The European Commission recently updated the Radio Equipment Directive (RED) 2014/53/EU, introducing new cybersecurity requirements that will go into effect on August 1, 2025. These new provisions impose stricter rules on manufacturers of connected wireless devices, who must demonstrate cybersecurity and compliance before any 5G radio equipment can be sold on the EU market.
The European Commission enacted RED in January 2022 to strengthen cybersecurity requirements for device manufacturers that incorporate radio technologies into their products. The directive aims to protect networks from harm, safeguard personal data and user privacy, and provide a stronger defense against emerging cyber threats in organizational settings and home environments for IoT and wireless devices.
This article will highlight the immediate security actions manufacturers of wireless devices can implement to prepare for the new regulation.
What is the Radio Equipment Directive (RED) and Why Does It Matter?
As of April 2025, 5G connectivity has surpassed 2.25 billion connections worldwide, growing four times faster than 4G during its comparable adoption phase. This also presents new challenges for securing wireless and IoT devices connected to public 5G networks at a velocity that continues to outpace the deployment of adequate security measures for manufacturers.
The core objectives of the Radio Equipment Directive (RED) align with the requirements of the Cyber Resilience Act, as both are crucial for manufacturers seeking CE marking to sell products within the highly regulated and complex EU market. Under RED, product security is a top priority, particularly given the growing complexity and risk profile of wireless and IoT-enabled devices regarding persistent threats and attacks.
Cyber attacks on 5G networks are projected to increase 300% in the next five years, highlighting the significance of the newly imposed regulations.
Toy safety is another RED focal point. Critical vulnerabilities can also be found in baby monitoring cameras, which allow attackers to intercept personal data, scan the home layout, and record private conversations.
A Spanish study found that only 57% of IoT-connected toys meet the cybersecurity standards set by the National Institute of Cybersecurity. The study analyzed 26 of the top-selling connected toys in the market. Other wearable radio equipment under the new directive includes fitness tracking devices, smartwatches, and smart glasses, where product security and data protection are paramount for manufacturers.
Key Requirements of the New RED Cybersecurity Regulation
Article 3(3)(d), (e), and (f) of RED outlines cybersecurity provisions that manufacturers of wireless devices must consider before shipping products to consumers. The article emphasizes security for connected IoT devices, where cyber risks are prevalent.
A study found that 99% of healthcare organizations manage IoMT devices with known exploited vulnerabilities. These include patient and surgical devices, where sensitive patient data is openly transmitted over unencrypted network connections. Article 3(3)(d), (e), and (f) of RED focuses on improving network security, specifically 5G networks, against these types of threats.

Manufacturers are required to disclose device security measures and information in the following areas.
- Device Authentication and Authorization: Strong security measures, such as authentication mechanisms and protocols, must be implemented to verify user identities and prevent unauthorized network access.
- Firmware and Software Updates: It is the manufacturer’s responsibility and obligation to send software and firmware updates in a timely manner. Undisclosed vulnerabilities can quietly slip past the design phase of the SDLC and impact consumers long past deployment. Manufacturers must demonstrate this commitment to consumers and provide precise fail-safe mechanisms for administrators to apply updates without disrupting device functionality.
- Incident Reporting: Manufacturers must have a vulnerability disclosure program and notify authorities during security incidents. Any device or equipment failures must be promptly reported, especially if they pose a risk to user safety, data integrity, or network security. Medical devices and embedded vehicle firmware are good examples of connected devices that can endanger the well-being of consumers.
Industry-Specific Use Cases for RED
Industrial & IoT
IoT threats against manufacturers have surged in recent years. A recent report revealed that 54.5% of all cyberattacks targeted the manufacturing sector, with nearly 6,000 weekly attacks detected across monitored devices. Unsecured IoT devices can inadvertently introduce malware into interconnected systems, ultimately compromising critical operational technology (OT) infrastructure such as energy grids, water supplies, industrial control systems (ICS), and programmable logic controllers (PLCs). An attack of this magnitude could essentially cut off the power or water supply to an entire city, causing billions in damages and widespread service disruptions.
Healthcare and Medical Devices
Critical vulnerabilities in wireless communication modules such as Bluetooth and 5G connected over a public hospital Wi-Fi network can be exploited to intercept sensitive patient data or gain unauthorized access to connected medical devices. This presents a cascading effect across the entire healthcare ecosystem, potentially disrupting clinical workflows and impacting patient safety, above all else.
A study found 82% of healthcare organizations run their medical devices on outdated Windows systems. Medical device manufacturers (MDMs) are responsible for ensuring that devices are built with security by design, encrypted communication, and the ability to push out timely firmware updates or end-of-life (EOL) notifications.
Smart Home Devices
Smart home devices connected to routers and open Wi-Fi hotspots are open access ports for attackers to exploit. An attacker might enter through a smart thermostat vulnerability and leverage it as a gateway to gain complete network control. From there, they could move laterally and compromise other connected IoT devices, such as CCTV cameras, smart sensors, locks, and even entire security systems. Home network devices face an average of 10 attacks every 24 hours, emphasizing the importance of the newly regulated RED cybersecurity requirements.
Preparing Manufacturers for RED Before the August Deadline
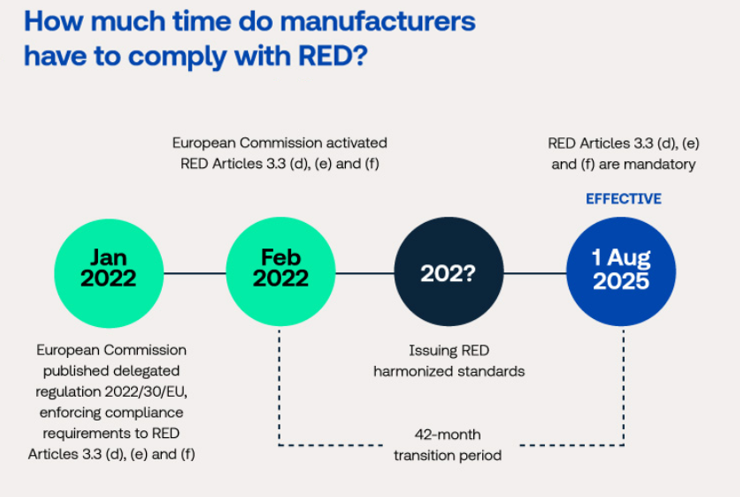
Timing is essential as manufacturers have until August 1, 2025, to meet the new cybersecurity requirements imposed by the EU directive.
Planning ahead is crucial for ensuring that all connected devices comply with the updated Radio Equipment Directive (RED) and avoid any production setbacks, in addition to regulatory penalties.
Manufacturers must get a head start to avoid last-minute issues and delays, especially given the technical challenges in redesigning products to comply with the new regulation. An unsecured component in an IoMT device, such as an unencrypted wireless communication module in a wearable heart monitor, could leak sensitive patient data to malicious actors.
Manufacturers will have to bake in security by design principles and test their products rigorously throughout the development lifecycle. Conducting an SBOM is a highly effective security measure that provides regulators with an itemized inventory of all software components, libraries, and dependencies used in a device.
Product security teams must deploy these security measures now to ensure ample time for risk mitigation and compliance validation before the deadline approaches.
C2A Security: Empowering Manufacturers to Lead the Way in Complying with RED Cybersecurity Standards
C2A Security empowers manufacturers of wireless devices not just to meet but exceed the newly enforced cybersecurity requirements under the Radio Equipment Directive (RED). Here’s how:
Proactive Risk & Vulnerability Management: C2A Security automates the continuous identification, prioritization, and mitigation of vulnerabilities throughout the product lifecycle. This proactive approach ensures vulnerabilities are addressed early, minimizing risk and ensuring real-time protection. Tailored to each product, this solution reduces manual intervention, enhancing security while enabling manufacturers to focus on innovation.
Cybersecurity by Design: C2A’s cybersecurity-by-design approach integrates security into every stage of product development. By embedding security from the start, manufacturers meet and exceed regulatory requirements, like RED, while eliminating vulnerabilities early. This proactive model reduces the need for costly post-launch patches and ensures a robust security framework throughout the product lifecycle.
Contextual Threat Intelligence: EVSec aggregates data from trusted sources like Health-ISAC and Auto-ISAC to identify critical threats tailored to each product ecosystem. By correlating real-time product data with threat intelligence, manufacturers can balance security and functionality effectively, proactively addressing real-world attack scenarios while maintaining operational goals and compliance.
Streamline Incident Response and Reporting: C2A Security provides automated incident response and reporting solutions tailored to diverse industries, enabling organizations to manage and mitigate cybersecurity incidents efficiently. By integrating real-time threat detection, actionable insights, and automated workflows, C2A ensures that all incidents are addressed swiftly, reducing downtime and maintaining business continuity across sectors. Whether in automotive, healthcare, or other critical industries, our solutions are designed to help teams respond proactively and remain compliant with evolving cybersecurity regulations.
Automated BOM Validation: EVSec enhances BOM management and vulnerability orchestration, ensuring the continuous monitoring and securing of third-party software components. This reduces supply chain risks and ensures compliance with cybersecurity regulations.
Automated Compliance Audits and Certifications: With automated compliance audits and risk-driven vulnerability prioritization, C2A Security simplifies the validation and management of the BOM, supporting compliance with industry-specific regulations such as RED and the EU Cyber Resilience Act.
Schedule a demo to learn how C2A Security can help manufacturers prepare for the new cybersecurity requirements ahead of the Radio Equipment Directive (RED).







