By Gilad Bandel, VP of Cybersecurity
The global transition towards renewable energy is accelerating, with solar power at the forefront of this shift. Due to the IT-OT convergence, solar infrastructure becomes increasingly connected to the public internet for monitoring and control. Therefore, it increases the attack surface and opens new vulnerabilities.
Recent studies have revealed that tens of thousands of such solar power systems worldwide are exposed to the internet, creating an expansive attack surface for cybercriminals. These vulnerabilities, particularly in inverters, monitoring platforms, and control systems, can disrupt energy production, destabilize local grids, and compromise safety. These risks must be addressed proactively throughout the infrastructure lifecycle, from development to deployment.

For illustration, consider the recent power grid meltdown in the Iberian Peninsula. Though this event was not cyber-related, the implications of a cyber-attack caused by such a case are devastating. A deliberate incident will surely be more severe since it will be staged and launched by malefactors with damaging intentions, making it much harder to identify the multiple causes that might be delayed and prolong the time for completing the repairs until full system functionality restoration.
Identifying and Mitigating Risks: The Core of Cybersecurity for Solar Systems
The risks associated with unsecured solar systems are multifaceted, extending from operational disruptions to safety hazards. Unauthorized access to solar power management systems can lead to financial losses, service outages, and even physical damage to infrastructure, such as overvoltage commands that could potentially ignite fires. Furthermore, once an attacker breaches a system, they could use it as an entry point to other critical systems, posing significant risks to the broader energy grid.
Given these stakes, implementing a robust risk management process is crucial. A proactive approach involves several key steps:
- Asset Discovery: The first step is to identify and catalog all components within the solar power infrastructure. This includes understanding the hardware, software, and network dependencies that could be vulnerable.
- Threat Modeling: Analyzing potential attack vectors is essential once the assets are mapped. For example, exposed APIs, insecure communication protocols, and default credentials are common vulnerabilities in solar systems that must be addressed before deployment. The feasibility of such an attack must be considered when calculating and mitigating the emerging risks.
- Impact Analysis: Assessing the potential impact of an attack on financial, operational, and safety aspects allows for the prioritization of security measures to reduce overall risk. Potential damage severity is another consideration in risk estimation.
Continuous Vulnerability Management: Keeping Systems Secure Through Development and Deployment
Security must be integrated by design throughout the lifecycle of solar power systems, starting during development. This includes adopting secure coding practices, implementing encrypted communications, BOM & vulnerability management, and performing regular security testing, such as Static and Dynamic Application Security Testing (SAST/DAST) for firmware. Early detection, shift left, and remediation of vulnerabilities ensure systems are built with security in mind, reducing the cost of fixing issues.
In-field protection is just as important. After deployment, solar systems must continuously monitor to identify newly discovered vulnerabilities and threats that could enable a cyberattack. In addition, anomaly detection tools can alert operators to potential issues in real-time. At the same time, secure patch orchestration systems ensure that firmware and software updates can be deployed efficiently without disrupting energy production.
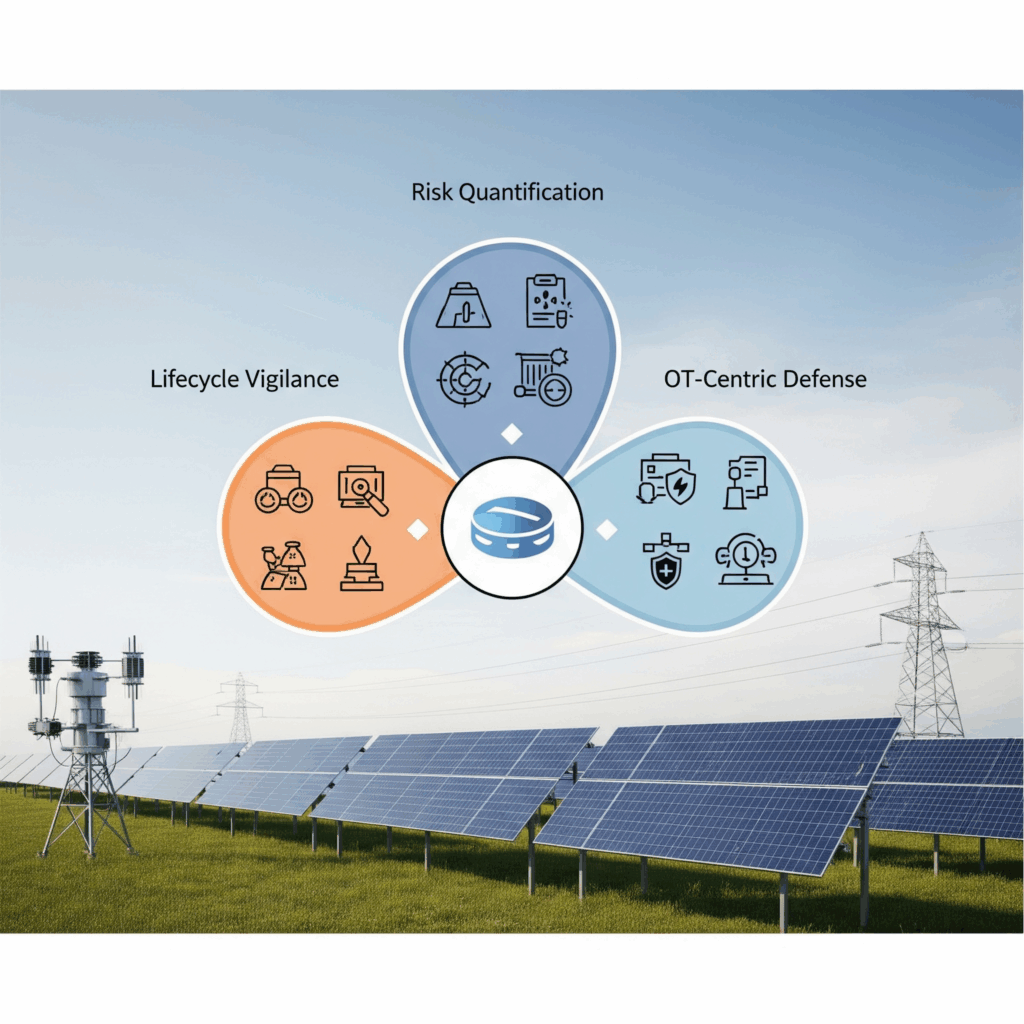
How C2A Security Can Help Mitigate These Risks
C2A Security EVSec platform offers a holistic and comprehensive cybersecurity approach tailored to the unique challenges of the solar industry throughout the whole lifecycle. By systematically embedding security at every stage of the product lifecycle and managing the entire supply chain, C2A ensures that risks are mitigated early on and throughout the operational life of solar systems. Here’s how C2A Security’s solutions can help organizations protect their solar assets:
- Risk Quantification and Prioritization: EVSec’s automated risk-based management tools help organizations create a cyber-model for dynamic threat modeling, security posture, and identify vulnerabilities in their products, networks, and firmware, allowing them to prioritize remediation efforts based on impact severity.
- Lifecycle Vigilance: EVSec’s platform supports continuous in-context vulnerability management and mitigation prioritization, ensuring that security measures evolve alongside the threats targeting the solar infrastructure. An extensive Threat Intelligence function supports this process.
- OT-Centric Defense: With a focus on Operational Technology (OT), C2A’s solutions provide tailored protection for critical infrastructure, ensuring availability while safeguarding against cyber threats in a zero-trust environment.
Building a Resilient Future for Solar Energy
The growing connectivity of solar power systems presents clear risks, but it also provides an opportunity to strengthen the resilience of the energy infrastructure. Solar power systems can be protected against the growing tide of cyber threats and automation-based compliance with global standards and regulations by adopting a comprehensive, proactive approach to risk management, continuous vulnerability monitoring, and secure operations.
C2A Security’s expertise and the industry-awarded AI-driven EVSec platform provide the means necessary to safeguard these systems, from seamless integration into the CI/CD pipeline and DevSecOps orchestration through deployment and the field. This drastically reduces the costs, time to market, and work effort required compared to other alternatives. For organizations seeking to enhance their cybersecurity posture in the renewable energy sector, proactive risk management is no longer optional—it’s essential.
Contact C2A Security today to learn how we can help secure your solar infrastructure and ensure long-term operational resilience: https://c2a-sec.com/schedule-demo/.







