The healthcare sector is facing growing risks from the interconnected Internet of Medical Things (IoMT), where vulnerabilities in a single device can expose entire networks to breaches. These risks extend beyond patient data breaches to include disruptions in clinical workflows, misdiagnosis of patient treatment, device malfunctions, and other harm to patient safety.
Medical device manufacturers (MDMs) face parallel challenges, particularly as regulators increase pressure on cybersecurity and safety requirements, including FDA approval times and clearance for 510(k) premarket submissions, to avoid production lifecycle delays and potential recalls due to non-compliance or post-market security vulnerabilities.
Here are 50 alarming statistics that every healthcare security professional and MDM should know about in 2025.
Interconnected Medical Device Threats on the Rise
- 93% of organizations have confirmed KEVs and insecure internet connections for IoMT.
- 8% of imaging systems carry KEVs linked to ransomware.
- 75% of healthcare organizations increased their medical device and operational technology security budgets over the past 12 months, but only 17% feel extremely confident in their ability to detect and contain attacks on medical devices.
- 99% of hospitals and HDOs manage IoMT devices with known exploited vulnerabilities (KEVs).
- The FBI’s Cyber Division reported that 53% of networked medical devices have at least one known critical vulnerability.
- 10% of surgical devices had vulnerabilities with high EPSS scores.
- 21% of medical devices are secured by weak or default credentials.
- 14% of connected medical devices run on unsupported or end-of-life operating systems.
- 99% of healthcare organizations are vulnerable to publicly available exploits.
- 31% of healthcare organizations that experienced medical device cybersecurity incidents faced up to 12 hours without critical systems.
- 42% of medical device professionals said that developing and maintaining secure code in apps connected to medical devices was their greatest challenge.
- 55% of medical device manufacturers delayed releases caused by software issues found during testing.
- 36% of all identified exposures are DICOM services.
- 52% of electronic health record systems (EHR) experienced the highest compromise rate.
- 11% of the applications identified across all asset categories were open-source software.
- 20% of pump controllers had critical vulnerabilities with extreme exploitability.
- Over 76% of medical devices are impacted by supply chain vulnerabilities.
- DICOM (Digital Imaging and Communications in Medicine) exposure has grown by 246% since 2017.
- 1 in 5 connected medical devices run on unsupported operating systems.
- Only 13% of medical devices support endpoint protection agents.
The Impact of Healthcare-Related Data Breaches
- The average cost of a healthcare data breach is $7.42 million (~24% YoY decrease from 2024).
- Over 305 million patient records were exposed in 2024 (26% YoY increase from 2024).
- Healthcare organizations took an average of 205 days to report incidents in 2024.
- As of August 2025, there are 1.2 million internet-connected healthcare devices and systems publicly accessible online, including MRI scanners, X-rays, CT devices, DICOM viewers, blood-test systems, and hospital management platforms.
- In June 2025, a misconfigured MongoDB database exposed over 8 million patient records, including data from 2.7 million U.S. patients.
- 67% of healthcare organizations were hit by ransomware in 2024.
- 77% of healthcare organizations were targeted by ransomware in the past year, with 53% paying the ransom.
- Change Healthcare experienced the most significant data breach of 2024, impacting over 190 million individuals. The BlackCat/ALPHV ransomware group received a $22 million ransom for the attack.
- Healthcare represents 17% of all ransomware attacks across industries.
- 50% of healthcare organizations lack confidence in detecting and resolving data breaches.
- 42% of healthcare organizations lack policies for unauthorized data access prevention.
- Over half (54%) of healthcare security professionals believe their organizations are vulnerable or highly vulnerable to a ransomware attack.
- In H1 2024, there were 13 reports of data breaches involving the loss or theft of electronic devices containing ePHI and paper/records.
- The mean cost in healthcare organizations to recover from a ransomware attack was $2.57 million in 2024.
- Claroty’s Team82 discovered that 20% of hospital information systems contain KEVs linked to ransomware.
- 74% of hospitals relying on legacy systems experienced at least one cyber incident in the past year.
- Only 43% of healthcare security professionals upgraded legacy technology post-ransomware attack.
- 68% of healthcare security professionals said their organizations experienced a supply chain attack in 2024.
Healthcare Regulatory Concerns and Rule Changes
- The 2025 HIPAA Security Rule introduces a mandate requiring the implementation of Multi-Factor Authentication (MFA) across all access points to electronic Protected Health Information (ePHI) to strengthen cybersecurity efforts.
- The HHS Office for Civil Rights (OCR) now expects healthcare providers to produce full documentation of their compliance activities within 10 business days of notice of the date on the information request.
- The OCR fined 4 HIPAA-regulated entities for HIPAA violations and imposed $4.79 million in financial penalties in H1 2024.
- Montefiore Medical Center settled a $4.75 million HIPAA penalty for a malicious insider incident, the most significant imposed penalty in H1 2024.
- Only 31% of compliance, risk, and legal professionals felt prepared to meet future compliance and risk challenges.
- 52% of healthcare CISOs are extremely concerned about the pace of regulatory change.
- 73% of healthcare organizations say new FDA cybersecurity guidance and EU cybersecurity regulations are already influencing their procurement decisions.
The Medical Device Manufacturer (MDM) Threat Landscape
- There were 708 medical device recalls in Q1 2025.
- FDA approvals for high-risk medical devices fell to a 10-year low in Q1 2025, with only nine approvals.
- There was a 5.9% decline YoY in average days to submission decision for 510(k)s.
- In February 2024, the FDA issued an advisory letter to the medical device industry, emphasizing the critical importance of scrutinizing third-party-generated data in premarket submissions.
- The FDA has 90 calendar days to review 510(k) submissions, which may be delayed up to 180 days if additional information is requested.
- Out of the total 903 AI-enabled medical devices cleared through August 2024, 43 (4.8%) were recalled, and the average time between approval and recall was 1.2 years.
- 19% of Class I recalls across all medical devices involved implantable devices in 2024.
- 11% of device recalls involved Class 1 recalls in 2024.
- Medical device recalls increased 8.6% YoY in 2024 over 2023, with 1,059 devices recalled.
- Device failure accounted for 11.1% of all recall events, making it the leading cause.
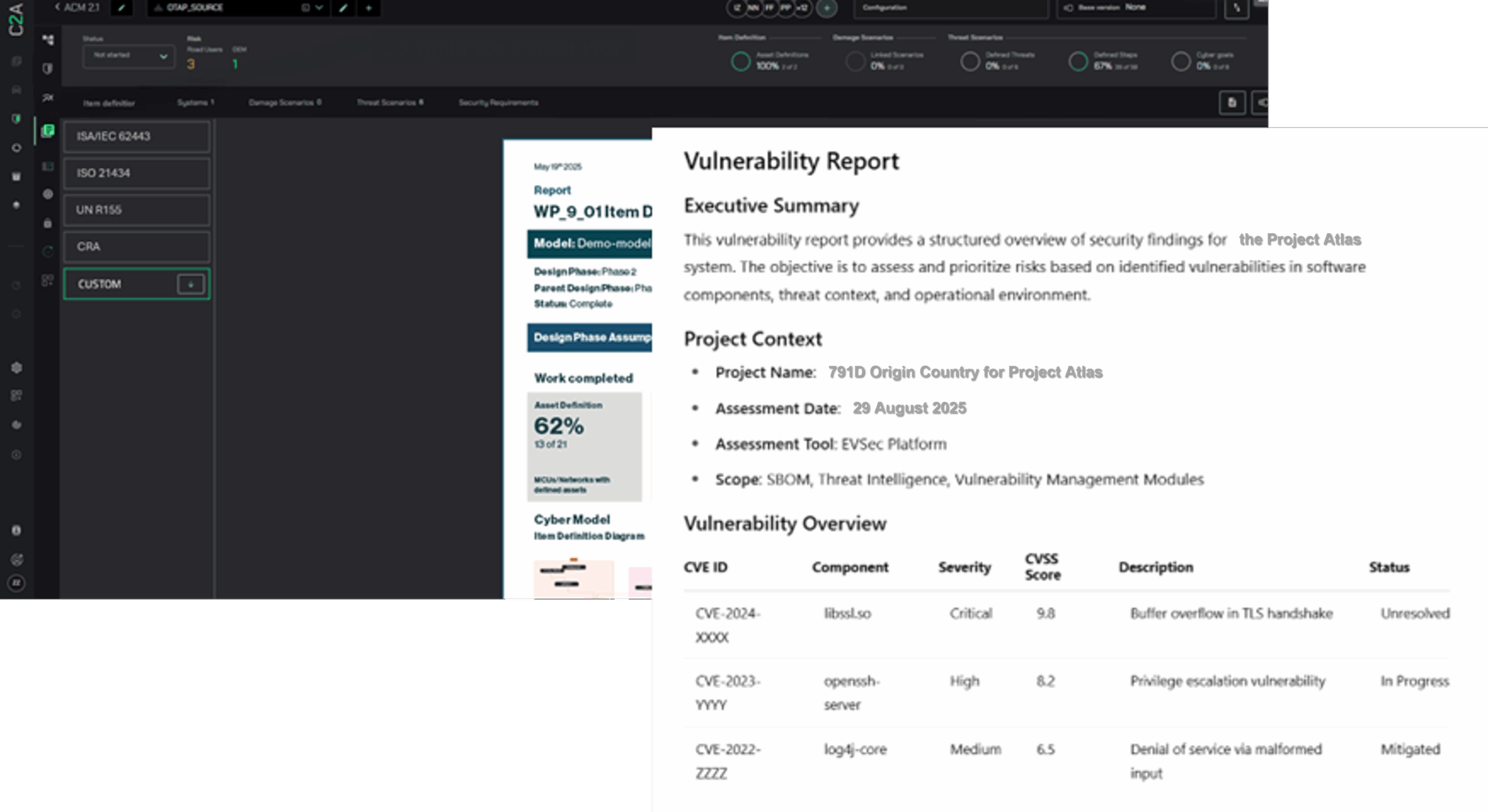
How C2A Security Protects Medical Devices & Critical Infrastructure
Healthcare organizations and medical device manufacturers can no longer rely on vendor patch cycles to secure interconnected devices. They need proactive, context-driven protection that reduces risk across the entire lifecycle.
C2A Security’s EVSec platform provides:
- SBOM/HBOM-based risk intelligence to uncover vulnerabilities at the component and firmware level, ensuring evidence-backed prioritization and faster remediation.
- Continuous device risk monitoring to detect abnormal network traffic and unauthorized data exfiltration, reducing dwell time and lateral movement.
- Supplier and software provenance profiling to enforce accountability across OEMs and their supply chain, strengthening compliance and resilience.
- Coordinated incident response workflows to contain and recover from attacks quickly, shortening detection and response times without disrupting clinical operations.
- Compliance automation to meet FDA, HIPAA, NIS2, EU RED, and IEC/ISA 62443 requirements while reducing audit preparation and submission delays.
- Human-in-the-loop explainability to provide context-driven triage with clear, defensible remediation steps for engineering teams and regulators.
With EVSec, healthcare providers and manufacturers can minimize vulnerabilities, prevent lifecycle delays, and defend critical infrastructure against ransomware and supply chain attacks.
Schedule a demo to learn more.