The recent endorsement of the Cyber Resilience Act (CRA) by the European Union Parliament marks a significant advancement in cybersecurity legislation. Primarily focused on strengthening Products with Digital Elements (PDEs) within the EU, the CRA sets up a framework to guarantee the cyber resilience of products that have digital components. This article discusses the implications of the CRA for the automotive industry, specifically Trailer Bodybuilders. As the automotive industry evolves with increasing digitalization, various segments must adapt to new cybersecurity standards. One such segment is Trailer Bodybuilders – understanding their role and how the CRA impacts their operations is crucial for comprehending the broader scope of this legislation.
A Primer on Trailer Bodybuilders
A trailer bodybuilder is a company or workshop specializing in designing, constructing, and assembling the bodies or trailers attached to the chassis of commercial vehicles, usually trucks and pickup trucks (US). These bodies or trailers are customized to suit various applications, such as:
- Freight and Logistics: Constructing dry vans, refrigerated trailers, flatbeds, and curtain-sided trailers for transporting goods.
- Construction: Building dump bodies, mixers, and lowboys for hauling construction materials and equipment.
- Specialized Transport: Creating custom trailers for transporting specific items like livestock, automobiles, hazardous materials, or oversized loads.
- Utility and Service: Developing bodies for utility trucks, mobile workshops, tow trucks, and emergency service vehicles.
Trailer bodybuilders often work closely with truck manufacturers to ensure the bodies they create are compatible with the chassis and meet regulatory standards and requirements.

**
A Primer on the Cyber Resilience Act (CRA)
The European Union Parliament has recently approved the Cyber Resilience Act (CRA), a comprehensive cybersecurity legislation to improve the security of PDEs (both Hardware and Software) within the European Union (EU). The regulation aims to address two main problems with PDEs:
- The inadequate level of cybersecurity inherent in many products, or inadequate security updates to such products and software.
- The inability of consumers and businesses to currently determine which products are cyber secure or to set them up in a way that ensures their cybersecurity is protected.
The CRA categorizes products into Class I, Class II, and Unclassified, imposing different levels of cybersecurity requirements based on the associated risk. It mandates security-by-design principles and establishes essential cybersecurity requirements for manufacturers, importers, and distributors of digital products. Once the CRA is entered into effect, PDEs must bear the CE marking to indicate they comply with the new standards
The CRA has four specific objectives:
- Ensure that manufacturers improve the security of products with digital elements from the design and development phase and throughout the entire product lifecycle;
- Ensure a coherent cybersecurity framework, facilitating compliance for hardware and software producers;
- Enhance the transparency of security properties of products with digital elements;
- Enable businesses and consumers to use products with digital elements securely.
The CRA is set to enter into force in the 2nd half of 2024, with the majority of its provisions applying three years after publication. However, vulnerability reporting obligations will apply 21 months after this date.
There are six primary obligations for manufacturers:
- Cybersecurity is taken into account in the planning, design, development, production, delivery and maintenance phases;
- All cybersecurity risks are documented;
- Manufacturers will have to report actively exploited vulnerabilities and incidents;
- Once sold, manufacturers ensure that vulnerabilities are handled effectively for the duration of the support period;
- Clear and understanding instructions for the use of products with digital elements;
- Security updates are made available to users for the time a product is expected to be in use.
**
The CRA and the Automotive Industry
While the CRA exempts automotive products covered under the Vehicle General Safety Regulation (Regulation (EU) 2019/2144), the industry is not entirely isolated from its implications. Automotive manufacturers should consider the impact on digitalized components and services, ensure supply chain compliance, and recognize the CRA’s importance for accessing the EU market.
To prepare for the CRA, car makers and Tier 1 suppliers should:
- Implement efficient documentation processes to track and record vulnerabilities systematically and use this information in subsequent risk assessments:
** Mandatory vulnerability handling process for the expected product lifetime or 5 years (whichever is shorter).
** Document product vulnerabilities by creating an BOM encompassing at least the product’s primary components.
** Collate and maintain relevant product information for ten years after the PDE is placed on the market. - Plan the product lifecycle to ensure continued security support throughout the compliance period:
** Assess and classify their PDEs to determine the level of security requirements and compliance efforts needed. - Establish robust risk management programs:
** Conduct cyber risk assessments before placing a PDE on the market, including additional due diligence for third-party component suppliers. Enhancing the transparency of security properties.
** Delegate specific tasks to an authorized representative while performing internal risk assessment activities within the organization. - Establish organization-wide practices, such as coordinated disclosure and vulnerability management processes:
** Improve the security of PDEs from the design and development phase and throughout the whole life cycle. Conducting regular testing, patch management, responsible disclosure programs, and clear documentation.
Additionally, note that Annex 1 of the CRA covers essential cybersecurity requirements such as endpoint detection, privilege management, data minimization, and vulnerability and patch management.

Three Reasons Why Trailer Bodybuilders Aren’t Covered under UN Regulation No. 155
Trailer bodybuilders are covered under the Cyber Resilience Act (CRA) and not under UN Regulation No. 155 primarily because of the scope and focus of each regulation. With the increasing integration of digital systems in trailer design and functionality – for advanced monitoring, control, and communication technologies, Trailer Bodybuilders need to ensure that their products meet various cybersecurity standards and regulations. UN Regulation No. 155 targets the cybersecurity and cyber-resilience of complete vehicles and motorcycles, and applies to the Type Approval of vehicles, particularly concerning Cybersecurity Management Systems (CSMS). Trailer bodybuilders are covered under the Cyber Resilience Act (CRA) for three reasons:
- Digital Components: Trailers increasingly incorporate advanced digital systems for monitoring, control, and communication, which are covered by the CRA’s focus on cybersecurity for products with digital elements.
- Regulatory Alignment: The CRA’s broad applicability to all products with digital components ensures that even specialized and non-vehicle-specific products, such as trailers, comply with cybersecurity standards.
- Distinct from Complete Vehicles: While UN Regulation No. 155 is specific to complete vehicle systems and their type approval, the CRA’s broader scope means it encompasses the various digital aspects of trailers built by bodybuilders.
**
Fines and Violations of the Cyber Resilience Act (CRA)
The CRA will require manufacturers to ensure their PDEs are free from “known exploitable vulnerabilities” before market release. Vulnerabilities must be addressed and remediated “without delay” through security updates and disclosed publicly once an update is available. Exploited vulnerabilities must be reported even if there is no related cyber incident.
Violations of the CRA will be subject to different fines (PDF):
- Violations of the CRA – Fines reaching a maximum of 15,000,000 EUR or 2.5%*.
- Non-compliance with any other obligations – up to 10,000,000 EUR or, if the offender is an undertaking, up to 2%*.
- The supply of incorrect, incomplete, or misleading information to notified bodies and market surveillance authorities in reply to a request – up to 5,000,000 EUR or, if the offender is an undertaking, up to 1%*.
Fines are from the company’s total worldwide annual turnover for the preceding financial year, whichever is higher.
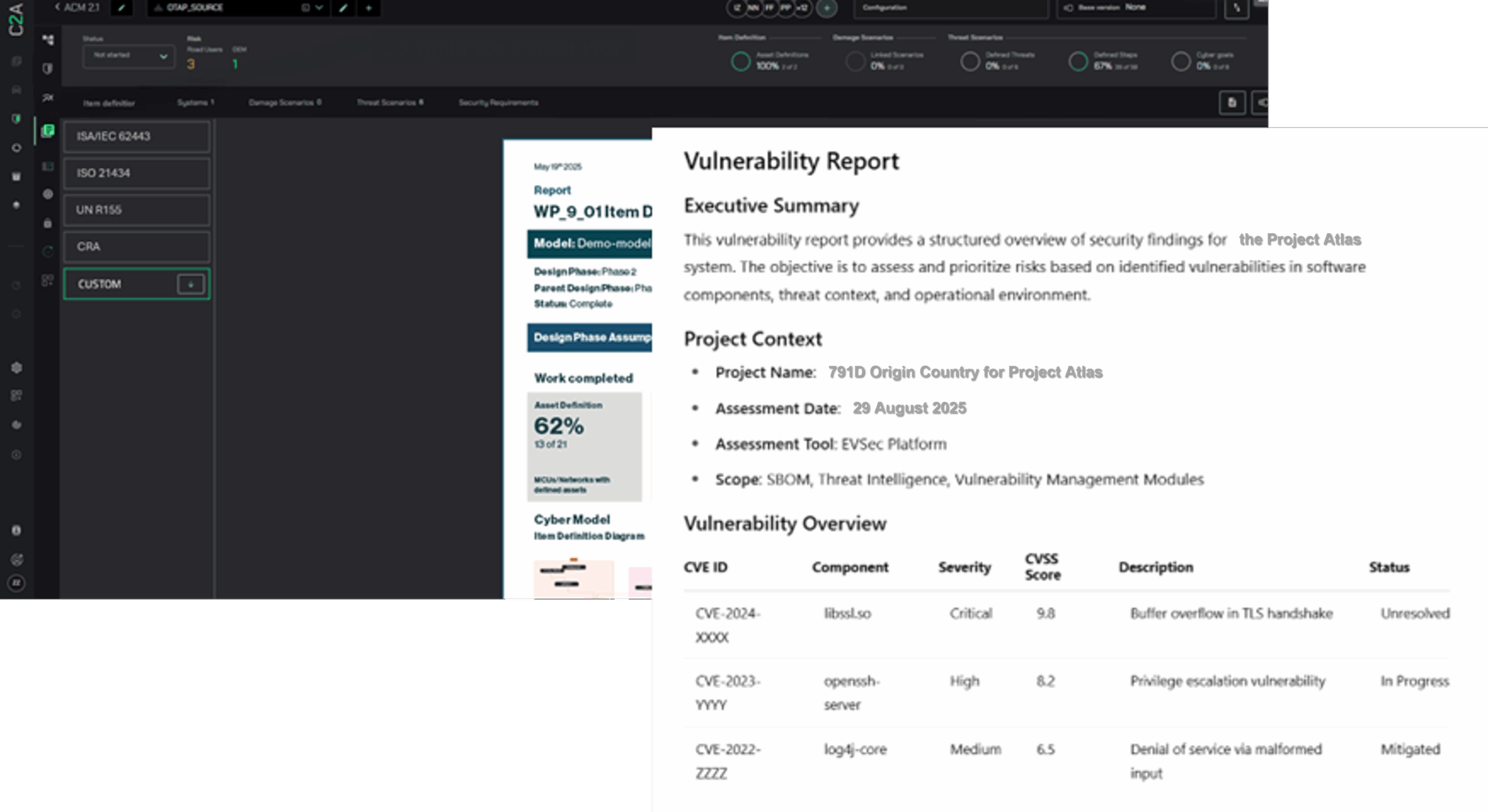
The new CRA underscores the critical importance of robust cybersecurity measures for organizations across Europe. It emphasizes the need for proactive vulnerability management to identify and mitigate potential threats effectively. A comprehensive cybersecurity platform, such as C2A’s EVSec, plays a vital role in ensuring compliance with CRA and other regulatory frameworks.
Simplifying CRA Compliance with EVSec Platform
EVSec is a product security DevSecOps risk management and automation platform designed to help companies tackle the challenges posed by software-defined products, particularly in regulated industries. EVSec platform leverages a proprietary risk-based approach to product security, enabling organizations to achieve compliance in minimum time and cost while enhancing their overall cybersecurity posture:
• Security by Design with Dynamic TARA, ensuring the highest level of Cybersecurity through the entire product lifecycle.
• EVSec’s binary analysis and BOM Management capabilities for automated BOM validation, ensuring coherence and up-to-date information.
• EVSec’s Centralized platform- enabling correct work and authorization processes for coordinated vulnerability disclosure & mitigation.
Transition to a proactive security posture leveraging EVSec’s comprehensive capabilities for cybersecurity management systems, risk assessment, detection and response, software updates, data protection, and continuous compliance.