The EU Cyber Resilience Act (CRA) officially became law on October 10, 2024, and was enacted on December 10, 2024. It sets a new cybersecurity benchmark for hardware products, connected medical devices, and critical software.
Regulatory Spotlight:
Download your complimentary CRA 1-pager (PDF)
Cyber Resilience Act and Trailer Bodybuilders (blog post)
Navigating UN Regulation No. 155 (blog post)
Designed to enhance resilience across the supply chain, the CRA complements the NIS2 directive, which also came into effect in 2024, creating a more unified cybersecurity framework across industries.
For medical device manufacturers (MDMs), the CRA reinforces compliance with Regulation (EU) 2017/745, introducing stricter security requirements based on risk classification, device type, and company size. MDMs must integrate cybersecurity risk management throughout the product lifecycle, from premarket development to postmarket surveillance. Additionally, the regulation imposes stricter oversight on patient data collection during clinical investigations, ensuring device security and data privacy.
At C2A Security, we recently analyzed the CRA’s impact on the automotive industry and Trailer Bodybuilders, helping OEMs and suppliers navigate compliance challenges. Now, we’re focusing on healthcare cybersecurity, where the stakes are just as high – if not higher.
This article explains what medical device manufacturers need to know about securing products throughout their lifecycles under the CRA’s evolving regulations.
Let’s dive in.
The Latest CRA Updates: What Has Changed?
MDMs must establish a structured vulnerability management process in the premarket phase and bear the CE marking to ensure that products sold in the EU meet high safety, health, and environmental protection requirements. This includes interconnected medical devices.
A study found that 27% of infusion pumps contain critical-severity unpatched CVEs, and 30% have unpatched CVEs. Manufacturers must prioritize vulnerabilities based on risk and severity levels before shipping any products to market. The requirements mandate that the manufacturer accept full responsibility for protecting consumer safety and healthcare infrastructure from potential threats.
Healthcare Industry Impact: A Deep Dive
CRA requirements will reshape how medical devices and products are developed, tested, and maintained throughout their lifecycle. Cybersecurity integration is paramount during the design and construction of each device and product to ensure it meets the highest EU safety standards to qualify for a CE marking.

Outlined is the six-step process manufacturers must follow to obtain a CE marking.
1. Identify the Applicable Directive(s) / Regulation(s) and Harmonized Standards
Example: MDMs must ensure product compliance with the Medical Device Regulation EU 2017/745 and the Cyber Resilience Act. Harmonized standards include ISO 13485:2016, ISO/IEC 27001, and IEC 81001-5-1:2021. Many other regulations and standards are based on the device and product type, such as IEC 62304 for software lifecycle processes and IEC 60601-1 for electrical safety.
2. Verify Product-Specific Requirements
Example: Devices must have a fail-safe mechanism in case of a malfunction. This could be a heart monitor that switches to a default monitoring mode with limited functionality or an insulin pump that must revert to a pre-programmed insulin dosage if it loses wireless connectivity. Patients must receive critical care and treatment without disruption, even if the device experiences a technical failure, software glitch, or connectivity loss.
3. Identify Whether an Independent Conformity Assessment (By a Notified Body) Is Necessary
Example: Critical care medical devices, such as ventilators, pacemakers, and dialysis machines, require a Notified Body Assessment to ensure compliance with regulatory safety standards for life-threatening scenarios. Failure to uphold these standards can result in severe penalties, class action lawsuits, and regulatory backlash against manufacturers.
4. Test the Product and Check Its Conformity
Example: Devices must be tested for quality management, and the product design must meet specific compliance requirements. For instance, a wireless pacemaker must be tested to verify that the device automatically switches to a backup system without disrupting heart rhythm support if the primary battery or signal processing unit fails.
5. Draw Up and Keep Available the Required Technical Documentation
Example: Manufacturers must conduct BOM assessments to identify potential security risks in third-party components and document all updates before postmarket deployment. These critical risks include outdated software libraries or end-of-life (EOL) hardware components. BOMs help security teams document every component and detail its origin, version, and any known vulnerabilities.
6. Affix the CE Marking and Draw Up the EU Declaration of ConformityExample: Manufacturers must ensure compliance with specific regulatory bodies to launch the product postmarket. To obtain the coveted CE marking, a final assessment should verify that all device parts, components, and software modules meet consumer safety and cybersecurity requirements.
How MDMs Should Prepare for CRA Compliance
Improve device lifecycle security management: Follow security-by-design principles and plan for safe decommissioning of devices to prevent residual data exposure. Conduct detailed threat modeling using the STRIDE or MITRE ATT&CK frameworks.
Conduct BOM assessments: A Bill of Materials (BOM) provides a comprehensive inventory of every device’s hardware and software component. BOM assessments enable security teams to track, document, and update components across the supply chain and product lifecycle to ensure compliance with the CRA and other mandated industry-specific regulations, such as HIPAA and GDPR.
Implement a Vulnerability Disclosure Program (VDP): Transparency is key to preparation for the CRA. Assemble a dedicated security team to ensure all potential device vulnerabilities are reported, tracked, and resolved efficiently. Establish clear KPIs, such as the number of vulnerabilities fixed per quarter, to benchmark progress and communicate these metrics to stakeholders.
Encryption: Encrypting communication between devices and wireless connections minimizes the risk of patient data being intercepted by unauthorized entities or potential threat actors within proximity. Unencrypted devices may be subject to recall, regulatory penalties, or restricted market access due to non-compliance with the CRA. Ensure that data transmitted between devices, cloud systems, and healthcare networks is fully encrypted at all stages of the product development lifecycle.
Automate device security settings: Devices are complex by nature. Consumers should not have to decipher configuration settings or read technical instruction support guides to program their devices. Manufacturers must consider this aspect before any device can ship to market. Advanced security settings should be baked into every device or product, including a fail-safe mechanism if the device suddenly malfunctions or the firmware becomes corrupted during an attack. Manufacturers should update consumers several months in advance if the devices have reached their end-of-life (EOL) to give users sufficient time to transition to newer, supported models.
The Future of Cybersecurity for MDMs Under the CRA
Moving forward, the CRA aims to reduce friction for end users and suppliers by simplifying product configurations and enhancing cybersecurity measures. For MDMs, this means conducting thorough BOM and risk assessments, maintaining up-to-date documentation, establishing clear guidelines for vulnerability management, and integrating security checks throughout the entire product lifecycle.
Building a Cyber-Resilient Future with C2A Security
As medical device manufacturers (MDMs) prepare for the EU Cyber Resilience Act (CRA) compliance deadlines, a proactive, automated approach to cybersecurity is critical. The CRA mandates lifecycle security, requiring manufacturers to embed cybersecurity from development through postmarket surveillance.
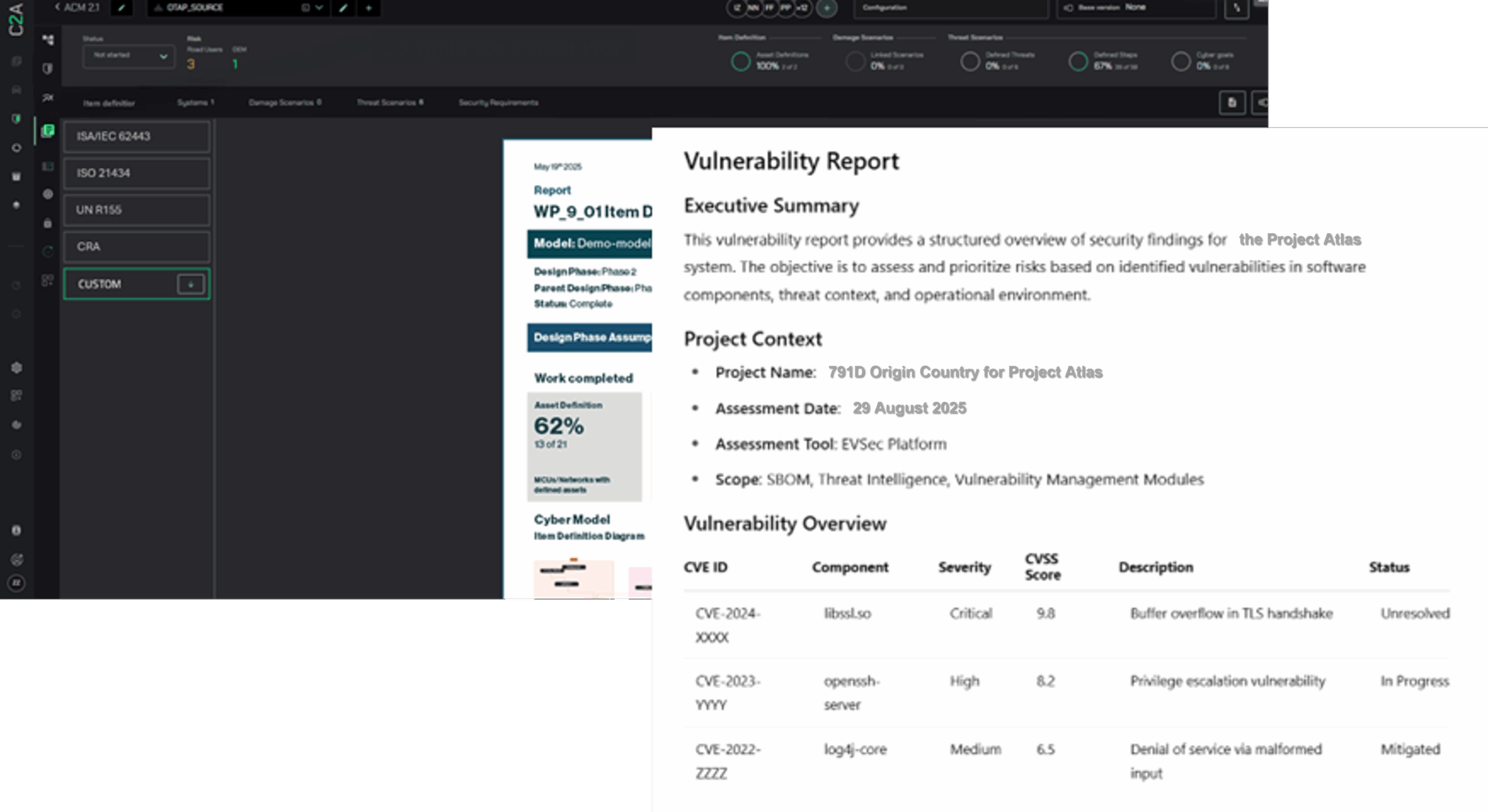
C2A Security’s EVSec Platform helps MDMs streamline compliance and enhance cybersecurity resilience across the entire product lifecycle:
- End-to-end Cybersecurity Management: EVSec ensures security is integrated through postmarket monitoring from the earliest design stages, aligning with the CRA’s lifecycle security requirements.
- Context-Driven Risk Prioritization: EVSec helps manufacturers focus on the most critical threats, balancing security with product functionality and clinical needs by analyzing real-world attack scenarios.
- Automated BOM & Vulnerability Management: The CRA mandates secure supply chain management, requiring real-time tracking of third-party software risks. EVSec automates SBOM validation, vulnerability assessments, and remediation, ensuring compliance with regulatory frameworks like MDR, HIPAA, FDA requirements, and NIST guidelines.
- Patch Management & Compliance Automation: CRA compliance demands continuous security updates. EVSec automates vulnerability scanning, patch deployment, and compliance audits, reducing manual effort while protecting devices.
- Collaboration & Workflow Orchestration: Secure development requires cross-functional coordination. EVSec automates security task delegation, enabling regulatory, engineering, and security teams to collaborate efficiently—without disrupting clinical workflows.
With EVSec, MDMs can reduce compliance burdens, accelerate time to market, and maintain patient safety while future-proofing their cybersecurity strategy against evolving regulatory requirements.
Schedule a demo today to learn more and stay ahead of the CRA.