by Gilad Bandel, VP of Cybersecurity
The modern vehicle is a marvel of engineering, increasingly connected and intelligent. However, this digital evolution brings a new frontier of risks: cyber threats. A stark reminder of this came with reports of significant vulnerabilities discovered in the Nissan Leaf, where security researchers demonstrated the potential for remote attackers to gain control over critical vehicle functions, including steering. Such a vulnerability could impact the economy, for example, by turning off the fleet or, even worse, the safety of the passengers and other road users, by causing severe accidents. This incident underscores the urgent need for a context-based risk management approach in the automotive industry.
The Nissan Leaf Breach: A Look Under the Hood
Security researchers detailed a sophisticated multi-stage attack chain targeting a 2020 Nissan Leaf. The attack began by exploiting the vehicle’s Bluetooth connectivity vulnerabilities, allowing initial unauthorized access. From there, the attackers bypassed secure boot protections, escalated privileges within the car’s systems, and established a covert and persistent command and control (C2) channel, reportedly over DNS or cellular communication.
This deep level of access enabled them to infiltrate the Controller Area Network (CAN bus), the vehicle’s internal communications backbone. Once on the CAN bus, the researchers could send malicious commands to manipulate various physical components. Disturbingly, this included the ability to control the car’s mirrors, wipers, and door locks, and most critically, to influence its steering, even while potentially in motion. Beyond direct control, the exploit also allowed spying capabilities, such as tracking the vehicle’s location, capturing screenshots from the infotainment system, and recording in-cabin audio. This research led to assigning eight CVE (Common Vulnerabilities and Exposures) identifiers (CVE-2025-32056 through CVE-2025-32063), highlighting the severity and multiplicity of the discovered flaws. Nissan was responsibly informed of these vulnerabilities before public disclosure, while not disclosing specific countermeasures or details for security reasons, assured the public that it had taken the proper measures to address and mitigate this issue.
Mitigation Through Proactive Analysis and Dynamic Defense
Could such an incident have been prevented? The answer lies in a proactive and layered cybersecurity approach. The attack’s nature—involving lateral movement from one compromised system (Bluetooth) to more critical ones (CAN bus)—points to the importance of comprehensive threat modeling and risk assessment from the earliest stages of vehicle design.
This is where tools and methodologies that enable deep analysis, like those visualized in modern cybersecurity management platforms (like the provided image depicting interconnected vehicle components and interfaces), become invaluable. For instance, a platform like C2A Security’s EVSec allows lateral movement analysis. Manufacturers can identify critical control points and vulnerabilities by mapping out all potential pathways an attacker could take through the vehicle’s network.
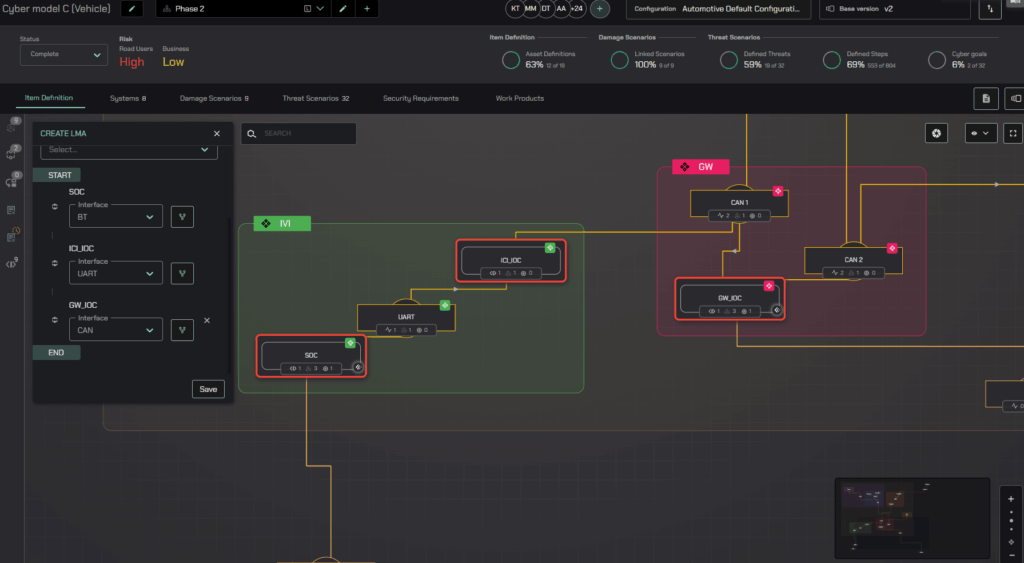
Furthermore, using an attack tree catalog is a crucial mitigation strategy. Attack trees systematically break down potential attack goals (e.g., “gain steering control”) into smaller, sequential steps an attacker would need to achieve. By analyzing these trees, security teams can pinpoint specific weaknesses and implement targeted controls at each step to disrupt the attack chain. The visual representation of system architecture, as shown in the example image with components like ‘SDC’, ‘ICI_IOC’, ‘UART’, and ‘GW_IOC’ interconnected via interfaces such as ‘BT’ and ‘CAN’, directly supports this kind of granular analysis. It helps in understanding how a compromise in one area (e.g., an ‘Interface’ like ‘BT’ on an ‘SDC’) could potentially cascade and allow an attacker to reach and control critical functions managed by, for example, the ‘GW_IOC’ (Gateway ECU) connected to the CAN buses.
Crucially, it’s essential to understand that risk is dynamic. New vulnerabilities are discovered continuously as the threat landscape evolves. Therefore, risk assessment cannot be a one-time activity. The risk scores associated with various attack steps in an attack tree must be continuously recalculated based on new vulnerability disclosures and emerging threat intelligence. As a result, properly updated and relevant risk mitigation actions must be taken with the associated security requirements generated and controls implemented as needed. Ideally, the system would automatically identify and analyze the emerging situation, generating the best optimized, most effective, and efficient recommendations handed to development for implementation. This continuous and dynamic risk management ensures that defenses remain relevant and practical over the vehicle’s entire lifecycle.

Broader Industry Best Practices and the Role of Specialized Vendors
Beyond these specific analytical techniques, a suite of industry’s best practices is essential for comprehensive automotive cybersecurity:
- Security by Design: Integrating security considerations into every phase of vehicle development, from concept to production.
- Defense in Depth: Implementing multiple layers of security controls, so if one fails, others can still protect critical systems. This includes network segmentation, strong access controls, and intrusion detection/prevention systems (IDS/ IPS).
- Secure Over-the-Air (OTA) Updates: Establishing secure mechanisms for updating vehicle software to patch vulnerabilities and deploy new security features (as mandated by regulations like UN R156).
- Vulnerability Management: Continuously scanning for, identifying, and remediating vehicle software and hardware vulnerabilities.
- Penetration Testing: Conduct rigorous security testing by ethical hackers to uncover potential weaknesses.
- Adherence to Standards: Complying with automotive cybersecurity standards and regulations like ISO/SAE 21434 and UN R155.
Leveraging C2A Security to Strengthen Supply Chain Defense
As supply chain attacks continue to rise, auto manufacturers and dealerships must take a proactive security approach, regularly audit hardware and firmware suppliers, perform integrity checks throughout the SDLC, assess third-party risks, and manage BOMs.
C2A Security helps car makers prevent supply chain attacks through several key aspects:
- Contextual Threat Intelligence: Ingest and correlate data from trusted threat intelligence sources, such as Auto-ISAC and other sources, with EVSec’s Cyber Model. EVSec enables car makers to narrow in on the most critical threats, balancing security with product functionality and real-world supply chain attack scenarios. This ensures that security teams can focus on the most impactful threats, enabling faster, more informed decision-making.
- Dynamic Risk and Vulnerability Management: Automatically and continuously identify, prioritize, and mitigate security vulnerabilities for every software product, based on dynamic risk management throughout the product lifecycle.
- Incident Response and Reporting: The built-in Cybersecurity Management System (CSMS) supports car makers in responding swiftly and effectively to incidents, with automated compliance reports covering UN R155, CRA, and other regulations for post-incident analysis and remediation.
- Proactive Security by Design: Streamline production with a built-in security-by-design approach that embeds security into every stage of software development, reducing vulnerabilities and ensuring compliance.
- Automated BOM Validation: EVSec leverages BOM and vulnerability management capabilities to monitor and secure third-party software components, reducing supply chain risks and ensuring compliance.
- Seamless CI/CD Integration: EVSec integrates with CI/CD pipelines, ensuring continuous validation of security controls and proactive mitigation of vulnerabilities before release.
The Nissan Leaf incident serves as a critical case study. As vehicles become more connected, the potential attack surface expands. However, by embracing advanced analysis techniques like lateral movement analysis and attack tree modeling, committing to dynamic risk management, and partnering with proven product security vendors, the automotive industry can build safer, more secure vehicles, ensuring that the benefits of connectivity do not come at the cost of safety, privacy or security.
Schedule a demo to learn how C2A Security can strengthen your automotive supply chain posture.



