As medical technology evolves, so must the safety, efficacy, and compliance standards. ISO 14971, the cornerstone of risk management for medical devices, has been updated to meet the challenges of the current and future complex healthcare landscape. The 2019 edition brings new principles, expanded terminology, and critical updates to align with regulatory frameworks like the Medical Device Regulation (MDR).
At its core, ISO 14971:2019 outlines a risk management framework that supports manufacturers in identifying, evaluating, and mitigating risks associated with medical devices, including software as a medical device (SaMD). It integrates industry practices and introduces a dynamic approach to risk management.
Risk management in the medical device industry is grounded in key principles known as ‘Risk Basics.’ These principles guide identifying, assessing, and controlling risks throughout a device’s lifecycle, aligning with regulatory expectations like the FDA’s cybersecurity guidance, which stresses the need for an ongoing and comprehensive risk management process.
ISO 14971:2019 – What’s the Scope?
The scope now explicitly includes software as a medical device (SaMD), not just traditional medical devices and in vitro diagnostic (IVD) devices. Introducing 3 critical terms:
- Benefit: Defined as a medical device’s positive influence or desirable outcome, extending beyond patient health to areas like public health or patient management.
- Reasonably Foreseeable Misuse: Previously a note, it is now a defined term. It refers to the unintended use of a device outside its intended purpose based on predictable user actions.
- State of the Art: A technical stage reflecting generally accepted practices based on current knowledge, not necessarily the most advanced solution.
These terms emphasize a holistic view of risk management, focusing on real-world usage and evolving technologies.

Key Insights
1. Revised Risk Management Process
Not just defining and documenting a process but implementing it in a process:
- Identifying hazardous situations in addition to hazards.
- Ensuring risk management personnel have education, training, skills, and experience beyond mere knowledge.
- Expanding risk control measures to include integrated safety and manufacturing processes.
2. Benefit-Risk Analysis
The benefit-risk analysis has been redefined, placing greater emphasis on benefits. If residual risks outweigh benefits, manufacturers are now explicitly allowed to change the device or its intended use, a practice now codified in the standard.
3. Overall Residual Risk Evaluation
Manufacturers must define methods and acceptance criteria for evaluating overall residual risk in their risk management plans. These criteria can differ from those used for individual risks, allowing for a more tailored approach.
4. Continuous Monitoring and Production Activities
Risk management extends into production and post-production phases, requiring manufacturers to:
- Collect and evaluate information from production, users, service personnel, and public sources.
- Monitor for changes in the state of the art, new hazards, or hazardous situations.
- Implement corrective actions for devices already in the market if necessary.
The Importance of Dynamic Risk Management as part of a Holistic Platform
A dynamic approach to risk management is essential in the fast-paced and ever-evolving landscape of medical device cybersecurity. Unlike static measures, which remain fixed and unresponsive to new threats, dynamic risk management continuously assesses and adapts to the changing threat landscape. This involves contextual vulnerability management, which evaluates risks based on their context, impact, and feasibility, ensuring that the most critical threats are prioritized and addressed.
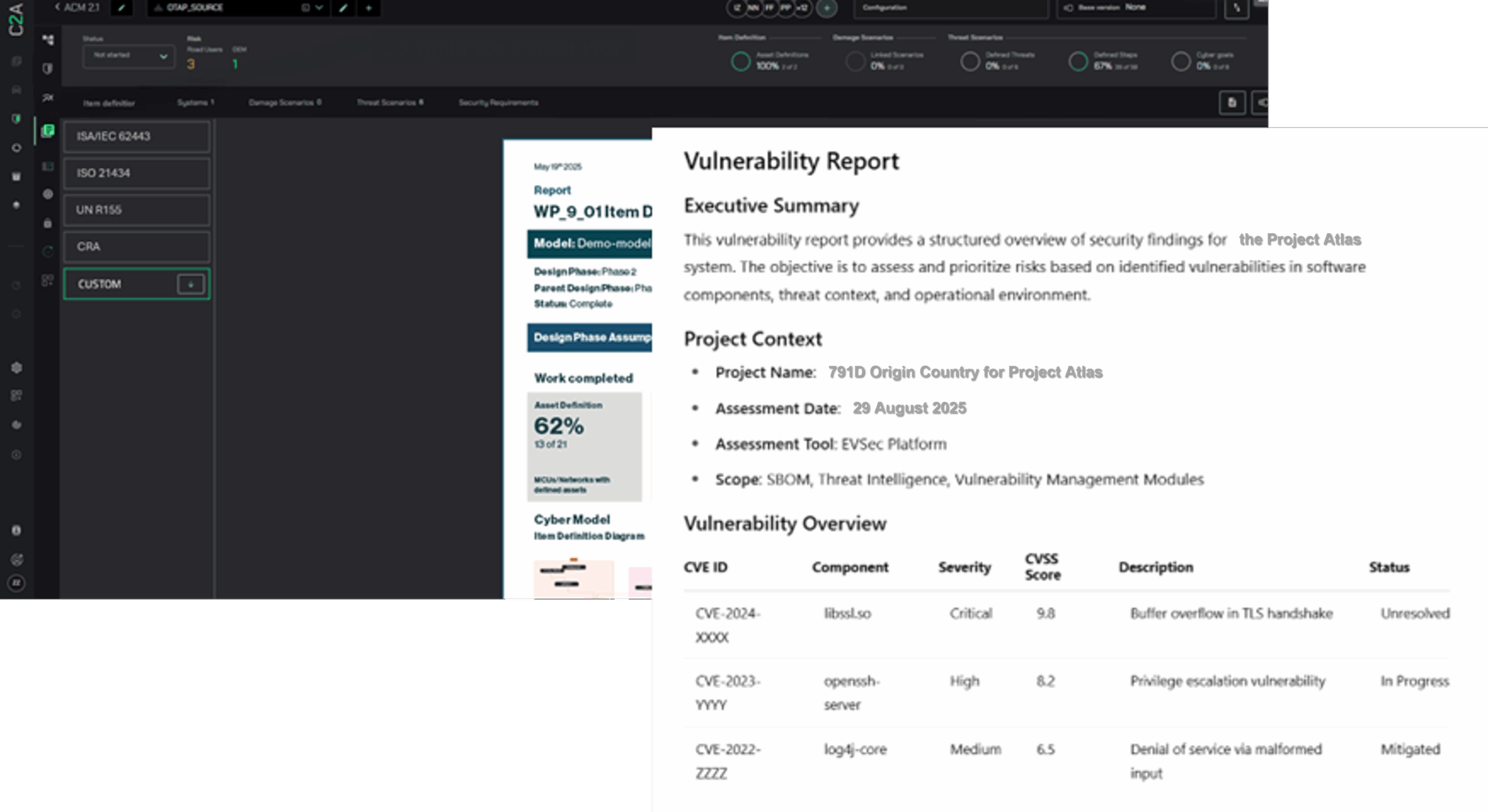
To enhance the overall robustness of medical systems, integrate key elements such as dynamic risk management with comprehensive compliance measures and receive a holistic product security platform. The true strength of a holistic security platform lies in its ability to seamlessly integrate Threat Analysis and Risk Assessment (TARA) with a Software Bill of Materials (SBOM), ensuring a proactive and transparent security posture using the same foundation.
This integrated approach offers significant advantages over traditional methods, focusing on isolated components and static safety measures. By embracing a holistic platform developed from the same building blocks, companies can reduce time to deployment, lower costs, and optimize resource allocation, ultimately achieving comprehensive risk management and operational efficiency.
C2A Security’s Integrated Approach – Security Embedded in Every Phase
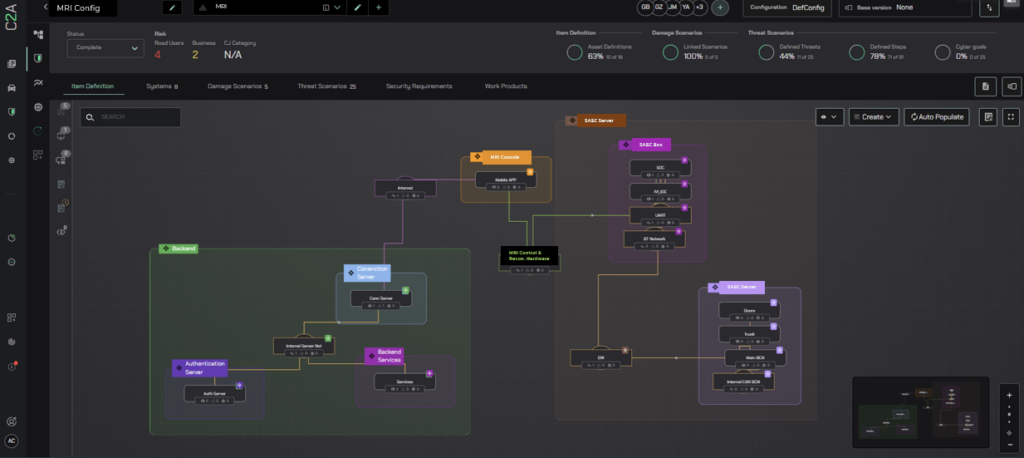
C2A Security’s risk management, compliance, and automation product security platform embodies this dynamic approach by embedding security into every phase of the product lifecycle and Standard requirements:
Dynamic Risk Management
- Scalability: Empowers with automation, reusable catalogs, and seamless integration into lifecycle security activities, ensuring efficient and scalable risk management across diverse projects.
- Automated Risk Assessment: Advanced tools identify real-time security vulnerabilities and threats, enabling swift mitigation and robust defenses against evolving risks.
- Proactive Threat Management: Ensuring resilience against potential risks by taking proactive measures to secure communication channels and safeguard functionality.
Security and Operations by Design
- Agile Product Security Development: Optimizing security controls for development teams, ensuring faster and more efficient incident response while maintaining high product quality.
- Dynamic Threat Analysis and Risk Assessment (TARA) Streamlines risk assessment and establishes a systematic, robust infrastructure, ensuring compliance with evolving regulatory standards.
Continuous Monitoring and Reporting
- Real-Time Monitoring: Continuously track cybersecurity measures across all lifecycle phases, maintaining a constant state of readiness and compliance.
- Comprehensive Reporting: Simplify regulatory audits and inspections with detailed compliance reports and risk assessments, saving time and resources while meeting all documentation requirements.
C2A Security’s EVSec Platform empowers software-defined companies to develop more secure products and shorten time-to-market.
As the only context-driven product security platform for Premarket Approval and Postmarket Surveillance, our leading DevSecOps Product Security platform leverages dynamic risk, BOM, and Vulnerability management, as well as attack path triage, to ensure targeted protection and seamless compliance for the development and operations of medical devices.
Schedule a demo today to learn more.