C2A Security’s EVSec Platform is the 1st to support the generation of automated audit reports
China’s GB Standards, which entered into force in May 2022, outline cybersecurity requirements for vehicle systems’ design, development, production, and post-production processes. GB/T Standards mark voluntary standards in China, all covered by the Cybersecurity Working Group (WG). These standards aim to enhance vehicle cybersecurity by ensuring secure product design, threat monitoring, incident response, and recovery mechanisms. As of June 2024, there are several standards and research projects under the Chinese Automotive Cybersecurity Standard System.
***
For additional background into Chinese Regulations and Standards, watch our Unmasking Global Regulations webinar, featuring David Mor-Ofek and ThunderSoft’s Ouyang Zhe.
***
Applicable to all automotive manufacturers and suppliers operating in China, the standards are comprehensive and cover multiple aspects of automotive cybersecurity, including risk assessment, management processes, and technical measures for vehicles and their network operations. These standards are part of China’s broader efforts to regulate and protect the increasingly connected and technologically advanced automotive industry.
Fines and Implications for Non-Compliance
Non-compliance with the Chinese GB Standards for Vehicle Cybersecurity can result in significant consequences for automotive companies. The regulatory authorities in China have the power to impose fines and other penalties to enforce compliance. Potential implications for non-compliant companies include:
- Financial Penalties: Companies that fail to meet cybersecurity standards may face substantial fines.
- Reputational Damage: Non-compliance can lead to negative publicity and damage to the company’s reputation, potentially resulting in loss of customer trust and decreased sales.
- Operational Disruptions: Cybersecurity incidents resulting from non-compliance can cause operational disruptions, leading to increased costs and potential safety risks for vehicle users.
- Legal Consequences: In severe cases, non-compliance may result in legal action, including lawsuits and regulatory sanctions.
***
Chinese GB Standards Requirements
Under the Chinese GB Standards, car makers are expected to implement a range of cybersecurity measures to protect their vehicles and related systems. These include:
- Risk Assessment and Management: Companies must conduct regular threat analysis and risk assessments (TARA) to identify potential cybersecurity threats and vulnerabilities. They are required to implement appropriate risk management tools and strategies to mitigate identified risks and provide reports to the Government.
- Secure Software Development (SDLC): Ensure that software development processes incorporate cybersecurity best practices, including secure coding techniques and thorough testing for vulnerabilities.
- Data Protection: Implement robust data protection measures to secure sensitive information, including encryption, access controls, and secure data transmission protocols.
- Incident Response and Recovery: Establish and maintain incident response plans to detect, respond to, and recover from cybersecurity incidents effectively. This includes regular testing and updating of response plans.
- Supply Chain Security: Ensure that suppliers and third-party partners adhere to the same cybersecurity standards to prevent vulnerabilities from being introduced through the supply chain.
***
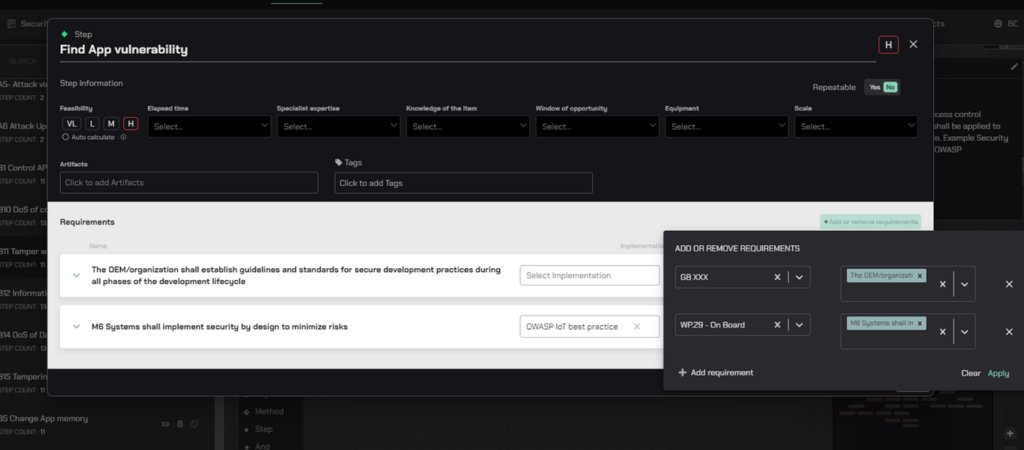
Leveraging EVSec Platform to Addresses Chinese GB Requirements
- Risk Management – Implement a structured risk management approach for automotive cybersecurity.
- Security and Operations by Design – Integrate security features at the design stage of vehicle development.
- Vulnerability Handling – Establish systems for monitoring and handling cybersecurity vulnerabilities.
- Supply Chain Security Posture – Develop and maintain the strategies, measures, and practices to protect all entities within your supply chain.
**
Risk Management
- Automated Risk Assessment: Utilize your platform’s advanced risk assessment capabilities to identify potential security vulnerabilities and threats in the communication interface between EVs and charging stations.
- Automated Risk Assessment: Utilize your platform’s advanced risk assessment capabilities to identify potential security vulnerabilities and threats in the communication interface between EVs and charging stations.
**
Security and Operations by Design
Agile Product Security Development and Operations that optimize the needed security controls for development teams and enrich operations with product security data for faster incident response:
- Data Breach Notification: Implementing processes for timely notifying the relevant authorities and affected individuals of data breaches.
- Develop and maintain an incident response plan to quickly address and mitigate any data breaches or security incidents.
**
Context-based BOM and Vulnerability Management
Risk-driven approach for automated BOM and vulnerability management, prioritizing true impact on the product and optimizing mitigation based on cost and time.
- Aside from our scanning tool, the EVSec platform can easily integrate with many commercial scanning or threat intelligence tools like Synopsys Black Duck, Upstream AutoThreat, or home-grown solutions, to enrich the vulnerability sources and create a comparison to validate whether the threat is relevant.
- The EVSec platform extensively gathers and integrates data from various vulnerability databases either directly or by integrating with other threat intelligence tools. Its purpose is to promptly alert users about any known vulnerabilities. Additionally, EVSec AutoSynth GenAI layer scours trusted sources for articles and news related to vulnerable software packages and potential security issues, ensuring that EVSec’s database remains up-to-date with the latest information.
- The configuration supports a flexible definition of initial risk. Users can use different configurations for each supplier and define the supplier’s risk calculation in its configuration.
**
Supply Chain Security Posture
- Develop and enforce comprehensive security policies that suppliers and partners must adhere to.
- Establish criteria for selecting and maintaining relationships with suppliers based on their risk score to your company.
- Make your supply chain an integral part of product security through information sharing and collaboration, for effective response and mitigation of vulnerabilities.
***
To learn more about EVSec Platform and to schedule an exclusive demo for your product security team, click here.