and quality.
C2A Security, a leading provider of automotive cybersecurity solutions, equips companies with tools and solutions that optimize their cybersecurity efforts.
Recognizing the complex and evolving nature of automotive cybersecurity, C2A Security aims to empower companies by helping them deliver secure products faster, and generate new software-based revenue streams while enhancing their overall secure posture.