Tool Overload and Fragmentation: Why Point Solutions Are Ineffective Today
Cyber threats are becoming increasingly difficult for security professionals to manage. Fragmented point solutions can’t keep up, leaving blind spots across identities, endpoints, and cloud workloads. With the recent surge in nation-state actors leveraging LLMs to target critical infrastructure, security leaders are losing confidence in the effectiveness of their existing tools.
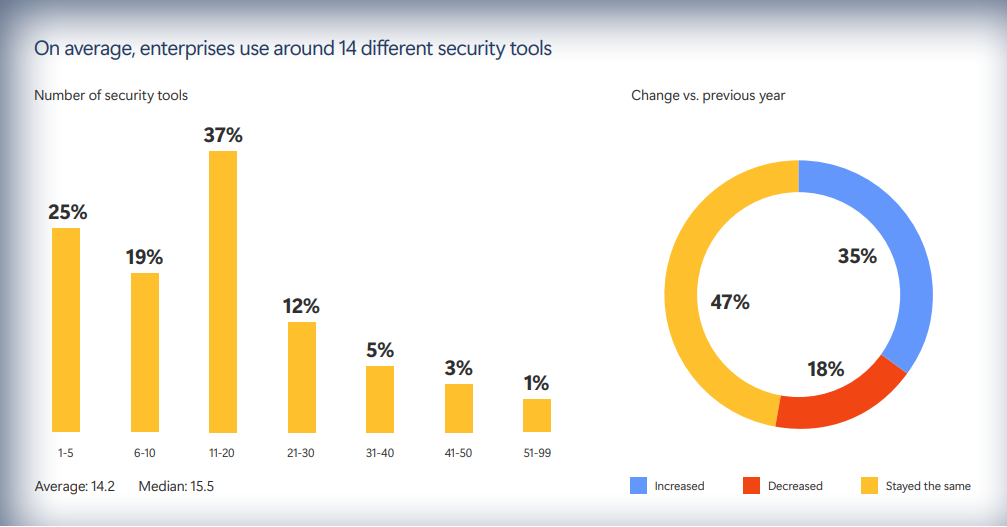
Traditionally, that meant that SecOps and other security leaders had to increase the number of tools to combat the growing threats. A Microsoft report found that, on average, enterprises use around 14 different security tools. In connected and regulated industries (automotive, medical, industrial/OT, IoT), these blind spots extend to firmware, supply-chain components, and fielded devices – areas where traditional IT-only tools have limited reach.
However, having more tools does not necessarily translate to reduced threat surfaces or improved security postures. Costs aside, they are also counterproductive to threat mitigation, assuming all systems and tools integrate without friction.
Microsoft found that organizations with more tools reported a higher average number of security incidents (15.3 vs. 10.5 for organizations with fewer tools). Limited visibility from fragmented point solutions only adds complexity to threat detection and incident response, creating more noise from alerts and further delaying mitigation efforts. For product companies, fragmentation also breaks traceability across SBOM/HBOM, OTA updates, and incident reporting – making compliance with frameworks like ISO/SAE 21434, UN R155, CRA/NIS2, and U.S. DoC 791D harder to prove.
Enter the use case for unified security platforms.
This article will explore the value of a unified security platform and how security leaders can reduce costs while successfully transitioning from a best-of-breed strategy to a consolidated approach. We’ll focus on unifying IT + OT + IoT data with product-lifecycle context (design → build → deploy → in-field), so organizations can move from detection to compliant remediation at scale.
The Real Value of a Unified Security Platform
Data integration plays a significant role in any successful threat intelligence program.
A SIEM can generate massive volumes of raw data logs with no business context. At the same time, an XDR agent might only display the event activity occurring on its endpoint, leaving out critical information from identities, SaaS applications, and cloud workloads. Equally, OT/IoT visibility tools often miss software provenance, vulnerability posture, and policy violations tied to SBOMs, firmware, and third-party components.
Fragmented point solutions offer partial visibility into the true threat surface. Something as trivial as a misconfigured cloud policy or an unverified third-party device can expose the organization to bigger risks and potential security breaches. Add to that unsigned firmware, outdated ECU/PLC images, or suppliers without attestations, and the blast radius extends from the cloud to the vehicle or factory floor.
Unified security platforms centralize exposure management and improve visibility across devices, identities, applications, data, and multi-cloud environments. For connected products, “unified” also means mapping software origin (SBOM/HBOM), supplier risk, and field telemetry into one risk graph. They can effectively ingest threat intelligence data from existing tools, such as SIEM, SOAR, and XDR, to help organizations prioritize threat mitigation efforts.
They also help security teams avoid silos created by fragmented or poorly integrated point solution tools. Analysts quickly become overwhelmed by the volume of false positives, which slows investigations and may lead to alert fatigue, allowing high-risk threats to evade detection. In fact, 57% of organizations report losing valuable time during investigations due to gaps in their data management strategies. The same survey found that 59% of security professionals say adopting a unified platform has sped up incident response. The benefits of a unified platform grow exponentially when AI is introduced to automate incident response and threat hunting investigations. AI must be grounded in business and regulatory context (e.g., safety-critical ECUs, regulated components, recall exposure) to drive actionable triage—not just more alerts.
Fragmented Point Solution Puzzle Complete: The Role of AI in a Unified Platform
Microsoft research found that 91% of security leaders who use best-of-breed solutions still prioritize moving to vendor consolidation because of AI’s role in streamlining security operations.
Why is this so important?
Nation-state actors and ransomware groups have begun leveraging AI to deploy sophisticated malware to target critical infrastructure, OT systems, and interconnected networks. A separate study on 2,800 ransomware incidents found that AI was leveraged in 80.83% (2,272) of the attacks, with the LockBit ransomware group accounting for the largest share at 815 incidents.
On the opposite end of the security spectrum, AI has tremendous benefits for SecOps. A report showed that 76% of SecOps teams claimed that AI makes their roles easier while saving security teams an average of 12 hours per week on manual processes. Combined with AI capabilities, that unified security platform can automate workflows and triage, enrich alerts with context, and drastically reduce MTTR rates.
Here’s how it can be achieved.
AI and machine learning (ML) can process and continuously learn from trillions of signals, enabling SecOps to detect behavioral anomalies and integrate with existing SIEM, SOAR, and XDR tools to enhance threat mitigation strategies. SecOps and SOC teams can leverage AI agents to query multiple data sources and gather historical evidence from past security cases to identify patterns and generate context-driven responses. For connected products, agents should also reason over SBOMs, supplier attestations, OTA rollout plans, and in-field telemetrics to block unsafe deployments, recommend safe phased rollouts/rollbacks, and generate audit-ready evidence.
It’s no surprise that 66% of SecOps teams are actively investing in AI for cybersecurity, with another 22% currently piloting AI projects.
The returns of a unified platform with AI capabilities are quite evident.
According to IBM, organizations can increase their return on security investment (ROSI) by 40% or more and reduce data breach costs by at least 18% through security automation tools. SecOps can confidently present these findings to draw support from executive leadership and influence cybersecurity purchasing decisions for a unified platform.
In regulated sectors, automation also shortens compliance cycles (DoC 791D/Rule 791D, ISO/SAE 21434, UN R155, CRA/NIS2) by auto-producing evidence, traceability, and incident timelines.
Security teams protecting critical infrastructure benefit by consolidating threat intelligence across multiple tools into a holistic view. Shifting from a reactive, best-of-breed approach to a proactive security solution is only possible through unified, AI-enabled platforms. The most mature programs explicitly bridge IT and OT, standardizing workflows between SOC and product/engineering teams.
C2A Security – The Context-Driven Product Security Platform
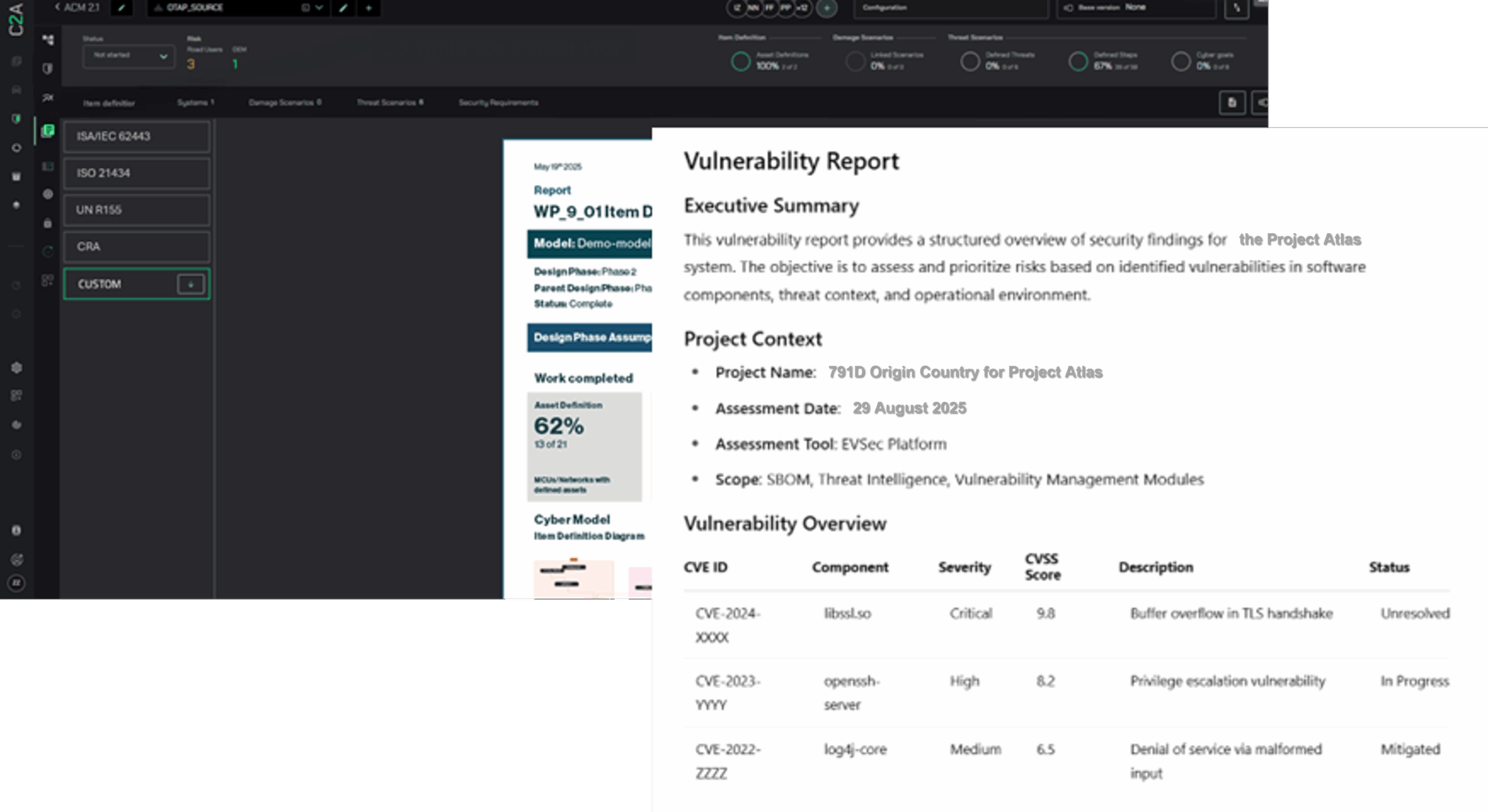
Point solutions leave critical gaps in an organizational supply chain and data silos across teams. EVSec is an AI-based, context-driven product security orchestration platform that provides complete visibility into an organization’s threat surface. Unlike IT-only solutions, EVSec unifies product-lifecycle context (design, build, test, deploy, in-field) with IT/SOC telemetry to drive decisions that are both secure and compliant.
EVSec goes beyond IT/enterprise security by also addressing embedded and critical infrastructure ecosystems, where fragmented tools can limit visibility and coverage. This includes SBOM/HBOM ingestion at scale, supplier risk mapping, contextual vulnerability triage, and OTA safety (staged rollout, rollback, and anomaly detection).
Enables security leaders to automatically and continuously identify, prioritize, and mitigate security vulnerabilities with enriched context, while unifying fragmented supply chains. EvSec empowers your SOC to focus on the most critical events with actionable data for better detection and optimized threat mitigation. It also automates compliance evidence for ISO/SAE 21434, UN R155, CRA/NIS2, and U.S. DoC Rule 791D – producing audit-ready reports and end-to-end traceability.
Schedule a demo to learn how C2A Security can help you smoothly transition from point solutions to an orchestration-based approach.