Risk assessments, which are part of the vulnerability management process, are one of the core activities of professional cybersecurity teams. The first time a cybersecurity risk assessment is conducted is at the very first stage of a vehicle’s lifecycle. When a new vehicle is being designed, automotive manufacturers perform a Threat Analysis and Risk Assessment (TARA), then apply countermeasures to address those vulnerabilities. Once manufacturers are equipped with the results, they can define their cybersecurity concept, refine the cybersecurity requirements, and develop a cyber secure design of the vehicle.

With the increasing connectivity and complexity of vehicles, the automotive industry faces a new challenge — conduct assessments on an ongoing basis.
From a risk mitigation perspective, the faster an organization can perform a cybersecurity assessment, the faster the necessary improvements can be put into place. With the increasing connectivity and complexity of vehicles, the automotive industry faces a new challenge — not only do OEMs and suppliers need to conduct initial cybersecurity risk assessments, they also need to conduct assessments on an ongoing basis, which is currently difficult to achieve quickly and efficiently. A firm and efficient risk assessment process is what provides the foundation for efficient automotive cybersecurity lifecycle management.
Time is of the essence for risk assessment, but how long does the typical risk assessment process take?
Risk assessment is a lengthy, multi-step process that may require the attention of a variety of players to account for different factors. Based on the risk assessment’s results, manufacturers then need to create a cybersecurity incident response plan, conduct required maintenance if needed, then return the vehicle to its secured state.
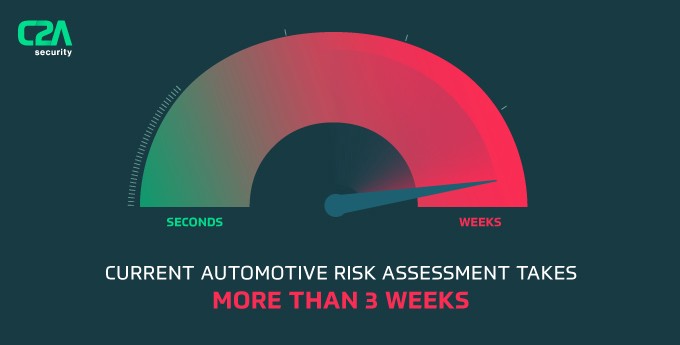
According to a recent market research survey of OEMs and tier 1 suppliers conducted by C2A Security, 56% of participants acknowledged that their organization’s risk assessment process takes more than three weeks.
According to a recent market research survey of OEMs and tier 1 suppliers conducted by C2A Security, 56% of participants acknowledged that their organization’s risk assessment process takes more than three weeks. Since this practice needs to be recurring, the current timeline is not sustainable. Automotive companies must have a system in place that allows them to quickly identify threats and risks on an ongoing basis, before incidents spiral out of control. They need to be able to quickly offer critical solutions that match the fast-paced changes to threats and vulnerabilities.
What’s the hold-up?
One essential piece that enables quick and accurate risk assessments is visibility into cybersecurity statuses and improvements throughout the supply chain. Full transparency throughout a vehicle’s supply chain allows all the components of the vehicle to be accounted for, and assessments should be performed throughout a vehicle’s lifecycle on a consistent basis.
However, this doesn’t appear to be happening at scale because there are significant barriers to achieving quick and efficient risk assessments. C2A Security’s market research found that more than 50% of respondents believe coordination between different entities is the biggest impediment to timely risk assessment processes. They acknowledged that communication and coordination between internal and external teams was often highly fragmented.
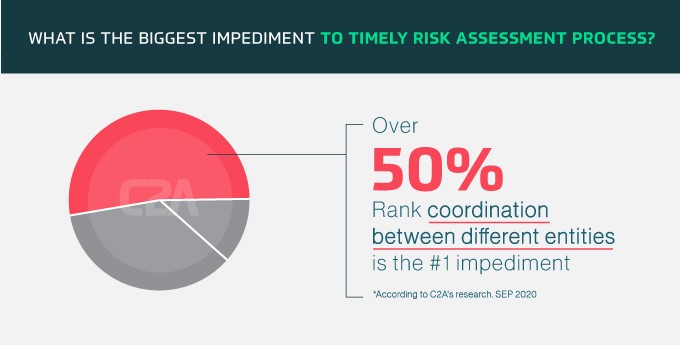
Additionally, 35% of survey participants said they lack the tools required for streamlining and automating the security lifecycle management process, which presents a roadblock for completing timely risk assessments. It’s clear that the industry needs to streamline security lifecycle management to maintain a strong security posture across all the various vehicle makes and models, from design to production to maintenance and every step in between. Digitized tools and solutions that can help streamline this process should be deployed to assist OEMs and suppliers communicate information more freely, so they can perform cybersecurity risk assessments more efficiently.
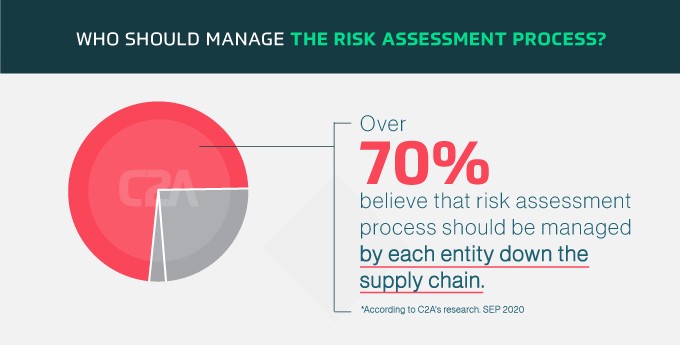
OEMs are not solely responsible for cybersecurity risk assessments
While it’s widely agreed that OEMs should own the risk assessment process, our research indicates that this notion is expanding. Cybersecurity is a shared responsibility and more than 70% said they believe the risk assessment process should be managed by each entity in a vehicle’s supply chain. Further, communicating vulnerabilities to all partners when identified is key to ensuring fast resolutions.
How can we do better?
With the much-needed changes in the regulatory environment for automotive cybersecurity finally here in the new ISO 21434 standard and UNECE WP.29, the clock is ticking for the entire automotive ecosystem to act. The survey findings reinforced that visibility and traceability are integral to the implementation of current and future cybersecurity standards. Without it, it’s nearly impossible to conduct a risk assessment in a timely manner. The automotive industry should encourage the development and adoption of digital solutions that provide full-spectrum visibility. These solutions will help better manage modern vehicle architecture and significantly speed up the reaction to attacks for the entire supply chain.
There is a true need for an orchestration layer that streamlines the automotive manufacturers’ management and ensures end-to-end, comprehensive, and structured organizational processes.
Currently, improving coordination between the internal and external teams responsible for ongoing risk assessments is a significant challenge for automotive manufacturers. There is a true need for an orchestration layer that streamlines the automotive manufacturers’ management and ensures end-to-end, comprehensive, and structured organizational processes.
Fortunately, new digital solutions are available to help automakers and tier 1 suppliers overcome the current roadblocks to achieving end-to-end cybersecurity and industry resilience, and the industry should encourage the development and adoption of these tools to ensure the protection of pedestrians, drivers, and passengers alike. An effective risk assessment process requires a connection between all entities involved to make sure that they are well coordinated to enable an efficient and swift risk assessment process. It is time for the industry to establish harmonized communication between all entities down the supply chain and create a uniform and effective channel for the risk assessment process that maintains in-vehicle cybersecurity throughout a vehicle’s lifecycle.






