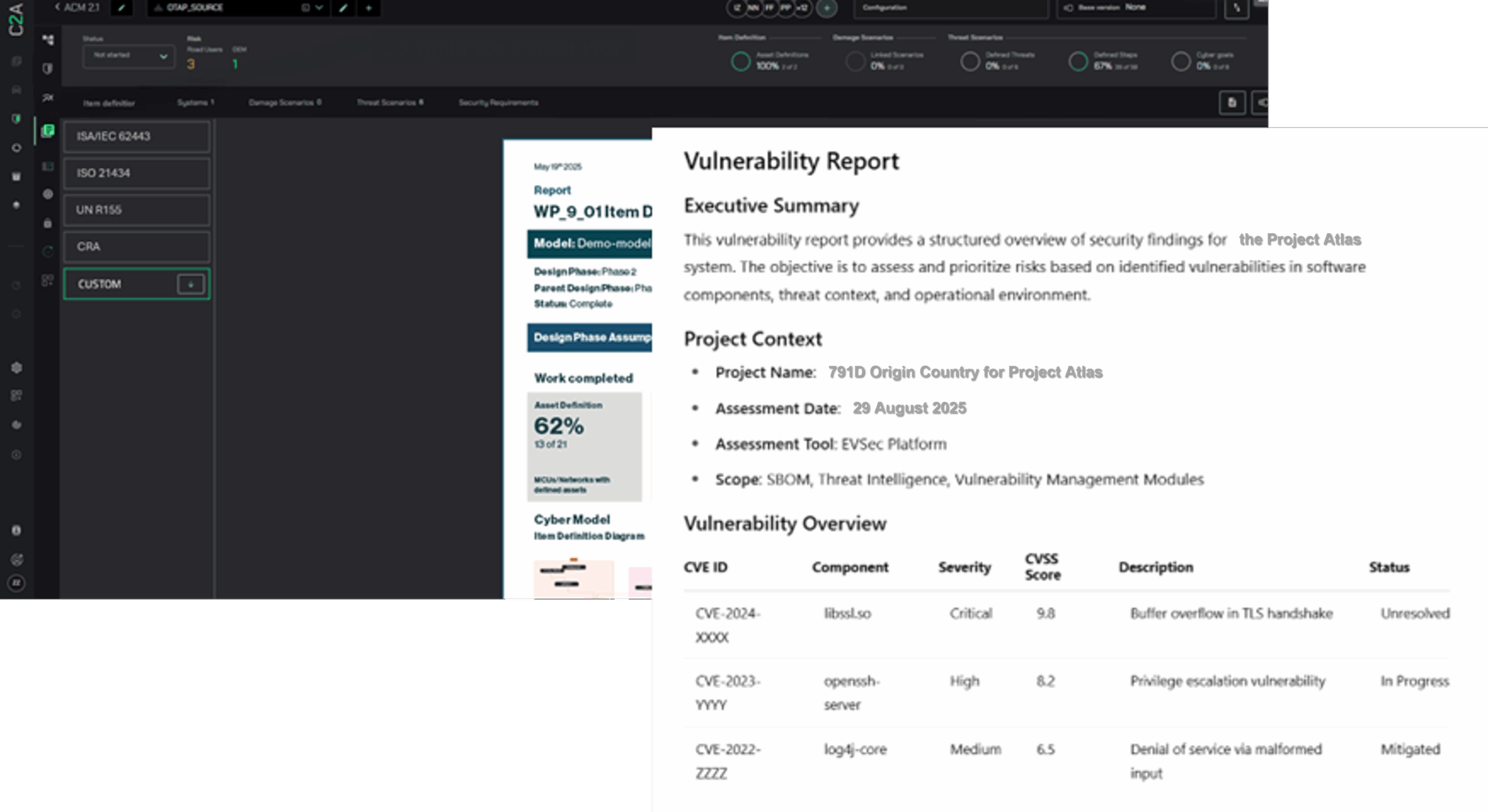
As electric vehicles (EVs) continue to gain traction, expanding EV charging infrastructure has become a top priority. However, this expanding network also ushers in a new and evolving cyber risk landscape, introducing new challenges and requirements for OEMs, manufacturers, government, and regulatory bodies. This rapid evolution, however, also underscores the fact that as a relatively new piece of the cybersecurity puzzle, more effective approaches are urgently needed. It’s crucial to understand that this new ecosystem, extending beyond each charging point, amplifies the risk of attacks, with the consequences of these attacks spreading into more extensive networks, transforming what was once local or minimal into potentially devastating damage.
While many countries have realized the importance of further regulations and introduced cybersecurity standards and policies for EVSE (electric vehicle supply equipment), they essentially have been instigated with the connectivity of charging points related to IoT as top of mind. New EV technology requires its subset of policies, as charging systems are de facto connected devices – connected not only to the cloud and interconnected with other service functions but also connected to critical infrastructure, including but not limited to power grids and third-party service providers. Each instance of “hooking up” an EV for service opens up the cars and all the connections emanating from the stations to further attack vectors and exploitation. OEMs must consider cybersecurity from a holistic perspective and an industry-level risk-based perspective. This holistic approach, which fosters a sense of shared responsibility in the industry, is even more crucial when considering the complexity of today’s connected car.
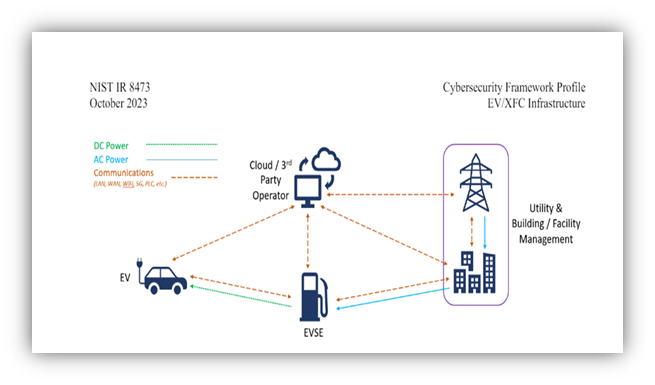
The National Institute of Standards and Technology (NIST) has released updated recommendations for mitigation actions to address these emerging threats, NIST IR 8473 (pdf). These guidelines, developed with a comprehensive understanding of the evolving cyber risks in the EV charging infrastructure, are a testament to the industry’s commitment to cybersecurity. They provide a roadmap for OEMs, manufacturers, and other stakeholders to safeguard their systems, instilling a sense of reassurance in the face of these challenges.
A recent example is Wallbox’s Copper SB charging point, which the UK Office for Product Safety and Standards has indicated cannot be protected against hackers, representing an unsolved weak point they said could allow malicious actors to bring down the UK’s energy infrastructure. Until today, no recall has been issued, and these charging points continue to be sold through the end of June, leaving apparent vulnerabilities. This case is only one example instance, and yet it is obvious why companies should be on higher alert as the regulations for this domain continue to try to catch up. Not only does each connected and electric vehicle and all the components within require increased awareness, but we also clearly see how there is a rational argument to be made for new levels of regulation of the new ecosystem created by a growing number of electric vehicles and charging stations, their drivers, those responsible for each of the many interconnected and disjointed components within each new technology and item required to Sustain the growth of EVs and connected cars.

What’s Next
EV charging infrastructure includes charging stations, communication networks, and backend systems that manage billing and user data. These interconnected systems are vulnerable to several cyber threats: Unauthorized Access can disrupt services and steal information; Data Breaches can intercept transmitted data; Malware and Ransomware can cause operational disruptions; Denial of Service (DoS) Attacks can overwhelm infrastructure; and Physical Tampering can introduce vulnerabilities. However, the most alarming aspect is that attacks on the grid through EV infrastructure integration pose significant risks to grid stability and security, escalating the attack to potential blackouts and controlling entire fleets or areas, underscoring the situation’s urgency.
NIST’s cyber-risk mitigation recommendations emphasize integrating security throughout the entire software development lifecycle (SDLC). Here are key mitigation actions:
- Automated Security Testing: Integrate automated security testing tools into the CI/CD pipeline to identify vulnerabilities early in the development process.
- Continuous Monitoring and Logging: track and analyze security events, ensuring timely detection and response to potential threats.
- Threat Modeling: Conduct threat modeling to identify potential security threats and design appropriate mitigations.
- Incident Response Planning: tailored to the SecDevOps environment, response, and recovery actions.
The expansion of EV charging infrastructure brings about new cyber risks that require comprehensive mitigation strategies. NIST’s updated recommendations provide a robust framework for enhancing the security of these systems. By adopting these guidelines, stakeholders can ensure the resilience and reliability of EV charging infrastructure, protecting it from evolving cyber threats. As the EV market continues to grow, maintaining a proactive approach to cybersecurity will be essential in safeguarding the future of sustainable transportation.
In a recent blog, we discussed how C2A Security’s EVSec risk management and automation platform is gaining traction due to increased awareness of the need to shore up protection. Only a trustworthy risk-driven product security platform allows developers to focus on creative features and manage software and operations at scale.
Are you looking to understand the implications better? Read more about the risk-driven DevSecOps platform. Want to understand more about how C2A Security helps you not just check the boxes but do so in a way that boosts your bottom line? Schedule a free demo today.