In July 2025, a highly prolific breach made waves in the cybersecurity world when the U.S. National Nuclear Security Administration (NNSA) confirmed that it had been compromised through a zero-day vulnerability in Microsoft SharePoint’s on-premises servers.
The breach has been attributed to state-sponsored Chinese threat actors, including Linen Typhoon, Violet Typhoon, and Storm-2603, who exploited the flaw to steal cryptographic MachineKeys and enable long-term persistence inside federal networks. Although no classified data was accessed, the incident impacted hundreds of organizations worldwide, including two U.S. federal agencies.
Rather than a one-off exploit, this event reflects a broader trend: attackers are weaponizing collaboration platforms as an entry point into critical systems and supply chains.
How the SharePoint Attack Happened: Origin of the Breach
The threat actor groups successfully bypassed authentication in a calculated ToolShell attack (CVE-2025-53770), enabling them to execute remote code on SharePoint servers. The attack chain illustration below shows Storm-2603 altering Group Policy Objects (GPO) to encrypt files, extract plaintext credentials and MachineKey data, and distribute the Warlock ransomware across compromised Microsoft environments.
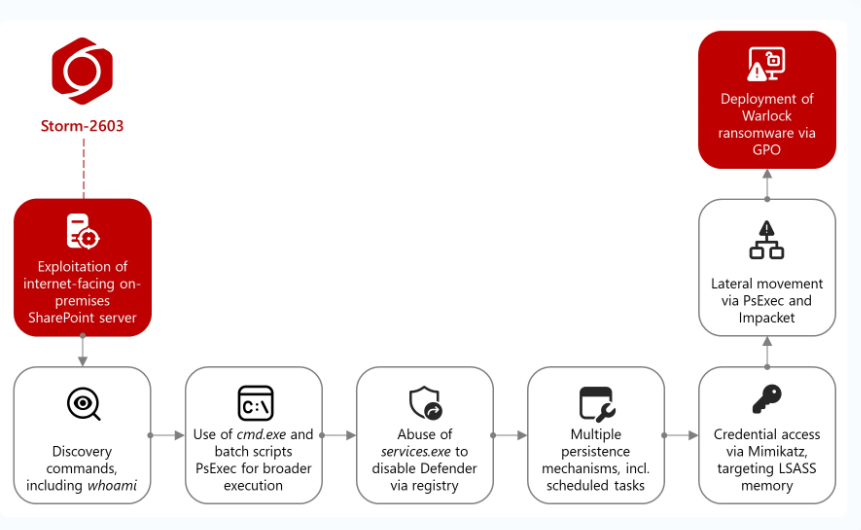
Storm-2603 sent a POST request to the SharePoint server, using a malicious script named spinstall0.aspx to execute PowerShell commands and retrieve the MachineKey data.
Over 200,000 organizations rely on SharePoint to manage and store sensitive documents. Earlier this month, Microsoft neglected to patch a bug in its on-premises SharePoint service and has since only provided partial mitigations for several other vulnerabilities. The incident highlighted the risk of exploited SharePoint vulnerabilities and a dependence on vendor patch cycles.
This incident underscores the high cost of depending solely on vendor patch cycles: one unpatched bug became a systemic exposure point for hundreds of critical networks.
SharePoint Paves the Way for Larger Attacks Against Critical Infrastructure
State-sponsored Chinese groups exploited SharePoint’s weaknesses for access and long-term espionage and operational disruption. Using spoofing flaws in on-premises servers, attackers gained a foothold in environments once considered peripheral, then escalated privileges through persistent web shells, using espionage as a core tactic, technique, and procedure (TTP) for prolonged intelligence gathering similar to those employed by Volt Typhoon in 2024.
- Linen Typhoon (APT 27) has stolen intellectual property from governments and enterprises since 2012.
- Violet Typhoon (APT 31) specializes in espionage against governments, NGOs, defense entities, and academic institutions since 2015.
By exploiting platforms organizations wrongly categorize as “low-risk,” these actors reached sensitive systems, including the U.S. National Nuclear Security Administration. While SharePoint Online in Microsoft 365 was not impacted, on-premises systems remain exposed, and attackers can retain access through stolen MachineKeys even after patches are applied.
Escalating Risks Beyond SharePoint
The lesson is clear: collaboration platforms are becoming stepping stones for advanced persistent threats (APTs) targeting critical infrastructure. Organizations cannot assume that a patched system equals a secure system.
Microsoft advises rotating ASP.NET MachineKeys and revoking compromised credentials, but the scope extends far beyond SharePoint. Other tools like OneDrive carry similar risks. A recent vulnerability in its file-sharing function allowed unauthorized access to entire cloud backups, creating opportunities for lateral movement and ransomware deployment. For critical infrastructure, the stakes are existential: attacks on connected accounts can shut down power grids, disrupt transportation, or cripple water treatment facilities.
As of this writing, nearly 9,700 on-premises SharePoint devices remain internet-exposed, many unpatched and unverified. Even those updated remain at risk if adversaries already established long-term persistence.
How C2A Security Secures OEMs and Vendors in Critical Infrastructure and Supply Chains
The SharePoint breach is a clear reminder that relying on vendor patch cycles is insufficient. Critical infrastructure operators, OEMs, and tier-1 suppliers must take a proactive approach to security that addresses blind spots before attackers exploit them.
EVSec, C2A Security’s cybersecurity automation platform, embeds trust, visibility, and automation across the entire product and supply chain ecosystem. It enables organizations to:
- Deliver SBOM-based risk intelligence for early detection of vulnerable components.
- Perform vendor risk profiling to assess and monitor supplier exposure.
- Apply real-time vulnerability detection and patch intelligence that goes beyond vendor advisories.
- Orchestrate incident response workflows for fast, coordinated action.
- Maintain continuous compliance with ISO/IEC 27001, NIST CSF, IEC/ISA 62443, NIS2, and other critical standards.
With EVSec, organizations can enforce supply chain accountability across the full software development lifecycle, ensuring that a single missed update does not escalate into a system-wide compromise.
Schedule a demo to learn how C2A Security can help protect critical infrastructure from APTs and supply chain attacks.







