It’s a time of change in the automotive industry. Connected Autonomous Vehicles (CAVs) host incredibly complex hardware and software architecture that are more vulnerable to cyber attack, requiring protection at every stage of the vehicle lifecycle. At the same time, OEMs, Tier-1s and industry suppliers are under pressure from international and regional regulators to incorporate new ISO 21434 standards and WP.29 R155 regulation without impacting vehicle development timelines — requiring them to scale cybersecurity capabilities across the supply chain, and ensure compliance in new vehicle models. Meanwhile, the United States’ NHTSA, ENISA in Europe, and member trade association AutoISAC have issued best practice guidelines for industry leaders to follow. In this series of blog posts, C2A Security will break down each compliance area for security professionals, beginning with standards and regulations – what does this mean for your organization, and how can security software support teams in their journey to compliant cybersecurity?
ISO 21434: after first steps to implementation, what’s next?
ISO 21434 exists to encourage automotive OEMs and suppliers to prioritize cybersecurity throughout the entire vehicle lifecycle, from ideation to retirement of a vehicle. It adopts a security-first mindset, laying out guidelines for each step of product development in a way not done in its predecessor, ISO 26262, which did not thoroughly address automotive cybersecurity concerns.
First, organizations should apply a gap analysis to compare current policies against ISO 21434 recommendations, identify weaknesses in cybersecurity protocols, and ultimately strengthen them to ensure compliance. Once complete, manufacturers and suppliers should refer to ISO 21434 terminology, objectives, requirements and guidelines to define new policies and implement new processes, manage risks, and embrace “security by design” not only in vehicle development – but across the entire culture of an organization.
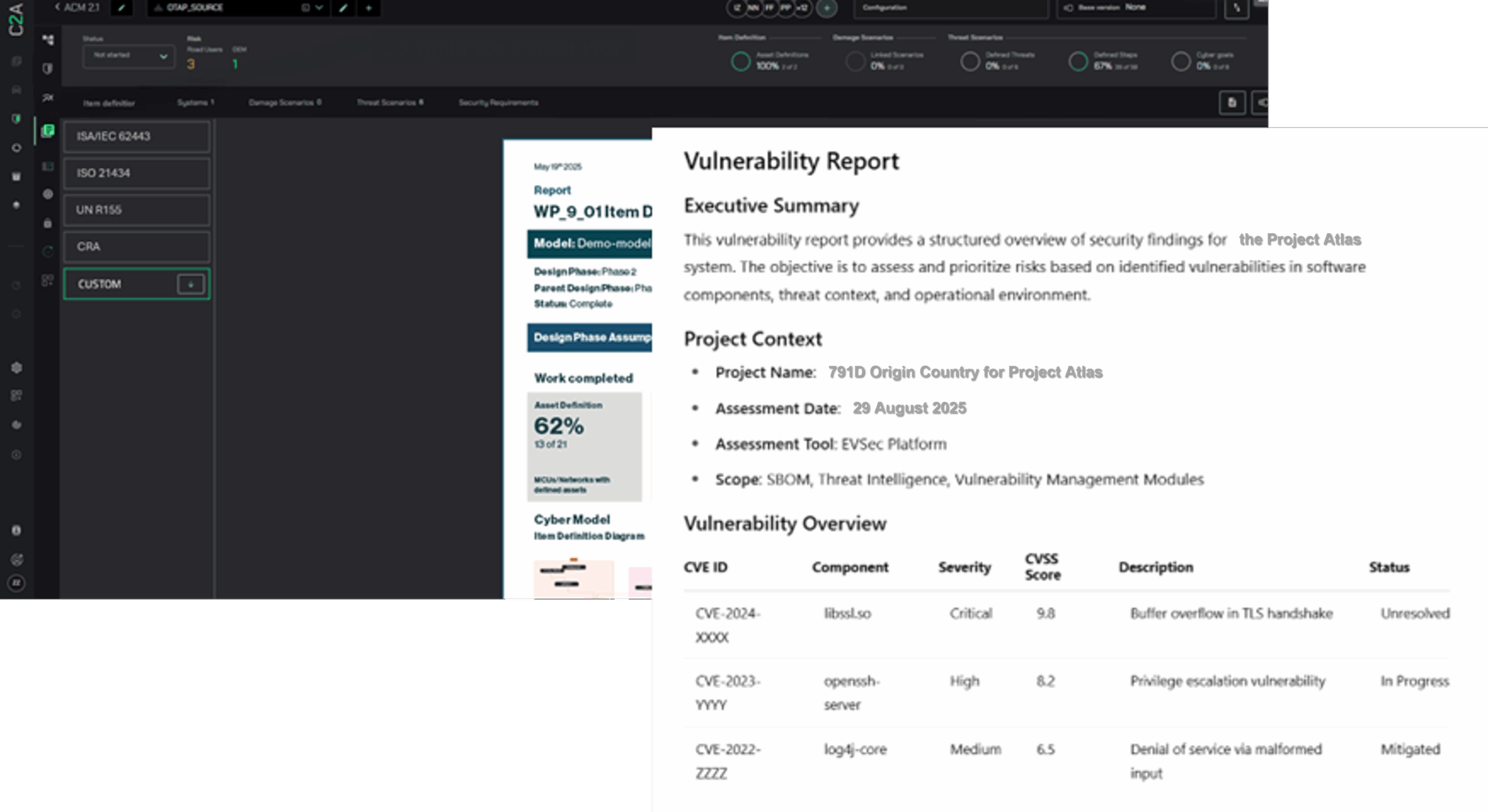
As ISO 21434 comes into force, cybersecurity management systems (CSMS), threat and risk assessments (TARA) and vulnerability will be top of mind for automotive security professionals. C2A’s AutoSec ANALYSIS supports this process, providing scalable, synchronized and sophisticated analytics for seamless scalability of ISO 21434 compliance across an entire organization. Now, OEMs and Tier 1s can rely on intuitive UI, automation and reuse capabilities throughout the cybersecurity lifecycle, delegate security work to internal and external stakeholders across the supply chain to deliver faster and more efficient compliance, and leverage AutoSec’s cutting-edge proprietary Risk Analyzer tool for balanced, secure and automated policy enforcement.
UNECE WP.29 regulation R155 for CSMS has been adopted – what does this mean for vehicle security?
The UNECE WP.29 regulation R155 for CSMS and Type Approval helps OEMs and suppliers better understand and respond to risks associated with new and emerging vehicle architecture. Rolled out to coincide with ISO 21434 regulation – discussed above – it proposes cybersecurity and software updates to manage vehicle cybersecurity risk, further emphasize a “vehicle by design” approach, detect and respond to security incidents across vehicle fleets, makes and models, and ensure that software updates are fully secure and do not compromise vehicle safety. It focuses on cybersecurity regulation in the development, production and post-production phases of the vehicle lifecycle, and is applicable to any manufacturer and supplier operating within the 54 countries that participate in the 1958 UNECE Transportation Agreements and Conventions.
The regulation stipulates that automotive organizations must, “include the capability to analyze and detect cyber threats, vulnerabilities and cyber-attacks from vehicle data and vehicle logs. This capability shall respect paragraph 1.3. and the privacy rights of car owners or drivers, particularly with respect to consent.” It emphasizes the following measures be considered:
- Preventing and detecting unauthorized access
- Protecting systems against embedded viruses/malware
- Detecting malicious internal messages or activity
In addition to CSMC, TARA and vulnerability management, it calls stakeholders to better prioritize IDS and runtime protection in cybersecurity protocols. C2A’s AutoSec ENDPOINT seamlessly protects the vehicle from supply chain attacks. Armed with detection, protection and compatible software, manufacturers and suppliers can now enable advanced BOM analysis to identify weaknesses before they’re exploited. They can protect against zero-day vulnerabilities across the entire supply chain, eliminating the need for frequent, unplanned OTA campaigns. Seamlessly integrated, AutoSec ENDPOINT protects compatibility, supporting stripped and non-stripped binaries, available for common automotive operating systems and chipsets.
Standards and regulations are ushering in a new era of Automotive Cybersecurity
Despite the massive overhaul, new regulation activities are bringing in positive change for automotive cybersecurity leaders. Manufacturers and suppliers are prioritizing cybersecurity as a safety issue in a way that they have not before. New regulation is offering an opportunity to cybersecurity teams to do away with old practices to implement a more methodical, systematic approach to cybersecurity across all organizations. While companies look to grapple with best practices, regulations and standards they’re confronted with — AutoSec ‘s automated capabilities will help to ease stress and alleviate pressure from security teams, creating room for more thorough implementation. Now, several services can be replaced with a single, unique, fully-customizable and centralized platform, all built with automotive-specific needs in mind. With clear guidance from regulators and standards bodies alike, the automotive industry can change for good. After all, secure vehicle architecture ultimately means one thing: mitigated risk to the public, creating safer roads for all.